Do you know that 60% of data breaches are insider threats? Also, the average cost of each of these threats is a whopping $11.5 million. These numbers clearly show the widespread prevalence of these thefts and the huge impact it has on an organization. More importantly, these high numbers emanate from the fact that these threats are hard to identify and mitigate.
Typically, insider threats are done by employees who have legitimate access to sensitive information. They tend to steal this information and sell it to others for money or use it to settle a grudge against the organization itself. Regardless of the reason, an organization must take the necessary steps to protect its assets from insider attacks.
One such strategy is USB port locking.
Here is our list of the best USB port locking tools:
- ThreatLocker Storage Control – EDITOR’S CHOICE This management system for USB devices and the USB ports of computers locks all ports and then selectively allows authorized devices to connect. Get a free demo account.
- ManageEngine Device Control – FREE TRIAL This is a comprehensive device control and file access management solution that prevents anyone from moving sensitive files to any peripheral devices. Start a 30-day free trial.
- SysTools USB Blocker This tool quickly blocks or unblocks USB devices on multiple computers at the same time. It comes with many advanced features and works well on Windows 7,8,8.1, and 10.
- Endpoint Protector Device Control An all-encompassing platform that monitors and locks down your USB and peripheral ports. Also, it provides complete control and visibility into the usage of these ports.
- GiliSoft USB Lock This data leak prevention tool locks your USB ports and prevents anyone from copying data to USB drives, CDs, and other portable devices. It works only on Windows devices.
- USB Disk Manager A small Windows utility that prevents systems from reading or writing to a USB drive.
So, how do you know if any of the above tools are appropriate for your business needs?
Well, it all starts with research where you understand each tool’s detailed features, so you can determine the best fit. To ease your efforts, we have done the hard work, so sit back and read through the detailed feature list of each tool.
What is USB Port Locking?
Many times, employees prefer to download important documents to a USB flash drive because it’s easy to carry. Also, it’s hard for an organization to know that some files have been copied to a flash drive. Due to these reasons, an employee can get away with this stealthy act.
The good news for organizations is that there is USB port locking software that prevents anyone from copying files to a USB drive. This acts as a deterrent for employees with privileged access to steal sensitive information.
Another advantage of this software is that it prevents employees from infecting computers with malware, ransomware, or other malicious software through a USB flash drive.
Due to these security advantages, organizations increasingly prefer to use USB port locking software to prevent any form of an insider attack.
The Best USB Port Locking Tools
Our methodology for selecting port locking tools and software
We reviewed various port locking tools and analyzed the options based on the following criteria:
- Ability to lock and unlock USB ports quickly and effectively
- Support for locking down other media, such as CD drive and Bluetooth
- Graphical interpretation of data, such as charts and graphs
- Free trial period, a demo, or a money-back guarantee for no-risk assessment
- Good price that reflects value for money when compared to the functions offered
1. ThreatLocker Storage Control – GET DEMO
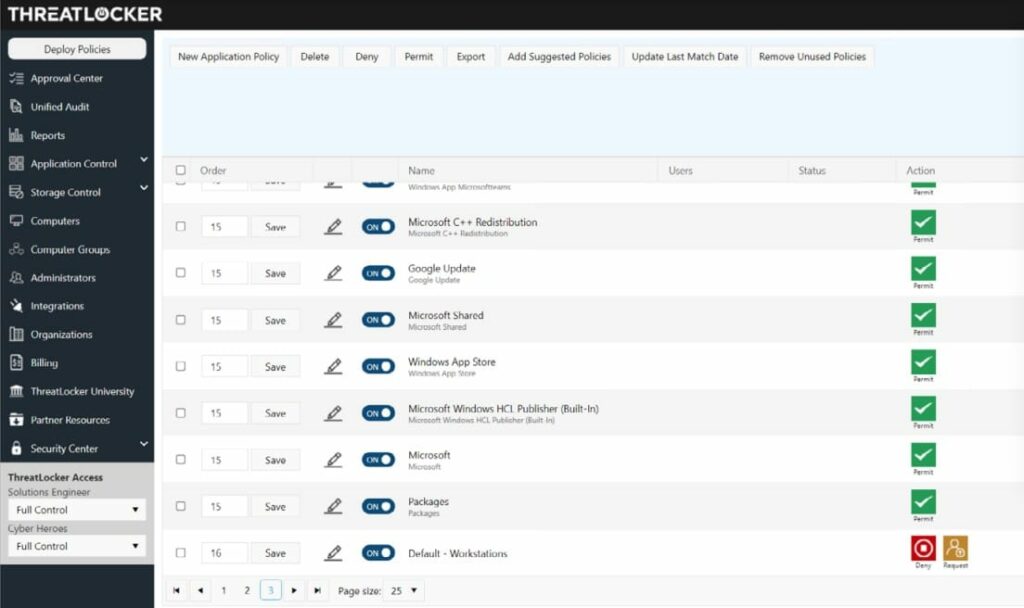
ThreatLocker Storage Control provides a method to manage all peripheral devices that can connect to a computer through a USB port. The ThreatLocker system monitors all of the endpoints on a protected network and all of the USB ports on each. The system starts by blocking all ports and then allowing an administrator to make some ports active for specific USB devices.
Key Features:
- Security Policy Creation Every business needs to have a company-wide security policy, which dictates who can access which resources. One of the features of the ThreatLocker system is a section that lets the administrator formulate a security policy that applies to all access rights for each user. The Storage Control module implements one part of the security policy. The console provides an access rights manager (ARM) that maps permissions for a user to use a software package to access a specific resource, such as a file folder or a USB storage device.
- USB Port Controls Manages all of the USB ports of all of the computers on a business’s network. The tool starts off with the policy of blocking all USB ports by default. The system administrator can then set up a permission structure for each port and specify USB devices that are allowed to attach to each computer. Users can also initiate the authorization of a device by inserting it into a port. Although all ports are blocked, they are still able to communicate with the central console of ThreatLocker. The insertion of a device provokes a notification in the console and the systems administrator has the option of approving it or leaving the block in place.
- Activity Logging Logs all actions related to file access and file movements. So, if an authorized user is allowed to move a file onto a USB storage device, that event will be recorded. The log record includes the identity of the user, the file that was moved, the direction of the movement, the device it was moved or copied to, and the date and time of the event. These logs are stored and will be compiled into compliance reporting and can also be used to trace the source of disclosure if the file movement is later discovered to have been ill-advised.
Why do we recommend it?
ThreatLocker Storage Control includes USB management in its remit and it also covers network shares and even folders. The system prevents all USB devices from attaching and then a user inserting a USB gets a notification that presents a brief window in which to request approval for the device.
Who is it recommended for?
This system is suitable for use by any company. Data theft isn’t just an issue for businesses that manage sensitive data. You also don’t want employees walking off with your client list or intellectual property. There are many types of trade secrets that can be stolen with a USB stick.
Pros:
- Blocks all USB devices by default
- Authorization identifies each USB device by serial number
- Approve a USB stick for a computer, for a user, or a combination of both
- Option to approve a USB device for system-wide use
- Works on Windows and macOS
Cons:
- Doesn’t operate on computers running Linux
Threat Locker doesn’t publish a price list. Click here to get access to a free demo account.
EDITOR'S CHOICE
ThreatLocker is our top pick for a USB port locking tool because it shuts down all USB ports by default, so there is no danger of a system administrator oversight resulting in ruinous data theft. Instead, the worst that can happen is that some workers will be temporarily inconvenienced. However, the ThreatLocker system has a mechanism that caters to the occurrence of block processes: inserting a USB provokes a pop-up through which the user can make an urgent request to the administrator.
Download: Get a 30-day free trial
Official Site: https://www.threatlocker.com/try-threatlocker
OS: Windows and macOS
2. ManageEngine Device Control – FREE TRIAL
ManageEngine Device Control is advanced software that prevents anyone from copying data to peripheral devices. It’s a simple and highly effective tool to prevent any insider attack or data loss.
Key Features:
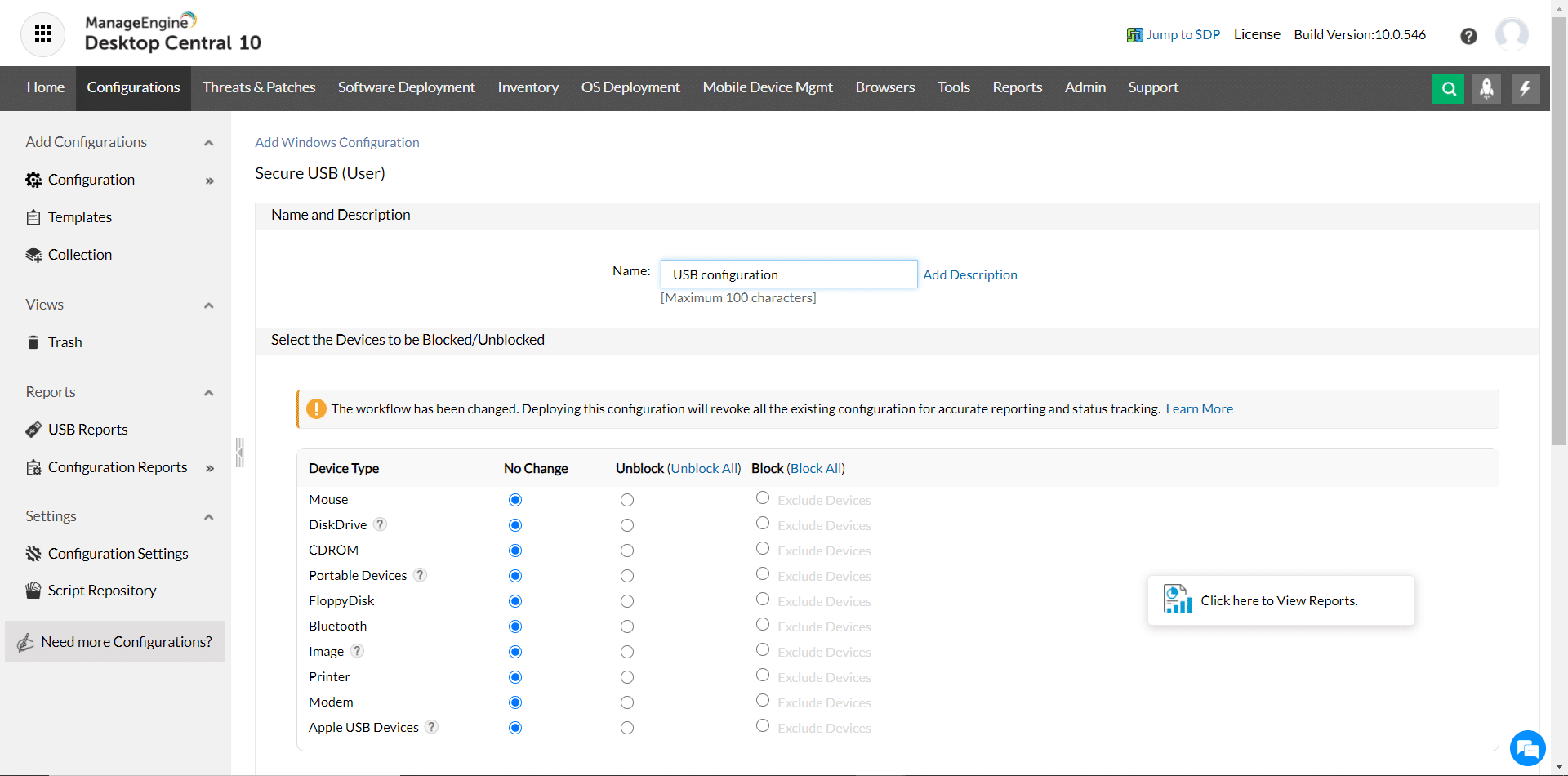
- Comprehensive Control Provides comprehensive control over all ports and removable devices. It follows a zero-trust security model, so every time a user logs into a device or uses its USB ports, this information is logged in the audit section. Admins are also alerted during such attempts, and all these can deter employees from copying sensitive information to peripheral devices. You can also use this tool to create a trusted device access list. Any device that’s not a part of this list can’t access the USB port. Further, it creates a layer between computers and removable devices, so no malware can impact your network.
- Streamlines File Access Device Control streamlines file access by encouraging you to set certain parameters. For example, you can implement a strict role-based access policy to allow readers only to read a file and not copy them to devices. Similarly, you can set the maximum file size that can be downloaded. This is an advantage because most times, sensitive information is grouped and stored in a master file. Above everything, this tool allows you to monitor file usage and actions as they happen, so you can always stay on top of insider attacks.
- Generates Reports Device Control logs every file activity. It also maintains a record of devices and computers and users that access them. Since every information/activity is logged, you can generate reports at any time for internal viewing and auditing. Further, you can also use it to comply with industry standards. Thus, these are some of the important features of ManageEngine Device Control. In all, this is a comprehensive tool that provides complete control over file access and usage. Plus, the fact that it logs every access and login acts as a big deterrent for employees looking to commit insider thefts.
Why do we recommend it?
ManageEngine Device Control provides USB device management as part of its Endpoint Central package. Until recently, this tool was called Desktop Central, which explains the title in the image at the top of this review. This system recognizes that USB ports and be used to connect many types of devices, not just memory sticks.
Who is it recommended for?
This unit is part of a package that provides remote monitoring and management tools for endpoints. The highest plan for the system is a unified endpoint management system that includes mobile device management. There is also a Security edition that includes data loss prevention. The package is intended for use by IT departments.
Pros:
- Designed to work right away, features over 200 customizable widgets to build unique dashboards and reports
- Leverages autodiscovery to find, inventory, and map new devices
- Uses intelligent alerting to reduce false positives and eliminate alert fatigue across larger networks
- Supports email, SMS, and webhook for numerous alerting channels
- Integrates well in the ManageEngine ecosystem with their other products
Cons:
- Is a feature-rich tool that will require a time investment to properly learn
Click here for a free trial version.
3. SysTools USB Blocker
SysTools USB Blocker is a simple tool that blocks and unblocks USB ports from any machine/user. It comes with many features that allow you to block or unblock multiple systems simultaneously.
Key Features:
- Blocks and Unblocks USB Ports Makes it easy to quickly block or unblock USB ports, preventing users from using peripheral devices such as USB, flash, and pen drives to copy sensitive information from a computer. But what happens if someone has to copy files for other tasks. In such genuine cases, the admin can unblock the USB ports to provide access to these peripheral devices. With SysTool USB Blocker, both the above tasks are simple and quick.
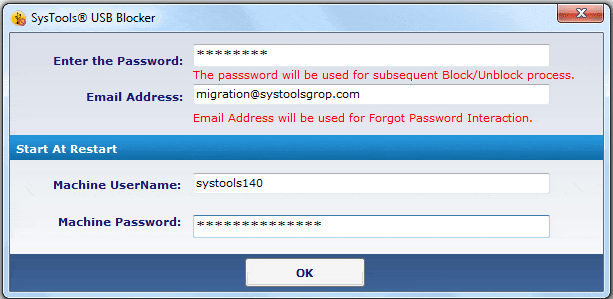
- Works on Multiple Machines A salient feature of this tool is that you can use it to block or unblock any number of USB ports spread across multiple machines. However, you’ll have to install this tool on all the machines you want to control. Furthermore, you must set the machine and user password and have to use the same credentials for both blocking and unblocking.
- Highly Interactive USB Blocker has a rich and interactive user interface. The obvious advantage of this tool is that it can be used by people of all skill levels. It’s highly intuitive and requires no prior knowledge or experience either. Due to these features, SysTools USB Blocker is highly user-friendly for people of all technical levels.
- Windows OS Works only on Windows operating systems. It’s compatible with Vista, ME, NT, XP, Win 7, Win 8, Win 8.1, and Windows 10. It also works well on Windows 2000, 2003, and 2008. On all the Windows systems, it requires a minimum of 5MB of hard disk space, 1GB of RAM, and a 2.4GHz processor. Overall, SysTools is a simple and convenient tool to block and unblock USB ports. Its user interface is a huge plus, but the downside is that it doesn’t work on non-Windows computers.
Why do we recommend it?
SysTools USB Blocker is an affordable and straightforward USB port blocker with bulk license purchase discounts. The system identifies the administrator by email address and password. Without those credentials, the utility won’t alter the USB port settings. Modes are: block all USB ports or unblock all USB ports.
Who is it recommended for?
This is a simple tool for small businesses. The package controls the USB ports on the computer that hosts it. So, an administrator would have to physically visit each computer to turn the blocker on. This isn’t a feasible prospect for the central IT support teams of mid-sized and large organizations.
Pros:
- Extremely simple tool
- Blocks ports with little to no technical knowledge
- Configures ports to require a password
Cons:
- Not ideal for larger networks
SysTools USB Blocker starts at $29. Click here for a trial version.
4. Endpoint Protector Device Control
Endpoint Protector Device Control is an encompassing security solution that controls and monitors USB ports to prevent any data theft or loss. It comes with many features that provide complete control over USB port usage and the resulting data theft. EndPoint Protector Device Control comes with many features that provide complete control and visibility over your USB ports and their usage.
Key Features:
- Cross-Platform Works well across platforms and devices, which means, you can monitor your employees’ devices regardless of their underlying operating system. It’s easy to monitor USB and other peripheral ports and you can even set policies that will be applied across all the operating systems.
- Simple and Lightweight A salient aspect of this tool is its simplicity. You can control all remote devices through a single web-based dashboard. Also, there’s no impact on the performance of any device due to this tool. It’s simple to use and requires no advanced technical skills, thereby making it ideal for all kinds of people. No prior training is necessary either.
- Ideal for Remote Working In today’s remote working world, this tool can be a handy way to grant or revoke USB access remotely. More importantly, you can do this even if the end devices are offline. Once the device comes back online, you can get the log reports.
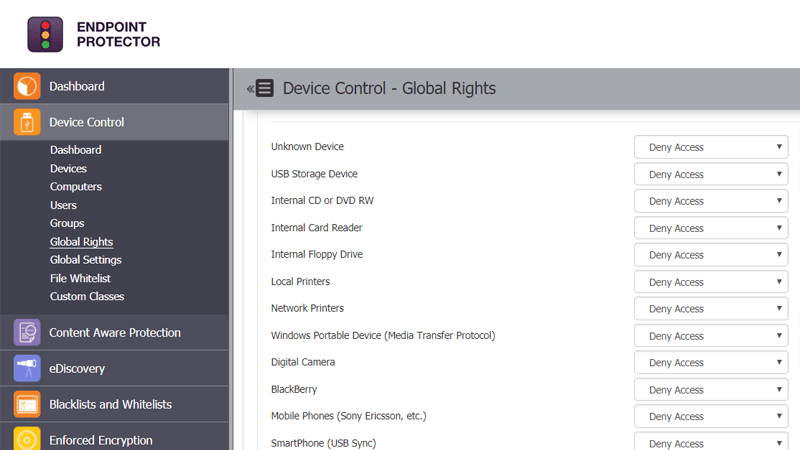
- Granular Control Provides granular control over the usage of USB and peripheral ports. Every team or department can even specify which devices’ ports can be used, whitelist or blacklist specific devices, define policies for each user or device, and more. All of these features ensure that the productivity of employees is not impacted and at the same time, it protects your data from theft or loss. You can even go a step further and ensure that all devices used within your organization are encrypted, so a data theft or loss has no meaning to the person doing it.
Why do we recommend it?
Endpoint Protector Device Control is a similar tool to the ThreatLocker system. It can control any device that connects to a USB port. The central server for this tool reaches across the network to each endpoint and blocks all USB ports by default. The administrator then builds up an allow list.
Who is it recommended for?
This is a very good system for companies that don’t have time or the expertise to fine tune a data protection plan and risk leaving exit points exposed while they consider their options. All USB ports are blocked by default. Devices can be approved for use by one user or on one computer or for use anywhere.
Pros:
- Cross-platform tool – Great for diverse environments
- Can remote monitor and alert to USB usage
- Supports lockdown of other peripheral ports
Cons:
- Can take time to fully explore all lockdown features
Overall, Endpoint Protector Device Control is a comprehensive tool that provides granular control of all USB ports, regardless of the operating system or device involved. Further, it is simple and non-intrusive while its web-based interface makes it easy to use for people of all technical levels.
Click here to request a quote. Click here to request a demo.
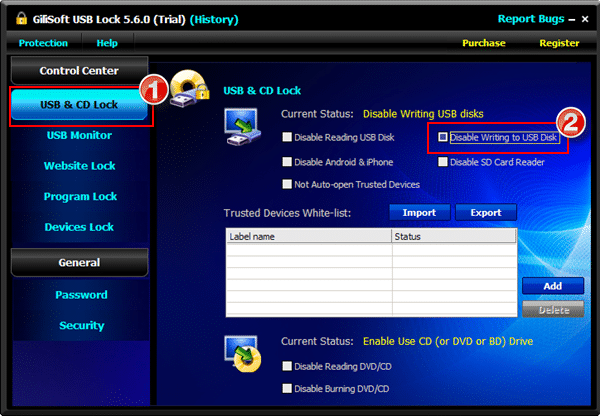
5. GiliSoft USB Lock
GiliSoft USB Lock, as the name suggests, locks down your USB ports to prevent anyone from illegally copying sensitive data to USB drives, CDs, or any other external storage mechanisms. Typically, this tool blocks all drives and devices that don’t belong to your organization.
Key Features:
- Blocks Drives Blocks both USB and SD drives on devices. It can disable both reading and writing on USB drives to protect your computer from not just data loss, but also from anyone installing malicious software. Also, you can whitelist certain trusted devices and these will be given reading and/or writing access, depending on what you want. Such a granular control will ensure that your business operations are not impacted while protecting your device.
- Reporting Logs every activity related to driving usage on a computer. With these logs, you can monitor USB activities, file operations like creation and deletion, history, whitelisted devices, user activity on USB drives, and more. Such comprehensive information is sure to provide the control you need over your devices. Further, this information can come in handy for internal and external auditing. You can even use these reports to prove compliance with industry standards.
- Website and Program Locks Goes beyond just drives and also locks websites and programs to protect your device. For example, you can block certain websites from displaying on your browser. In such cases, the original page is not loaded on the PC and the user is sent to a blank page. You can even customize this blank page to display any message you want. Likewise, you can also block programs to prevent them from executing on any device on your network. The best part is you can do all this with a single click on the control panel.
- Self Protection No one can uninstall this software without proper credentials. Further, admins have the option to make the Gilisoft USB Lock tool invisible, so users don’t even know that there’s protection software running on their device. Lastly, if someone enters a wrong password more than five times, the account is temporarily disabled and a notification is sent to the registered email. All these measures greatly bring down the chances of data theft.
Why do we recommend it?
Gilisoft USB Lock is a similar tool to SysTools USB Blocker, and they both run on Windows PCs. This tool will also block mobile devices from connecting to the computer and will also disable DVD drives. The system is able to allow specific USB devices to connect while retaining the default block for all other devices.
Who is it recommended for?
This is a good tool for personal use or for small businesses. The software can only control the USB ports on the computer on which it is installed and it is only available for Windows. This is a problem for mid-sized and large businesses that centralize IT support in one location.
Overall, Gilisoft USB Lock is a simple but effective tool to lock your USB drives and prevent data theft. That said, it works only on Windows 2000, 20003, XP, 7,8, 10, and 11.
Pros:
- Great user interface
- Blocks both USB ports as well as disk drives
- Offers password protection as well as full USB denial
- Can also block websites
Cons:
- Only suitable for small businesses
Gilisoft USB Lock costs $49.95. Click here to download a free trial.
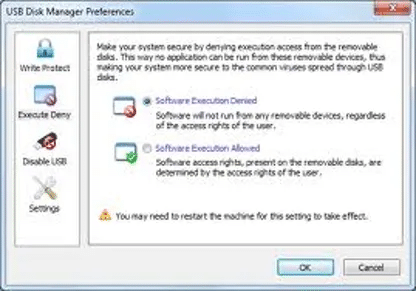
6. USB Disk Manager
The USB Disk Manager is a free tool that protects your system from any files transmitted to and from a USB drive. Essentially, it prevents your system from preventing any read/write operation on a USB drive. This means, that no malicious software can be transmitted from the USB drive, and no one can copy any file to it.
Key Features:
- Simple and convenient to use
- Works only on Windows
- Disallow read/write operation on USB drives
- Protects your system from malware or virus transmitted through USB drives
- Reduces the chances for authorized employees to copy sensitive content to a USB drive
- 100% FREE
Why do we recommend it?
USB Disk Manager is a free system that runs on Windows, with a number of functions. It can block all USB devices from attaching to a computer, and it has an option to allow access for file transfers while simultaneously blocking all programs from running. It is also possible to write protect a USB stick to prevent files from being deleted or overwritten.
Who is it recommended for?
Like GiliSoft USB Lock and SysTools USB Blocker, this tool will only operate on the computer it is installed on. It isn’t suitable for companies that administer their workstation fleet from one central office. Technicians in mid-sized and large businesses would not have the time to visit each computer to activate the block.
Pros:
- Lightweight application – uses little system resources
- Whitelist or completely lock down USB ports
- Deny specific file types and executables from running
Cons:
- Better suited for homes or small businesses
Click here to download this free Windows utility.
Conclusion
To conclude, USB port locking can prevent data thefts or loss, as no one will be able to copy sensitive files from a computer. At the same time, it will also prevent anyone from copying or installing malicious programs through a USB drive. Due to these benefits, USB port locking software is a must-have in your security arsenal.
In this article, we have listed a few highly effective tools. They come with many features that provide comprehensive security to your system. We hope it helps you to choose a tool that’s the best fit for your work environment.
USB Port Locking Tools FAQs
How do I lock USB ports?
To lock USB ports, you can use a variety of software tools or hardware devices. These can include USB port lockers, software-based access control tools, or group policy settings in a Windows environment.
Can USB ports be locked on a Mac or Linux computer?
Yes, USB ports can be locked on a Mac or Linux computer using software tools or hardware devices that are compatible with these operating systems.
What are some best practices for USB port locking?
Some best practices for USB port locking include using a combination of software and hardware-based locking methods, limiting access to USB ports to authorized users or groups, regularly monitoring USB activity, and implementing a strong security policy for USB devices.
Are there any drawbacks to USB port locking?
USB port locking can potentially limit productivity and can cause issues if authorized users need to transfer data using USB devices. Additionally, some USB port locking methods may be susceptible to bypassing or hacking, which can compromise overall system security. Using port locking tools can make granting access easier to balance security and productivity better.
What is software-based USB port locking?
Software-based USB port locking involves using a software tool or application to restrict access to USB ports. This can involve setting permissions or access controls, or using specialized software that can monitor and block USB activity.