Troubleshooting is one of the most difficult aspects of an application or system. Many times, it is a wild goose chase until you know where the problem is and its cause. This is where log files come in handy as they point you in the right direction, so you are more productive, efficient, and quick in solving problems. In particular, the Windows event logs are a handy tool to identify and troubleshoot issues.
What are Event Logs?
The Windows event log is a comprehensive and detailed record of all notifications generated by the Windows operating system. This includes system, security, and application notifications, errors, information, warnings, and more.
These event logs are highly useful for understanding the working of the operating system as well as the applications that run on it and using this information, you can quickly troubleshoot issues. You can diagnose the root cause easily and work towards addressing the problem. A related advantage is that such notifications help you to proactively predict future issues and prepare for the same.
Where to Find Event Logs?
The event logs are located by default in System32/Config folder and they have a .evt extension.
You can always move these files to a different location, but it is not as simple as copying and pasting because the log file name and the related location information are stored in the registry.
So, what should you do if you want to change the location of event logs? Simply follow the below steps.
- Click the Start menu and Run. Type “Regedit” and click OK
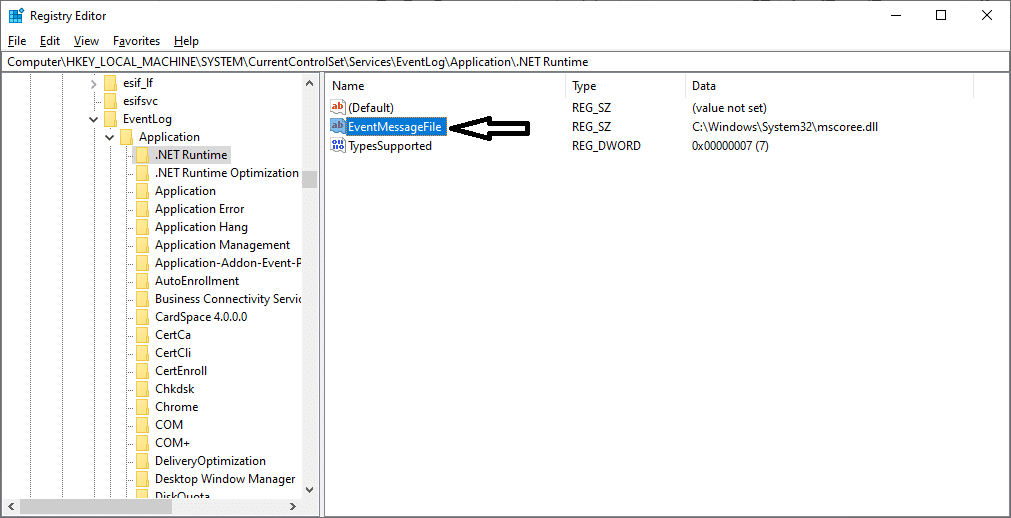
- On the left-hand pane, look for this registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Eventlog.
- Navigate to the specific event log that you want to move such as Application, Security, System, etc.
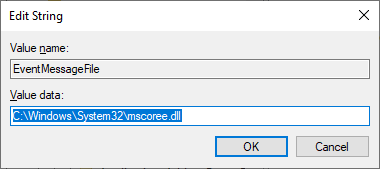
- On the right-hand pane, double-click on the EventMessageFile
- Under the “Value Data” field, type the new location.
- Repeat these steps for all the log files and finally, exit the Registry. The changes will be automatically saved.
- Lastly, restart your computer
From now on, the log files will be located in the new location.
Types of Event Logs
Your operating system handles many types of events and it has to send notifications and alerts accordingly. Putting all the information in the same log file can make it difficult for you to find information about different event categories.
This is why there are event logs for different categories and let’s look at the most important types of event logs now.
- Application Event Log This log file contains events that are caused by programs/applications that run on your system. What events get written on the log file is determined by the programmer/developer who has written the code for this application. Every application installed in your system will have a separate application event log.
- Security Event Log The security event log file contains security-related events such as the number of successful and failed logins, resource usage, remote connections, and more. You can change what events are recorded in this log file but must be logged in as a user with admin rights.
- Systems Event Log This log file contains events that are triggered by Windows service components and this list is determined by the Windows operating system.
- Directory Service Log The Directory Service Log file contains Active Directory (AD) related events and you can see this file only on systems that act as domain controllers.
- DNS Server Log This log file is located on DNS servers only and as you may have guessed, will contain events related to the resolution of DNS names.
There are many more log files, but these are the most prominent and commonly-used ones.
Now that you have an idea of what event log files and their types, let’s see how you can forward them from one system to another, and the rationale behind this process.
Event Log Forwarding
The Windows operating system allows it to be forwarded from one host to another. This can be a big advantage when you have to manage multiple systems within a network. You can configure all the event logs to be forwarded to a centralized system, so you can easily monitor them and more importantly, take the necessary proactive steps to prevent major failures.
All these forwarded events are stored in a file called Forwarded Events Log.
In this article, let’s see how you can configure systems to send their event logs to a centralized system, where to access this centralized log file, how to glean information from it, and what are some of the third-party tools that you can use to save time and effort.
Let’s start with the configuration.
Configuring Systems to Forward and Receive Event Logs
The Windows operating system automatically generates the event logs, so no additional effort is required from your end for the same. However, you must set up the source computers to forward event logs to a central system.
To do this, open your command prompt with admin permissions and execute the following command.
C:\> winrm quickconfig
Also, add the receiving computer to the local Administrators group of each source computer. This should allow the source computers to forward their event logs to the centralized computer.
Now, moving on to the centralized computer, you must configure this to receive event logs. Again, open your command prompt with admin privileges and enter the following command.
C:\> wecutil qc
Change Subscription Properties
After you add those configurations, change the subscription properties so your computers know what events are being collected by the receiver. To do this, follow the below steps.
- Log in to the device with administrator privileges and open the Event Viewer app. The easiest way is to right-click on Windows and search for it.
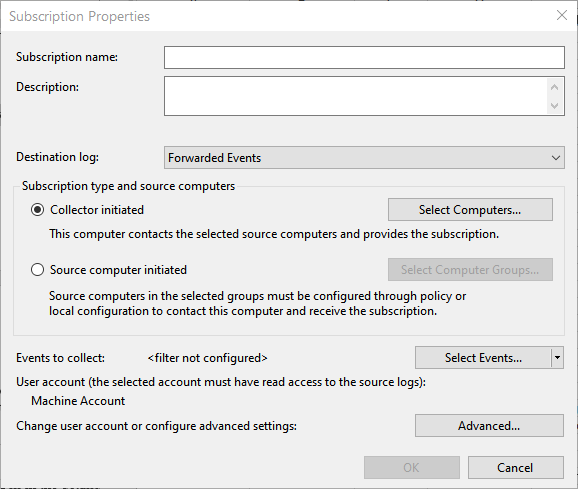
- On the left-hand pane, look for an option called Subscriptions and click it.
- On the rightmost pane, look for an option called “Create Subscription” and click that.
- This will open a new window called subscription properties and in that, select the collector or receiving computer and the events you want the source system to forward.
Once you set up these properties, the source computer will automatically forward log events to the receiving computer.
Moving on, let’s look at some third-party tools that can ease the process of event log forwarding. These tools are particularly useful for those who are not tech-savvy or those who want to spend less time managing multiple accounts.
Event Log Forwarding Tools
Our methodology for selecting event log forwarding tools and software
We reviewed various event log forwarding tools and analyzed the options based on the following criteria:
- Support for a wide range of environments, applications, and operating systems
- Robust search function to parse large amounts of data
- Ability to handle large volumes of data
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
Some of the well-known tools for event log forwarding are:
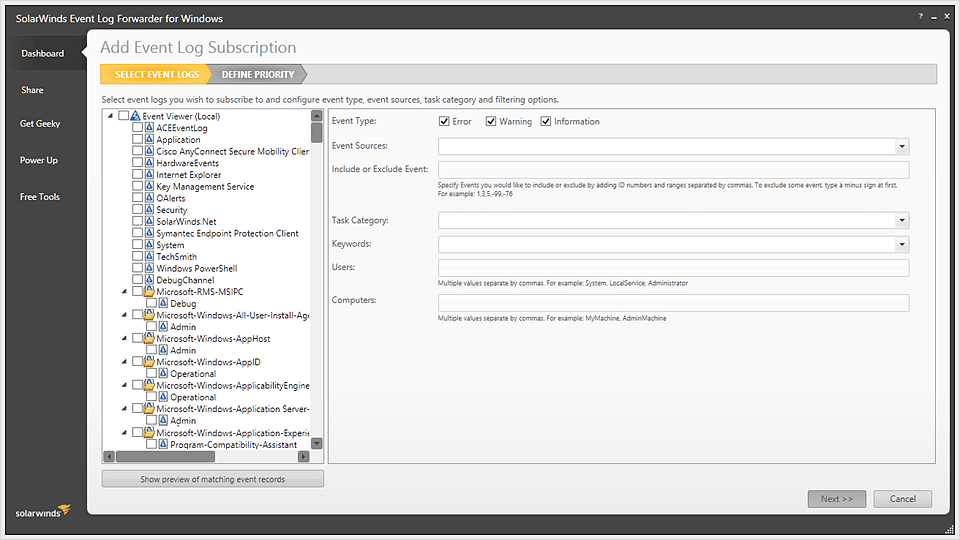
- SolarWinds Event Log Forwarder – FREE TOOL This free tool from SolarWinds forwards events to Syslog services. You can even filter these events based on a host of parameters to forward just the information you want.
- ManageEngine Log360 Cloud – FREE TRIAL streamlines log forwarding with helpful templates, granular log filtering, and intelligent alerts to stop threats quickly.
- Kiwi Syslog This is an advanced tool that centralizes and simplifies log forwarding and management.
- Netwrix Event Log Manager This freeware tool collects event logs from computers in your network, analyzes them, and sends alerts in real-time.
1. SolarWinds Event Log Forwarder – FREE TOOL
This event log forwarder from SolarWinds automatically forwards Windows event logs to any Syslog service. You can also use this tool to forward specific Windows events identified by their event ID, users, keywords, source, and more.
Key Features:
Below are some of the salient features of SolarWinds Event Log Forwarder.
- Automatically sends events from servers and workstations
- Exports event data from Windows systems.
- Sends events to multiple servers via UDP and TCP
- Alerts, stores, and audits activities
- Filters events to collect only the information you need
Why do we recommend it?
The SolarWinds Event Log Forwarder is an efficient free tool that enables you to consolidate logs by converting them into the Syslog format and sending them on to another location, which you would set up as your Syslog server. The tool can filter messages before forwarding and also send them to external destinations.
Who is it recommended for?
This is a free tool so there is no cost bar to using it. The package is ideal for network managers that want to construct a log management system. There are log managers available that include a forwarder component but many log management packages are basically servers that will only receive either Syslog or Event logs.
Pros:
- Completely free
- Captures both syslog and SNMP traps, ensuring nothing is missed
- Interface is easy to use, and allows for quick filtering based on application, location, or custom grouping
- Color-coded warning level helps critical events pop out, and aids in prioritization
- Affordable for any size network
Cons:
- Built for sysadmins, not the best option for home networks or non-technical users
Pricing: 100% FREE.
EDITOR'S CHOICE
SolarWinds Event Log Forwarder is our top pick for an event log forwarding system because it is a free tool but it has the backing of a high-end brand. The service can send Event Log messages from servers and workstations on to other systems or to files. The tool doesn’t convert the format of the messages but it will tag metadata to each record so the receiver can identify where each message came from and which operating system or software package generated it. The tool can also filter messages to remove low status notifications.
Download: Download Free Tool
Official Site: https://www.solarwinds.com/free-tools/event-log-forwarder-for-windows
OS: Windows Server
2. ManageEngine Log360 Cloud – FREE TRIAL
ManageEngine Log360 Cloud is a comprehensive cloud-based SIEM solution designed to help organizations secure their cloud environments. It offers several features that enable administrators to detect and respond to security threats quickly and efficiently.
Key Features:
- Real-time threat protection
- Advanced filtering options
- Templated reports, dashboards, and setup
Why do we recommend it?
ManageEngine Log360 Cloud is a SaaS option for a log management and SIEM system. The package is also available for self hosting. This is a large package that will gather both Syslog and Event logs and convert them to a common format. It can collect messages from cloud platforms as well.
Log360 Cloud also offers advanced threat detection capabilities, such as anomaly detection and behavioral analysis. These features enable administrators to identify suspicious activities and take corrective actions before an attack occurs. Log360 Cloud provides real-time alerts, reports, and dashboards that give administrators a complete view of their cloud security posture.
Log360 Cloud also offers predefined compliance reports for various regulatory standards, such as PCI DSS, HIPAA, and GDPR. These reports help administrators demonstrate compliance and avoid potential legal and financial penalties.
Who is it recommended for?
This package is designed for use by large organizations because it can collect log messages from many different sources in large volumes. The package will consolidate logs written in different formats so that they can be stored together, this is like a centralized forwarder. The package also includes a SIEM for security scanning.
Pros:
- Great dashboard visualizations, ideal for NOCs and MSPs
- Can integrate multiple threat data steams into the platform
- Offers robust searching of logs for live and historical event analysis
- Provides monitoring cross-platform for Windows, Linux, and Unix systems
- Can monitor configuration changes, preventing privilege escalation
Cons:
- ManageEngine offers a suite of advanced services and features can time to explore and test out
ManageEngine Log360 Cloud offers a 30-day free trial to test the software’s capabilities in your environment before buying
3. Kiwi Syslog
Kiwi Syslog from SolarWinds is an advanced tool that enables you to centralize log management and simplify the process of event log forwarding from one device to another.
Key Features:
Let’s now take a detailed look at the features of this tool.
- Centralized Management Managing the logs of a bunch of computers in your network can quickly get out of control. Also, managing them on a system-by-system basis may not always be practical. This is where Kiwi Syslog can come in handy. It brings all the event logs together on a single console, so you can quickly find the information you want.
- Real-time Alerts Kiwi Syslog sends real-time alerts based on Syslog messages and SNMP traps. It can receive them from UNIX, Linux, and Windows systems and analyze them for possible threats. These alerts can be a game-changer when it comes to identifying and mitigating security threats.
- Automatic Response You can set up Kiwi Syslog to automatically respond to certain messages in a particular way. Based on the message, you can set up Kiwi Syslog to trigger emails, run scripts, forward messages, and any other custom action.
- Meets Regulatory Compliance Some industry standards such as HIPAA and PCI DSS require you to archive log messages for a certain period. Kiwi Syslog automatically cleans the logs and archives them to help your business to comply with these standards. Similarly, it also handles the necessary documentation required for compliance and internal audits.
- Filtering and Buffering With Kiwi Syslog, you can filter any message by hostname, IP address, and timestamp to quickly find the information you want. Also, you can buffer up to 10 million messages and 1,000 emails to handle heavy loads easily.
- Log Forwarding Kiwi Syslog allows you to forward event logs to multiple servers using UDP or TCP, as the case may be. You can even specify the events that must be forwarded based on type and keywords. As you can see, Kiwi Syslog can be a handy tool for managing all your log events in a single place, so you can make better use of them for troubleshooting and for predicting future events.
Why do we recommend it?
The Kiwi Syslog server collects Windows Events and SNMP Traps as well as Syslog messages. You can choose to file the Event messages or insert them into a database. This gives you an opportunity to convert the messages into another format and even send them on to other servers.
Who is it recommended for?
This is a very flexible tool because it doesn’t just enable you to forward Windows Events, you can also convert and send Sylog messages to other servers or merge messages from different formats into one stream and send them on to a SIEM tool for analysis.
Pros:
- Offers a freeware version for smaller networks
- Captures both syslog and SNMP traps, ensuring nothing is missed
- Interface is easy to use, and allows for quick filtering based on application, location, or custom grouping
- Color-coded warning level helps critical events pop out, and aids in prioritization
- Affordable for any size network
Cons:
- Built for sysadmins, not the best option for home networks or non-technical users
Pricing: Kiwi Syslog costs $329 per installation and this is a perpetual license, so there are no monthly/yearly payments to track. Click here to try it for free for 14 days.
4. Netwrix Event Log Manager
Netwrix Event Log Manager collects messages from different sources, consolidates them, and archives event logs for compliance.
Key Features:
Here’s a brief look at Netwrix Event Log Manager’s features.
- Consolidates all events in a central location for better visibility and management.
- Sends notifications about critical events.
- Stores logs for further analysis and to meet compliance requirements.
- Automates the process of log collection and monitoring.
Why do we recommend it?
Netwrix Event Log Manager is a consolidator that can collect Syslog messages as well as Windows Event logs. This tool is part of Netwrix Auditor, which is a system-wide log management utility for compliance reporting. The software for this system installs on Windows Server.
Who is it recommended for?
This tool is intended for use to collect, store, and analyze Windows Event messages but you could also use it to forward those messages elsewhere. The main audience for Netwrix Auditor is with companies that need to comply with SOX, HIPAA, and PCI DSS.
Pros:
- Forwards and categorizes events in just a few clicks
- Offers hardware and device monitoring to track device health alongside security
- Allows sysadmin to implement automated remediation via scripts
- Integrates with popular help desk platforms for automatic ticket creation
Cons:
- The trial could be a bit longer
Pricing: 100% FREE. Click here to download this freeware.
These are some of the event log forwarding tools that can make this process easier and more effective for you.
Conclusion
To conclude, logs are an important part of your overall network as they act as a gateway to the health and performance of your devices. Windows will automatically capture different events and will log them in their respective files.
As a user, you can always forward these event logs to a central computer, so you can filter, search, analyze, and manage them better. But manually setting up the configurations can be difficult, especially if there are many computers in your network.
This is where third-party tools like Kiwi Syslog and SolarWinds Event Log Forwarder come in handy. We hope the brief description of these different tools gives you an idea of what they can do for your organization, so you can choose accordingly.
If this was interesting, you can always browse through our other guides!
Event Log Forwarding FAQs
How does event log forwarding work?
Event log forwarding works by configuring a source computer to forward its event logs to a destination computer or collector. The destination computer collects the forwarded event logs and stores them in a central location for analysis.
What are the benefits of event log forwarding?
Event log forwarding provides several benefits, including centralized monitoring and analysis of event logs, reduced administrative overhead, and improved security and compliance.
How can I configure event log forwarding?
You can configure event log forwarding using the Event Viewer or Group Policy. In the Event Viewer, you can right-click on the event log you want to forward and select "Properties" to configure forwarding. In Group Policy, you can configure forwarding settings for all computers in a domain or organizational unit. Alternatively, you can use tools like SolarWinds Event Log Forwarder to simplify this process.
What are the requirements for event log forwarding?
To use event log forwarding, you need to have a central computer or collector that is running Windows Server 2008 or later. You also need to have administrative access to the source and destination computers.
How can I troubleshoot issues with event log forwarding?
If you are experiencing issues with event log forwarding, you can use the Event Viewer or Group Policy to check the configuration settings. You can also check the event logs on the source and destination computers for errors or warnings related to event log forwarding.
What is the difference between event log forwarding and event log replication?
Event log forwarding and event log replication are similar in that they both involve collecting event logs from multiple computers in a central location. However, event log replication uses a pull-based model, where the destination computer retrieves event logs from the source computer, while event log forwarding uses a push-based model, where the source computer forwards event logs to the destination computer.
What are some best practices for event log forwarding?
Some best practices for event log forwarding include defining clear goals and requirements, testing the configuration before deployment, regularly reviewing event log data, and using event log data to drive continuous improvement.