Insider threats are broadly defined as threats that come from within the organization. Typically, these threats are due to disgruntled current and former employees who want to take “revenge” on the company. Sometimes, it can also be for gain, where these employees take money from competitors and pass on the organization’s secrets to them. These employees tend to be those who have privileged access to sensitive information and can access them at any time.
At first glance, this may look like a hypothetical situation or one that feels straight out of a movie. But if you look at the statistics, you’ll know that it’s real and can happen to any organization. A recent study by ID Watchdog shows that insider attacks are responsible for 60% of data breaches that happen within an organization!
Types of Insider Threats
Three types of insider attacks are possible. The first is a malicious actor who intentionally steals data from a computer and stores it on a removable drive. Later, this drive is used for ransom or is sold to competitors for money. The second is a careless employee who exposes sensitive information without intending to do so. These employees don’t gain anything from such acts. The third type of threat is from a mole who works for another organization but poses as an employee to gain confidential information.
Out of these three, the first threat is the most dangerous, and also, the hardest to detect. However, a common pattern is that these employees tend to copy data to a removable drive, as this is often hard to detect. So, one good way to prevent such attacks is to lockdown your USB, as this will prevent anyone from copying files to a removable drive.
This brings up the next question, how can you lock down USB ports? Using something called a USB lockdown software. As the name suggests, this software makes the USB ports inaccessible, thereby making it impossible for anyone to copy information on a removable drive. Since sending data to emails or any other means is easily traceable, the chances for insider attacks are reduced greatly.
Here is our list of the best USB lockdown software:
- ThreatLocker Storage Control – EDITOR’S CHOICE This USB device management tool blocks all USB ports by default and then allows authorized devices to attach but only for access by specific users. Access a free demo.
- ManageEngine Device Control Plus – FREE TRIAL This USB device control tool monitors all the removable devices connected to your computer and locks down the USB ports to prevent anyone from copying sensitive information. Start a 30-day free trial.
- Endpoint Protector This platform encompasses a slew of individual tools that work together to prevent accidental data loss and intentional data thefts, and in the process help with compliance.
- Ivanti Unified Endpoint Manager This is a client-based unified endpoint manager for all your devices, including the ones used by your employees. Its many advanced features such as remote control, user profile management, and more protect your sensitive data.
- Broadcom DLP Earlier known as Symantec, Broadcom DLP mitigates data breaches and accidental loss. Along with it, this platform also reduces compliance risks.
- McAfee DLP This platform provides comprehensive protection for your sensitive data by monitoring its movement across devices and plugging all leaking channels such as USB drives, cloud apps, and more.
Let’s now take a detailed look at each of these tools to help you find the appropriate one for your organization.
The Best USB Lockdown Software
Our methodology for selecting USB lockdown tools and software
We reviewed various USB lockdown tools and analyzed the options based on the following criteria:
- Ability to integrate into enterprise environments
- Ability to grant and restrict access easily
- Ability to monitor and restrict other methods of data extraction
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
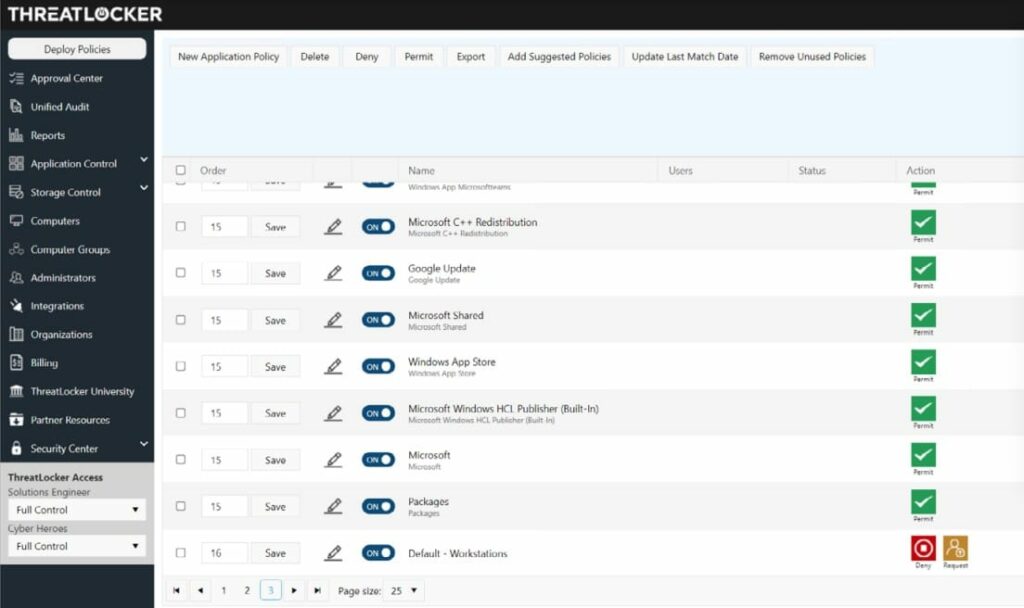
1. ThreatLocker Storage Control – GET DEMO
ThreatLocker Storage Control is a module on a cloud platform that provides a suite of security tools to protect against malware and data loss. This unit blocks USB devices from attaching to any computer on the protected network. The system administrator can then allow specific devices to attach.
Key Features
Here are some of the important mechanisms behind the ThreatLocker strategy:
- Security Policy Management This section of the ThreatLocker console applies to all units in the suite. You set up a deny-all strategy, which applies to software as well as USB devices.
- USB Port Controls The cloud-based ThreatLocker system reaches across the internet to every endpoint on the protected network and it disables the USB ports on each.
- Permitted Usage The Security Policy system includes an access rights manager (ARM) and that enables specific software to access otherwise-blocked files, directories, and devices. The system also allows the creation of permissions for users to access that software that has access to resources. The same system allows users to have access to specific USB devices.
- Conditional USB Attachment Each USB device can be identified by its serial number. This enables individual devices to be approved for use. This approval goes into the ThreatLocker ARM.
- User Access Requests A user can send a request to use a new USB device. After slotting the device into the computer, the blocking feature triggers with a popup that sends a notification to the system administrator who can approve the device or let the request expire.
The Storage Control package is delivered together with data and application fencing tools that enable the creation of a micro-segmentation security system.
You can contact ThreatLocker for a custom quote. Get access to a free demo system.
EDITOR'S CHOICE
ThreatLocker Storage Control is our top pick for USB lockdown software because it offers fine-grained controls on USB devices rather than just imposing blanket bans. All USB ports are updated to block all USB devices by default. With that security measure in place, the administrator can approve specific devices for use. Only these approved devices will work when inserted into a computer in the company’s fleet. Devices can be identified by a serial number and the administrator can choose to allow it for use with all computers or just one specific endpoint. It is also possible to limit the device’s use to just specified user accounts.
Download: GET FREE DEMO
Official Site: https://portal.threatlocker.com/signup.aspx
OS: Cloud-based
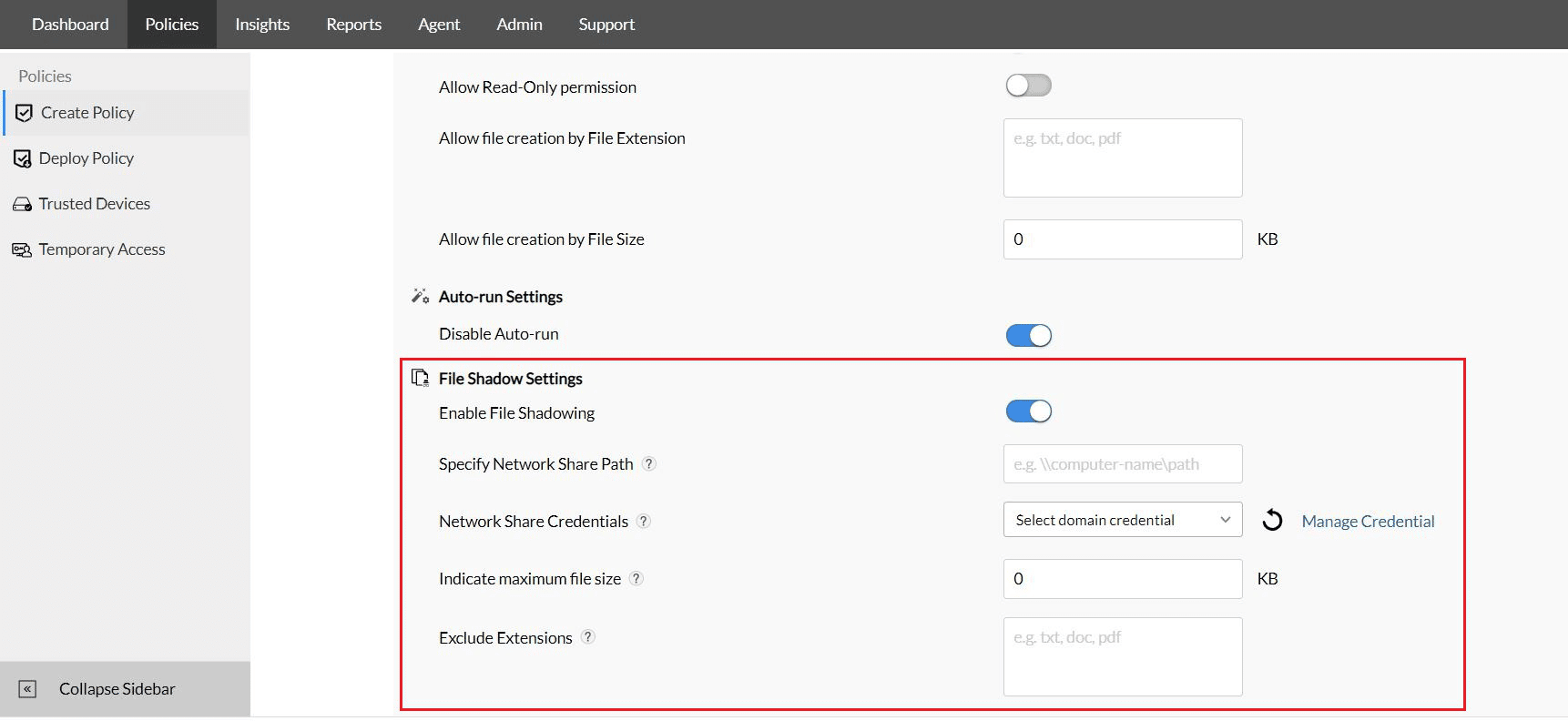
2. ManageEngine Device Control Plus – FREE TRIAL
ManageEngine’s Device Control Plus is an advanced platform for streamlining and controlling access to files and devices that contain sensitive information. It provides the option to monitor, control, and block both USB and peripheral devices, so no one can take your data intentionally or accidentally.
Key Features
Here’s a look at some of the key features of ManageEngine Device Control Plus.
- Role-based Access Control This tool makes it easy to implement role-based access and control to files and devices. As an organization, you can choose whom to provide access to, and in general, it’s best to limit access to only those who need it. This reduces the chances of accidental data loss and malicious data theft.
- File Access Control With Device Control Plus, you can get granular and restrict certain files from being transferred. For example, you can set limits on file sizes that can be transferred. This means that files that are larger than the specified sizes have to be transferred using removable media, and if you lock down the USB port, you effectively seal the data theft.
- Temporary Access to Third-party Devices This platform provides the option to grant access to third-party devices for a specific time. Once this time ends, the access is automatically revoked. Needless to say, this feature strikes a balance between employee productivity and security.
- No Specialized Expertise Device Control Plus is simple to set up and easy to use and requires no additional expertise at all. Its centralized dashboard as well as its extensive reports require no training whatsoever to use.
In all, Device Control Plus is an advanced platform that provides the required features to safeguard your data and prevent it from getting stolen or lost.
Pros:
- Designed to work right away, features over 200 customizable widgets to build unique dashboards and reports
- Leverages autodiscovery to find, inventory, and map new devices
- Uses intelligent alerting to reduce false positives and eliminate alert fatigue across larger networks
- Supports email, SMS, and webhook for numerous alerting channels
- Integrates well in the ManageEngine ecosystem with their other products
Cons:
- Is a feature-rich tool that will require a time investment to properly learn
Click here to download a trial version.
3. Endpoint Protector
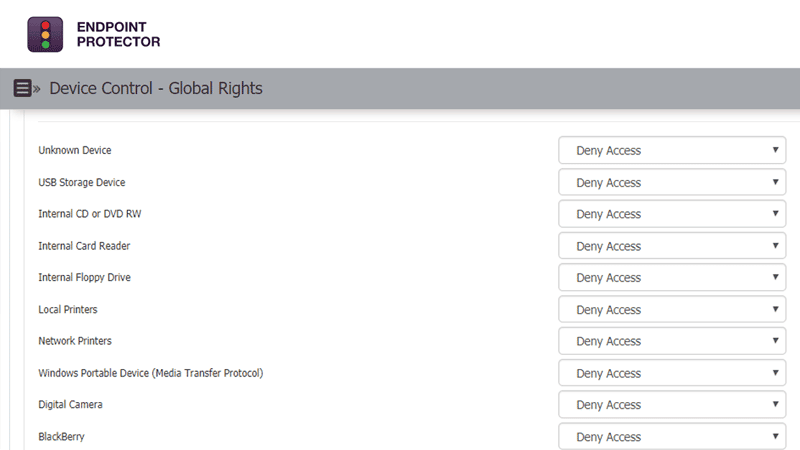
Endpoint Protector is an enterprise-grade DLP solution that detects, monitors, and protects sensitive data across all employee devices. It is simple to use and at the same time, is powerful enough to prevent data loss and theft.
Key Features
Below are the salient features of Endpoint Protector.
- Device Control The Device Control module of Endpoint Protector provides complete control of USB and other peripheral ports. In turn, this prevents data loss and leaks and also prevents anyone from using USB ports as a means to spread malware and viruses.
- Content-Aware Data Loss Prevention Endpoint Protector constantly inspects the content to protect your enterprise data. You can mark certain content as sensitive and whenever it is transferred, this tool sends an alert. It even scans third-party tools like Skype and Dropbox to ensure that no data is leaked or stolen. In the process, it also boosts compliance with HIPAA, GDPR, and more.
- Enforced Encryption This platform supports the use of encryption to manage and secure your USB devices. The biggest advantage is that your data will be protected even during transit as the contents are encrypted and would require a password to decrypt. This prevents accidental or intentional interception of data while it is moving from one device to another.
- eDiscovery of Sensitive Data Endpoint Protector scans all the sensitive data stored across your devices and adds an extra layer of security to them. In the case of unauthorized access, this tool also suggests remedial actions such as encryption or file deletion.
Thus, these are some of the important features of Endpoint Protector. It is undoubtedly comprehensive and protects your data both at rest and during transit to reduce the chances of data theft or accidental loss.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
Click here to request pricing. Click here to request a demo.
4. Ivanti Unified Endpoint Management
Ivanti Unified Endpoint Manager (UEM) provides complete control over all your on-prem endpoints. As a result, you have total visibility over all your assets and can even secure your IT investments accordingly. Also, Ivanti UEM provides recommendations to optimize their performance and cost, while preventing any accidental or malicious access to them.
Key Features
Read on to get a glimpse of the features that prevent data loss for your organization.
- Unified Endpoint Management In today’s remote work culture, staying on top of all the endpoints that access your data becomes critical. Ivanti works well across different operating systems such as macOS, Windows, Linux, Chromebooks, and even Raspberry PI OS. You can also deploy it across servers, PCs, and IoT devices.
- Simplified Configuration and Use Ivanti offers one-click access to protect your data as you can configure and manage IT policies related to individual users and groups within your organization. It even supports some intelligent actions such as distributing data only to those devices that need them.
- Customized Dashboards and Reporting This platform combines with another tool called Ivanti Xtraction to customize your dashboards and provide all the information in easy-to-read reports. As a result, you’re always aware of what’s happening within your organization and can take action accordingly. It helps with internal auditing and compliance as well.
- Reduce Disruptions due to Outages Sometimes, data losses and thefts occur due to system outages and device downtimes. Ivanti reduces the chances for these events by streamlining change and configuration activities. You can even make better use of existing resources to boost employee productivity.
Overall, Ivanti UEM provides a whole gamut of services that protect your sensitive data and provide visibility across all your IT assets.
Pros:
- Multi-platform support for Linux, Mac, and Unix gives the tool flexibility in diverse networks
- Patch scheduling works well out of the box
- Applies a zero trust model out of the box
- Offers simple graphical reporting which is easy to setup
Cons:
- Must contact company for exact pricing
Contact the sales team for pricing information. Click here for a free trial and here for a demo.
5. Broadcom DLP
Broadcom, formerly Symantec, offers an advanced Data Loss Protection (DLP) that mitigates data breaches and protects your sensitive data from unauthorized access. Its reporting tools also help with auditing and compliance.
Key Features
Join us to take a peek at some of the important features of Broadcom DLP.
- Protects your Critical Data Symantec DLP protects your critical data and keeps it safe from accidental breaches or malicious attacks by monitoring it at all times. It continuously scans remote and local devices to monitor how the confidential data is used and accordingly notifies the authorized users. Symantec DLP scans not just servers and PCs but also includes laptops, databases, cloud apps, and more.
- Total Visibility This tool provides complete visibility and control over your information, where it is currently stored and how and where it is moved, etc. This visibility greatly reduces the chances for your data to get stolen or exposed accidentally. Further, you can monitor risky behavior and can even fine-tune IT policies to strike a balance between security and productivity.
- Quick Remediation In the event of a data breach or loss, DLP offers the tools to quickly remediate and cut back your losses. It comes with an advanced workflow to streamline and automate the remediation process. You can encrypt files, decentralize incident remediation, block sensitive content based on the request attributes, do a detailed user-behavior analysis, and more.
- Labeling and Compliance You can extend Broadcom DLP to create Microsoft Information Protection (MIP) classification and encryption to ensure that the most important documents are classified and protected. Such features also help compliance with many regulations such as HIPAA, GDPR, PCI, SOX, and more.
Broadcom DLP is an advanced solution for preventing data breaches. It provides complete visibility over your sensitive information and its movement across devices. In the process, it helps with compliance as well.
Pros:
- Can automated tasks across multiple operating systems – Linux, Windows, macOS, etc.
- Great for diverse environments – BYOD setups
- Can support over 100k agents – great for enterprise use
Cons:
- Would like to see more workflow visualization options
- Not the best fit for smaller organizations
Contact the sales team for a quote. There are no free trials, downloads, or demos at the time of writing this piece.
6. McAfee DLP with Total Protection
McAfee Total Protection for DLP is a comprehensive data protection platform that continuously monitors your data and prevents it from getting leaked through cloud apps, removable drives, web postings, and more.
Key Features
Let’s now take a detailed look into the features of McAfee DLP.
- Device-to-Cloud DLP A salient feature of this tool is its device-to-cloud DLP, where the IT policies that you devise for on-prem devices can also be extended to the cloud. The classification tags and other pertinent information are also shared.
- Comprehensive Protection McAfee DLP provides comprehensive protection across all devices. It continuously monitors your data at rest and in transit, across your removable storage media, sharing applications, web postings, and more. You can also configure this tool to monitor those data that are classified as sensitive, and this will extend across all devices and storage media.
- Advanced Features This platform comes with many advanced features like user behavior analytics to make intelligent predictions on data thefts, so you can plug them at the earliest. It also conducts regular security analysis to instantly detect any suspicious user or device behavior.
- Compliance With McAfee DLP, you can stay assured of your compliance with leading standards such as HIPAA, GDPR, SOX, and more. It generates detailed reports regularly to help you track and audit your progress, and make any changes if necessary, to meet the compliance standards. It also offers templates that can ease this compliance process for you.
Overall, McAfee DLP is a comprehensive platform for protecting your data from accidental and malicious loss. Plus, it gives you complete visibility of your data and helps with meeting compliance standards.
Pros:
- Supports Windows, Linux, and Mac OS
- Offers roll-back points for infected endpoints
- Monitors network traffic to stop DDoS attacks, botnets, and rouge mail servers
- Allows sysadmins to orchestrate security policies across their environment
Cons:
- McAfee can use a lot of system resources while scanning (not ideal for older endpoints)
The cost of McAfee DLP depends on the number of nodes.
- For 5 to 25 nodes – $100/node
- 26 to 50 nodes – $98/node
- 51 to 100 nodes – $90/node
There are no free downloads at the time of writing this piece.
Thus, these are some of the best USB lockdown software available for you. As you can see, these platforms go beyond just USB locking and strive to provide more comprehensive protection for your sensitive data.
Conclusion
To conclude, classified information is an important asset, so you must take all possible efforts to prevent its loss or theft. This classified information is highly vulnerable to insider threats, that is from employees who are authorized to view them. Since this is also difficult to track, you must take all the necessary steps to prevent the theft of your confidential information.
This is where Data Loss Prevention (DLP) tools come in handy. These tools provide the visibility you need across your sensitive data, so you know where and how it is used at all times. More importantly, this can lockdown your USB drives, so no sensitive information can be transferred through removable media.
The tools described in this article have advanced capabilities to protect your data, and we hope you find all this information useful. Feel free to check out our other guides as well.
USB Lockdown Software FAQs
How does USB lockdown software work?
USB lockdown software works by blocking access to USB ports and devices that are not authorized by the administrator. The software can either completely disable USB ports or allow access only to authorized USB devices.
What are the benefits of using USB lockdown software?
The benefits of using USB lockdown software include increased security, protection against data theft or loss, and improved compliance with industry regulations. It can also help prevent the spread of malware through unauthorized USB devices.
What types of organizations can benefit from using USB lockdown software?
Organizations of all sizes and industries can benefit from using USB lockdown software, particularly those that handle sensitive data or have compliance requirements.
How does USB lockdown software compare to other types of security software?
USB lockdown software is a type of endpoint security software that focuses specifically on securing USB ports and devices. It is typically used in conjunction with other types of security software, such as antivirus software and firewalls.
What are some popular USB lockdown software solutions?
Some popular USB lockdown software solutions include Endpoint Protector, DeviceLock, and Netwrix USB Blocker.