Your network is filled with firewalls, servers, and routers capable of detecting and log security threats.
But when a threat comes up, too many admins rely on a slow process of manually wading through tens of thousands of log entries to find and correlate a small number of log entries.
The result? Slow detection and response to serious security threats. What if there was a way to take all the information and turn it into something useful ?
SolarWinds Security Event Manager (SEM) may be the answer.
Today we’re going to thoroughly Review SolarWinds Security Event Manager!
Before we Get started, download the software below and get installed to follow along with us on the Review (its 100% free to download, no CC Required)
https://www.solarwinds.com/security-event-manager
It not only centralizes and collects logs, but it also helps correlate important events, provides advanced searching features, and even takes automatic action against threats, all in real-time.
This full range of functions is referred to as SIEM—Security Information and Event Management—and it provides a powerful way to manage events on any network.
Lets take a Deep dive into what this program can accomplish for you and your business!
SolarWinds Security Event Manager Review
Real-Time Event Correlation
SolarWinds SEM is designed to receive and process the tens of thousands of event log messages generated by network devices and servers.
Next, it uses a sophisticated matching engine to instantly correlate events, identifying potential security threats or other issues.
Events are processed in real-time and in memory, meaning they don’t need to be written to a database and then queried before the system can identify problems.
Response is incredibly fast, though obviously higher log volumes could lead to slower processing depending on how powerful your server is.
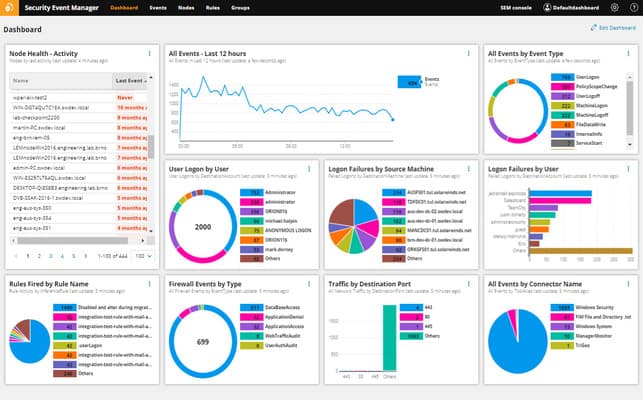
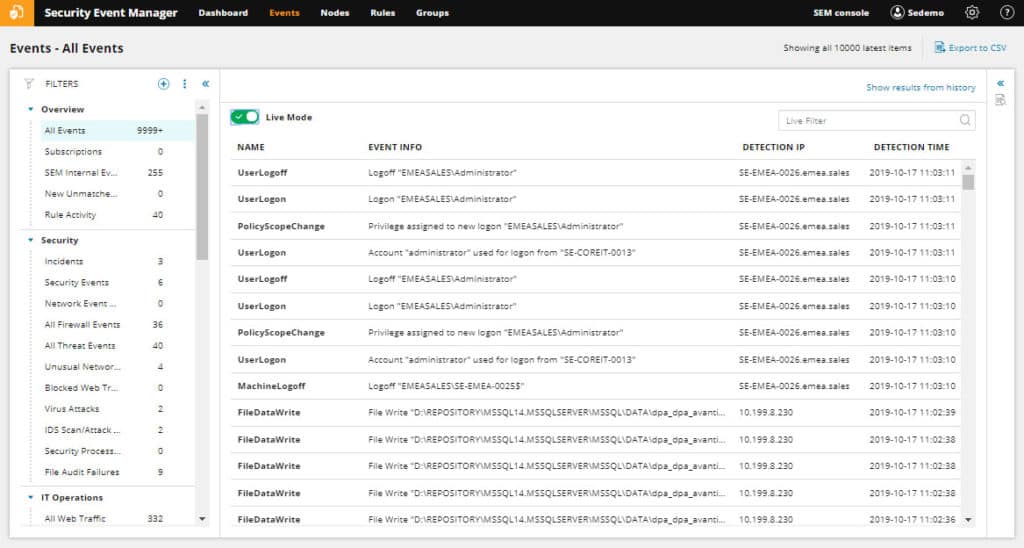
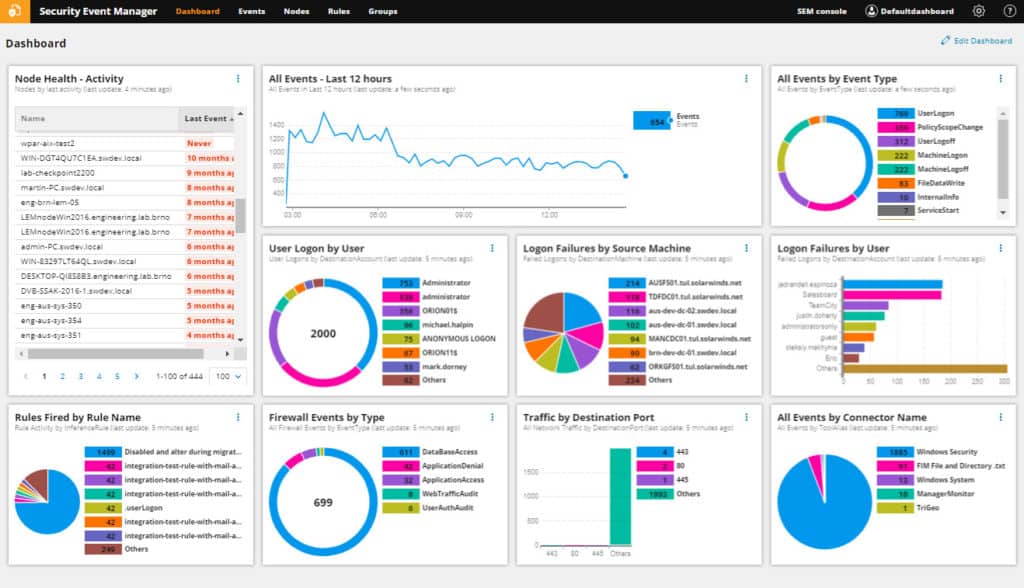
A monitoring display, like the one below, shows log data and events as they’re ingested from your devices. The Events page allows for log filtering, keyword search, and exporting of log data.
But the real power in SEM comes from its ability to automatically detect suspicious patterns in the logs and events as they stream in.
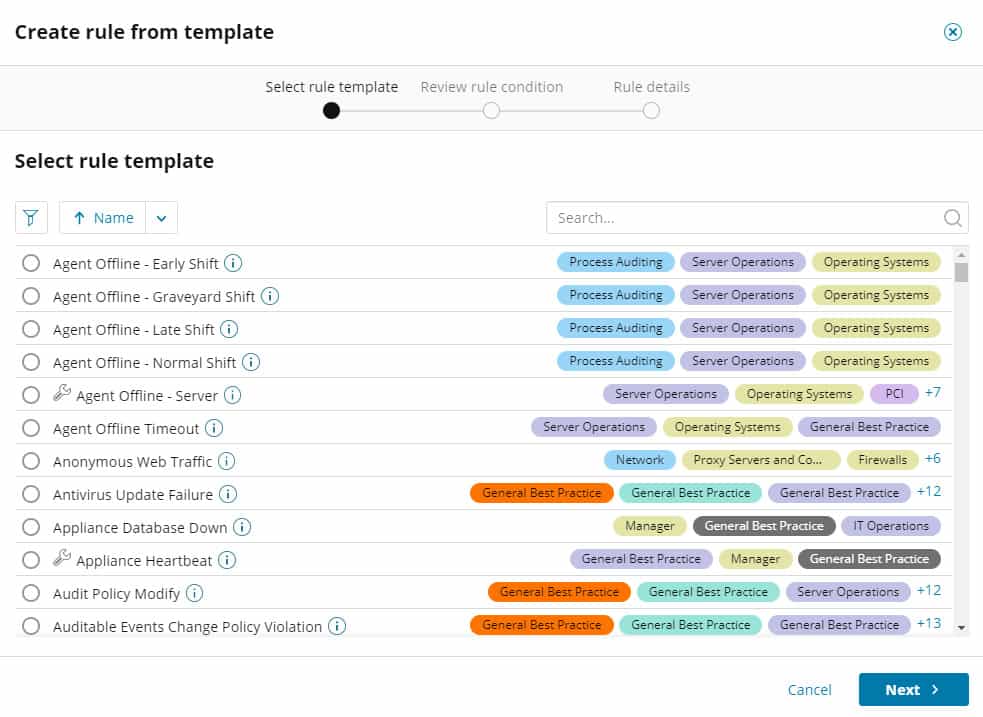
It does this using correlation rules to look for patterns matching defined conditions.
SEM ships with over 700 built-in correlation rules you can use to start monitoring the network out-of-the-box. And, SolarWinds makes it easy for admins to create new rules.
A simple graphical drag-and-drop interface allows admins to build new filters. Say goodbye to complex query languages.
Event correlation rules are flexible. Rules can be set to correlate events based on times, transactions, or even groups of events.
Thresholds can be specified for a number of events in a time period. And, variables can be set for various conditions—for example, enable rules during certain business hours, but disable them outside of business hours.
Active Response
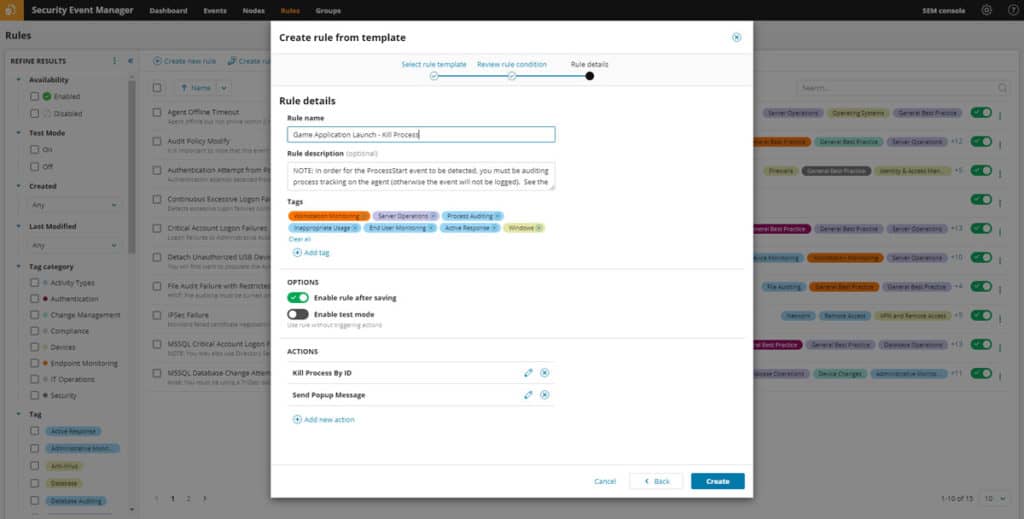
After a correlation rule has been triggered, someone needs to do something about it. SolarWinds SEM helps here by being your “someone” and automating responses to many situations.
SolarWinds calls this “Active Response,” and SEM includes a large library of possible responses to common situations. You can automate actions like:
- Quarantine infected machines, or force shutdowns and restarts
- Block IP addresses
- Disable user accounts
- Kill processes
- Restart or stop services
- Force user log-off
- Reset passwords
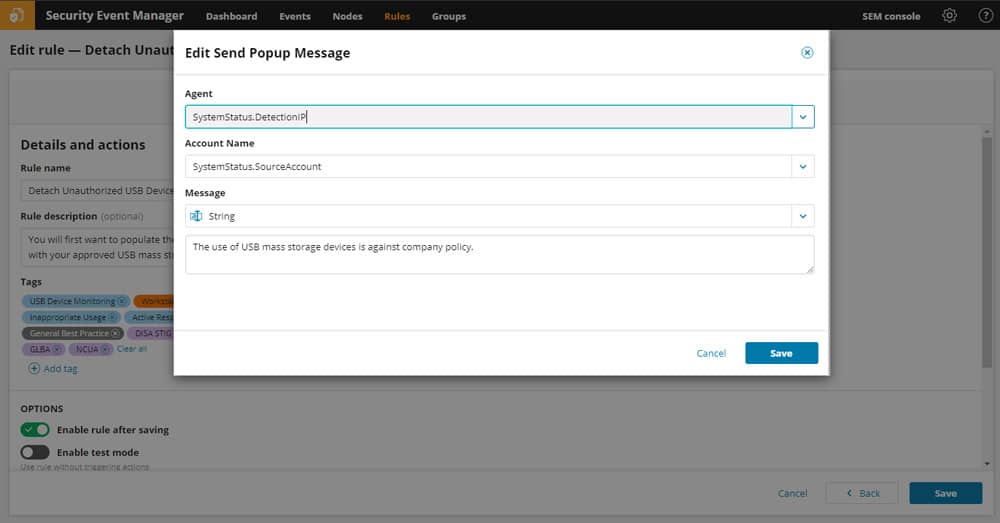
Rogue USB Data Loss & Theft Protection
Some companies are concerned about large-scale Data Loss and Theft from USB devices.
Active Response can help manage data access via USB devices. SEM can identify unauthorized access and copying of sensitive files, and enable actions like automatic ejection of USB devices, or quarantine of workstations using USB devices.
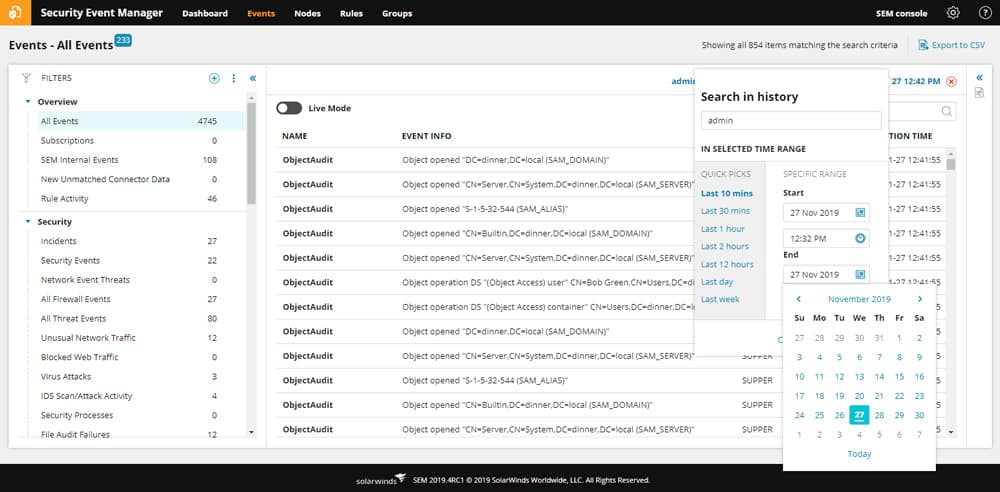
Advanced Search Features
Have you ever tried to mine through a huge log database?
It can be hard to find what you’re looking for, and it can be slow to query databases for different event types and IP addresses.
SEM takes search to a new level with visual search and forensic tools.
The dashboard provides a quick way to easily identify patterns and then drill into the specific logs associated with the suspicious activity.
Additional filters and time-based searching can help refine the exact logs you look at. Raw data can be easily exported and ready for further analysis using other tools.
Reporting
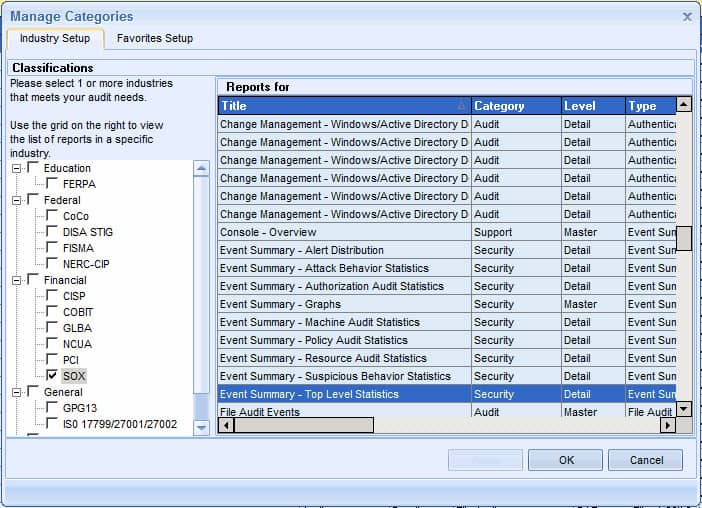
SolarWinds has included a powerful reporting engine with Security Event Manager. Over 300 built-in reports can help with everything from graphical summaries of activity, to detailed threat reporting and compliance.
Speaking of compliance, many of the reports are designed to show your organization’s compliance with standards and legislation like PCI DSS, Sarbanes-Oxley, HIPAA, and others.
And, reports can be customized to meet specific needs.
Reports can be scheduled to run at pre-determined intervals. It’s a great idea for large reports you need regularly, since scheduling a report to run at night frees up daytime processing power for other needs.
Easy Installation
SEM is deployed as a virtual appliance.
In theory, installation is as simple as downloading the VMware or Hyper-V file and loading it up.
SolarWinds likes to refer to this as “live by lunch” installation, since database and web server configuration is eliminated.
In practice, it’s a little more complex. If you don’t already have VMware or Hyper-V running in your environment, then you’ll need to set those up first.
Fortunately, the installer is helpful and includes links to the free VMware ESXi platform. A desktop software package is also required to set up various reporting components.
On the downside, there’s no Windows installer version of SEM, which removes some flexibility. The only option is to use the virtual appliance.
Most organizations looking at a product like this will already be using virtualization technology, so in reality this isn’t much of a limitation.In addition, they offer the ability to deploy the appliance in a public cloud, such as Azure or AWS.
The other component required: Agents.
Agents are needed for systems that don’t support SNMP/Syslog, and to enable some of the more advanced features of the product.
Agents add key functionality, and you’ll definitely want them.
But, successfully installing agents on hundreds or thousands of machines can be an enormous task, even if using automated tools.
However, SEM does come with a Remote Windows Installer so you can deploy the agent to many machines remotely, helping with this task.
Pricing
The pricing model is notable because it’s based on the number of nodes being monitored, as opposed to some software priced based on volume of log data.
A huge number of factors can influence the amount of data generated—number of devices on the network, types of events, virus outbreaks—the list goes on and on. It can be hard to estimate how much log volume to expect.
SolarWinds has a good solution to provide some certainty around licensing costs. They license by node, providing a predicable cost-model without requiring administrators to try to estimate log volume.
Security Event Manager pricing starts at US$4,665 to monitor 30 nodes.
Summary
Security Event Manager is a very cool tool. It blends log management with security incident response, delivering a well-priced, versatile, and easy-to-use product.
Features like Active Response and the dashboard will help to manage threats and make it easier for administrators to understand what’s happening on the network.
The VM-Appliance style of install makes it easy to get up and running quickly.
Bonus Integrations
And, as a nice bonus for users of other SolarWinds products, SEM integrates with SolarWinds software like Network Performance Monitor and Server & Application Monitor.
Integration allows the ability to send syslog messages to and from the other apps.
On the other hand, having the tool available as a VM-only install (even with the option to deploy in Azure or AWS) removes some flexibility.
And the need to install agents adds complexity and increases the work involved in a large deployment.
But overall, the great UI design and rich feature-set of SEM won us over. Security Event Manager is sure to fill a niche many businesses are missing.
Try it out yourself with a free 30-day trial download.
If you don’t have a log and security response product like this, you’ll be amazed at what you’ve been missing.
We hope this Review of SolarWinds Security Event Manager has covered many of the topics and questions you may have regarding finding a SEIM product to deploy in your environment!
Download a FREE 30 Day Trial to get Started Immediately!
Product: SolarWinds Security Event Manager
Review Date:
Rating: 4.9
Pros:
- Easy to deploy VMWare or Hyper-V appliance
- Track, monitor, and respond to network-wide security events
- Competitively Priced
Cons:
- No traditional Windows install available – virtual appliance only
- Requires end-point agents in some cases
SolarWinds Security Event Manager FAQs
What features does SolarWinds Security Event Manager offer?
SolarWinds Security Event Manager offers features such as real-time event correlation and analysis, log management and archiving, threat intelligence and vulnerability scanning, user activity monitoring, and compliance management.
How does SolarWinds Security Event Manager work?
SolarWinds Security Event Manager works by collecting and analyzing security event data from various sources, including logs, network traffic, and system activity, to identify potential security threats and vulnerabilities.
What types of security events can SolarWinds Security Event Manager monitor?
SolarWinds Security Event Manager can monitor various types of security events, including network traffic, system activity, user activity, application activity, and security policy violations.
What are some common use cases for SolarWinds Security Event Manager?
Common use cases for SolarWinds Security Event Manager include threat detection and response, incident investigation and forensics, compliance management, and performance optimization.
Can SolarWinds Security Event Manager be used for compliance management?
Yes, SolarWinds Security Event Manager can be used for compliance management, by providing real-time visibility into security events and automating compliance tasks.
What are some common security threats that SolarWinds Security Event Manager can help detect and prevent?
Common security threats that SolarWinds Security Event Manager can help detect and prevent include malware and viruses, network intrusions, phishing attacks, and insider threats.
How does SolarWinds Security Event Manager help with threat detection and response?
SolarWinds Security Event Manager helps with threat detection and response by providing real-time alerts and automated responses to potential security threats, and by providing tools for incident investigation and forensics.
Can SolarWinds Security Event Manager be integrated with other security tools and software?
Yes, SolarWinds Security Event Manager can be integrated with other security tools and software, such as firewalls, antivirus software, and intrusion detection and prevention systems, to provide a more comprehensive security solution.