Data is one of the most valuable assets today. Companies around the world are collecting and analyzing billions of data bits every second to get a holistic idea of their customers’ preferences and behavior. Using this information, companies can provide targeted advertising, that in turn, is sure to boost their revenue.
Personally Identifiable Information (PII) is the personal information about an individual that can be used to identify that entity. And this is exactly what companies are seeking. As this can quickly cross into a gray and illegal area, governments around the world are coming up with the necessary legislation to protect individuals’ data. Such legislation also mandates companies to follow certain data collection and analytics processes, so they are in tune with the prevailing legislation.
From a company’s standpoint, it becomes essential to collect the PII as it’s necessary for their operations and at the same time, comply with the prevailing legislation. This is where PII scanning tools help.
PII Scanning Tools and their Benefits
PII Scanning tools, also known as PII Scanners, are well-suited for organizations that store personal and confidential data as it helps them to comply with the prevailing legislation.
Some of the other benefits that come with PII scanning tools are:
- Helps you to build trust and loyalty among customers
- Secures your customers’ data from unauthorized access.
- Reduces the chances of hacking
- Maintains compliance
- Enables you to make the most of the data you collect
Now that you know the benefits of PII scanning, let’s look at some of the best tools available today.
Our methodology for selecting a PII tool that will identify and classify sensitive data
We reviewed the market for sensitive data scanners that will identify PII and assessed tools based on the following criteria:
- A scanner that can access all workstations, servers, storage arrays, and cloud storage accounts
- Adaptable to specific data protection standards
- Categorization for risk levels
- A scanner that can also locate intellectual property
- Nice to have a package that can also implement data protection
- A demo or a free trial that provides an opportunity to test the tool before buying
- Good value for money provided by a price that reflects the quality of services on offer
Best PII Scanning Tools
Here is our list of the best PII scanning tools:
- ManageEngine DataSecurity Plus – FREE TRIAL This advanced auditing and security tool protects your confidential data from unauthorized access and at the same time, helps to comply with regulations related to data security and privacy. Start a 30-day free trial.
- ManageEngine Endpoint DLP Plus – FREE TRIAL Protects endpoint data USB locking, file monitoring, and various reporting and auditing options. Start a 30-day free trial.
- Endpoint Protector This platform can discover, monitor, and protect your sensitive PII data, besides ensuring regulatory compliance.
- OneTrust This privacy, security, and governance tool helps you to protect your data and comply with the prevailing laws of the land.
- Digital Guardian DLP This enterprise SaaS solution offers advanced data protection to reduce the chances of data loss. Through its features, it helps with internal auditing and compliance as well.
- Teramind DLP A platform for securing your data from insider and outsider attacks through extensive monitoring capabilities.
Let’s now do a deep dive into each of these tools, so you can decide which of these is a good fit for your business.
1. ManageEngine DataSecurity Plus – FREE TRIAL
DataSecurity Plus from ManageEngine protects your data from unauthorized access, thereby protecting you from both insider and outsider attacks. Further, its auditing capabilities ensure you meet the tenets of the prevailing laws.
Key Features
The salient features of DataSecurity Plus are as follows.
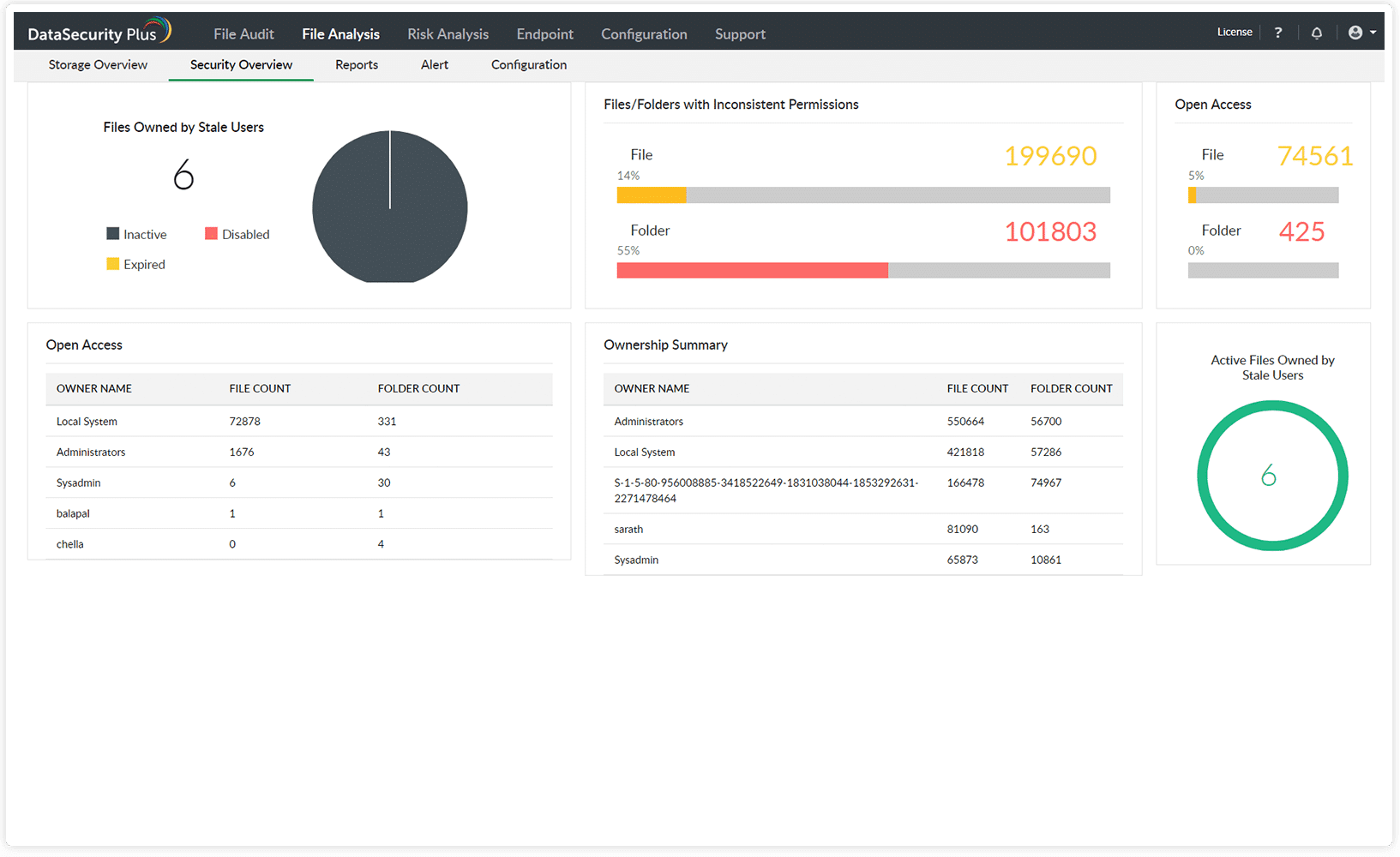
- Provides In-Depth Data Visibility This tool tracks access to all the files and data, so you know who is accessing a piece of data and when. Any action performed on these files such as reading, changing permissions, etc., are also recorded in real-time, so you can view them at any time for auditing. Similarly, it tracks and records when anyone uses Ctrl + C or right-click for copying content. Also, the movement of files to other locations including on USB drives is tracked closely. All these greatly reduce the chances of insider attacks.
- Discovers and Classifies Data DataSecurity Plus quickly locates files that contain sensitive information and classifies them accordingly, so additional layers of protection are automatically added to it. It also comes with automated and manual tagging features that make it easy to find the information you want.
- Data Security Protects your data in many ways. It secures and controls access to USB drives, inspects email attachments, prevents ransomware attacks, spots unusual activities in your cloud applications and files, and so much more. More importantly, it protects your sensitive data from getting posted on social media and other unauthorized websites. All these measures ensure that your data is protected at all times.
- Auditing and Compliance This tool allows you to generate reports for a ton of standards like GDPR, SOX, HIPAA, PCI, and more. It also continuously audits your data and alerts you on gaps and vulnerabilities
Why do we recommend it?
ManageEngine DataSecurity Plus is a data loss prevention system that is sold in four modules. You get eDiscovery for sensitive data, which includes PII, with the Data Risk Assessment unit. This service adjusts its searches for a given data security standard, such as PCI DSS, HIPAA, or GDPR.
Who is it recommended for?
The DataSecurity Plus system runs on Windows Server. Apart from the Data Risk Assessment tool, you can get File Server Auditing for file integrity monitoring and ransomware protection, File Analysis, which examines access permissions, and Data Leak Prevention, which patrols exfiltration points to block unauthorized data movements.
Overall, DataSecurity Plus is a comprehensive tool that adds a lot of value to your business. It achieves multiple objectives such as data security, protection, compliance, and more.
Pros:
- Provides a detailed account of file access, allowing sysadmin to understand the context of the file changeThe platform can track access trends over time, allowing for better malicious behavior detection
- Supports built-in compliance reporting for popular standards such as HIPAA, PCI DSS, and FISMA
- Can integrate with numerous helpdesk solutions, notification platforms, and backup systems
Cons:
- Requires a sizable time investment to fully explore all the platforms features and tools
Pricing: Click here to get a quote.
EDITOR'S CHOICE
ManageEngine DataSecurity Plus is our top pick for a PII scanning tool because it provides a range of PII protection systems that start with scanning. New data items that are stored to a disk are instantly assessed for sensitivity. The package can be tailored to specific types of data, such as credit card numbers, social security numbers, telephone numbers, or health provider IDs. As well as detecting PII and intellectual property, the ManageEngine system includes methods to protect those data stores from unauthorized access, inappropriate use, or ill-advised data movement. The tool is able to scan on-premises systems and cloud accounts and it also controls peripheral devices, email systems, and file transfer packages.
Download: Get a 30-day free trial
OS: Windows Server
2. ManageEngine Endpoint DLP Plus – FREE TRIAL
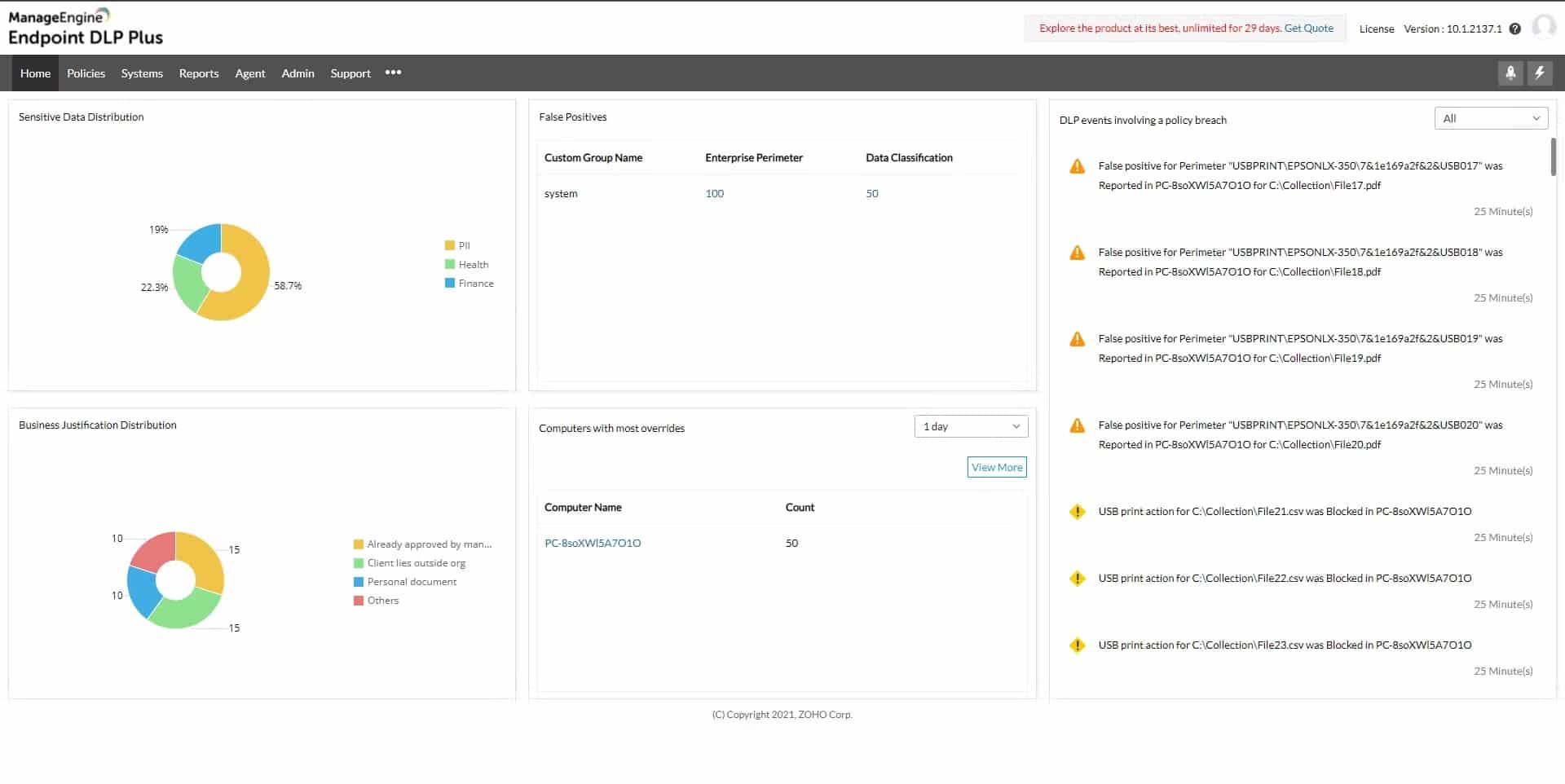
ManageEngine Endpoint DLP Plus is a platform that helps protect sensitive data on devices, users, and files across a network. It can be used in both local area networks (LANs) and cloud environments. The platform uses data containerization and intelligent alerting to categorize data and reduce false positives, ensuring productivity while keeping data secure.
Key Features
- Performs proactive scanning and documentation
- Identifies suspicious account behavior
- Runs on multiple operating systems (Windows, Linux, and Mac)
Why do we recommend it?
ManageEngine Endpoint DLP Plus is another data loss prevention package from ManageEngine. This system is a single package rather than a platform of modules. This system includes eDiscovery, user behavior tracking, and data movement controls. Endpoint DLP Plus is a software package for Windows Server.
It can also automatically identify potentially suspicious user actions, such as those that may indicate a compromised account or insider attack. Setting up and using Endpoint DLP is easy, even for those without prior experience, thanks to its various templates and wizards that allow users to classify sensitive data and apply policies quickly.
Who is it recommended for?
This system is particularly needed by companies that have to comply with data security standards. The sensitive data discovery and classification system can be tailored to a specific standard, such as PCI DSS, HIPAA, or GDPR. There is a Free edition that covers 25 endpoints and that’s ideal for small businesses.
Pros:
- Flexible deployment options across multiple platforms
- Can be installed on both Windows and Linux platforms, making it more flexible than other on-premise options
- Offers in-depth reporting, ideal for enterprise management or MSPs
- Integrated into more applications than most patch management solutions
Cons:
- ManageEngine is a feature-rich platform that takes time to fully explore and learn
Pricing: Click here to get a quote.
Free Trial: Start a 30-day free trial.
3. Endpoint Protector
Endpoint Protector is an industry-leading cross-platform DLP that discovers and monitors your sensitive data to prevent data loss prevention and increase compliance with the leading standards.
Key Features
Endpoint Protector comes with many advanced features, such as the ones mentioned below.
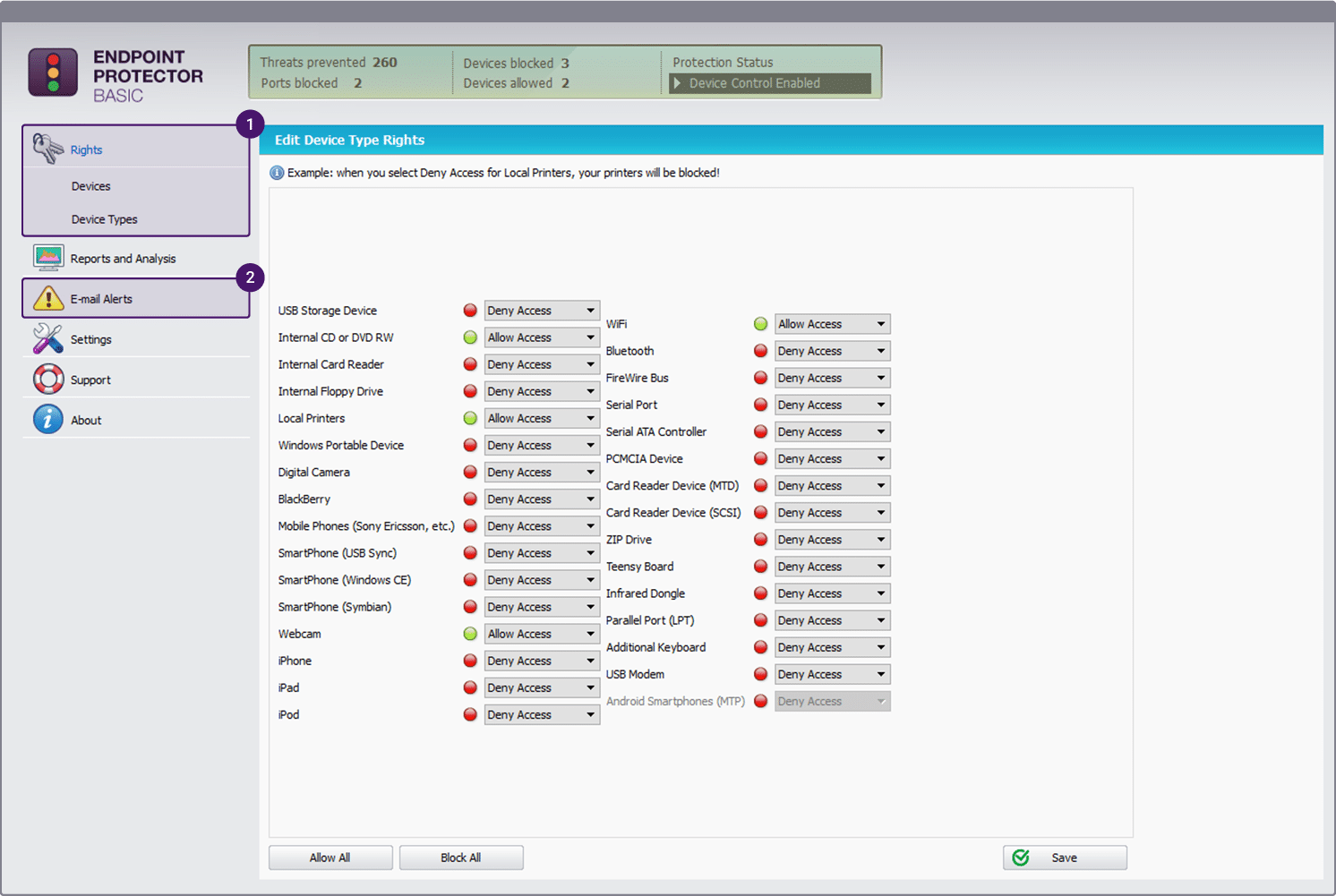
- Provides Complete Control A salient feature of Endpoint Protector is that it provides complete control over your sensitive data at all times. You can set up configurable alerts that will notify you when there are deviations from the established baseline practices and actions. Besides this, you can also take a look at the detailed logs and information related to file access, events, device activity, and more to understand if there has been any unusual activity.
- Integration with SIEM Tools Endpoint Protector comes with SIEM integration capabilities, so you can better analyze the logs, and get a holistic view of your entire infrastructure. With this information, you can even create custom dashboards and reports that will help you to make informed decisions about your infrastructure.
- Reduces Insider Attacks This tool comes with many advanced features that reduce the chances of insider attacks. Its content inspection and contextual scanning capabilities monitor the use of applications such as Skype, Dropbox, etc, for the transfer of sensitive files. Further, it also looks into the use of removable devices that can be used for transferring sensitive data. This tool can also lock down devices, so peripheral and USB ports can’t be used for transferring data. All these measures greatly reduce the chances for disgruntled employees to steal sensitive data.
- Encryption Endpoint Protector uses encryption to protect your data, both in transit and at rest. This can be a great deterrent for anyone who is trying to steal your data. Also, password-based access adds another layer of security to your data, thereby increasing the overall protection of your sensitive data.
Why do we recommend it?
CoSoSys Endpoint Protector is a data loss prevention system that scans endpoints running Windows, macOS, and Linux. The package is available as a SaaS platform or you can install it as a service on AWS, GCP or Azure. Another option is to run the software on your own server as a virtual appliance.
Who is it recommended for?
This package will discover and classify sensitive data and it can be tuned to specific data protection standards, such as HIPAA, PCI DSS, and GDPR. The service includes controls of USB sticks and email systems to block unauthorized data movements. CoSoSys doesn’t publish a price list and there is no Free edition, so it is difficult to assess the system’s appeal for small businesses.
Overall, Endpoint Protector has many advanced features to protect your data from unauthorized access, while making it easy for authorized employees to find the data they want. Through it all, this platform ensures compliance with leading standards.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
Pricing: Contact the sales team for a custom quote based on your specific needs.
Demo: Click here to request a demo.
4. OneTrust
OneTrust is a comprehensive platform that provides streamlined privacy, security, and governance for your data. It keeps your data safe while complying with regulations like GDPR.
Key Features
Here are some noteworthy features of OneTrust.
- Handles Data Governance OneTrust stays on top of your data always. It streamlines access to your data and ensures that unauthorized people don’t misuse your data. Such security and governance measures enhance the trust that your customers have in your business and can drive higher business value.
- Manages Privacy This platform comes with comprehensive privacy management features and even enables Privacy by Design. This helps you to create frameworks for complying with specific laws and regulations. More importantly, these privacy practices create a culture of accountability.
- Discovers and Classifies Data OneTrust has an AI-powered data discovery technology that makes it easy to find the data you want across multiple IT systems. Further, it tags and classifies data for easy searchability and accountability. You can even apply custom rules based on this classification.
- In-house Researchers A salient feature of OneTrust is that it has a team of in-house researchers and a network of 500+ contributors spread across 300 jurisdictions. What this means is you can stay on top of any changes in existing laws or the implementation of new legislation and can align your business with these changes.
Why do we recommend it?
OneTrust offers a range of company compliance management tools on its platform. These include a Governance, Risk, and Compliance module and a Privacy and Data Governance system. That second package is aimed at discovering and classifying stores of sensitive data. The package also provides a data retention consent gathering form for websites.
Who is it recommended for?
OneTrust caters to large corporations and even supplies legal advisors for bespoke guidance. The package also provides data management assessments for strategy reviews. That level of service doesn’t come cheap and it will be beyond the budgets of small businesses. The company also provides ESG guidance and management.
Overall, OneTrust is a comprehensive platform that can handle data governance, privacy, and compliance.
Pros:
- Barebones interface keeps things simple and straightforward
- Self assessments can easily be converted into reports to demonstrate compliance
- Comes with a prebuilt rights request portal
- Provides insights to reach compliance through gap analysis
Cons:
- Would benefit from a longer 30-day trial
Pricing:
OneTrust offers three pricing tiers:
- Large enterprise pricing
- Growing business pricing
- Special industry pricing
Click here to get the pricing for each of these tiers. The company claims that it can beat any competitor’s pricing, so that’s something you may want to consider.
Demos and Free Trials: Click here to request a demo and here for a free trial.
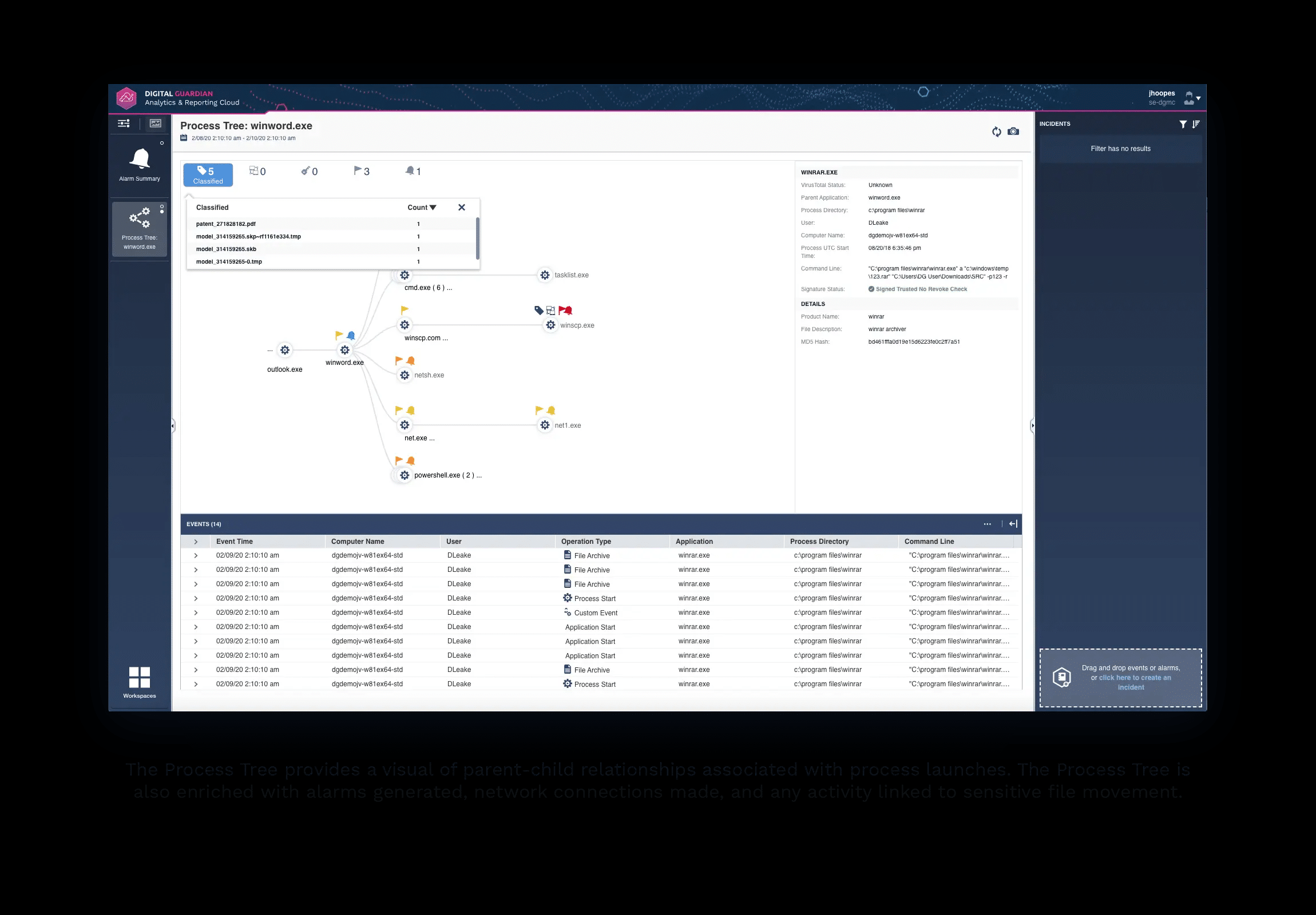
5. Digital Guardian DLP
Digital Guardian is an advanced Data Loss Prevention (DLP) tool and one of the few SaaS-based solutions available for Enterprises. It supports on-demand scalability and quick deployment to provide flexibility in protecting data across applications.
Key Features
Here’s a look at a few of the features of Digital Guardian DLP to give you an idea of what this platform can do for your business.
- Works Well Across Platforms A salient feature of Digital Guardian is that it works well across platforms such as Windows, macOS, and Linux. You can also use it across both cloud-based and native applications. Since it is cloud-delivered and powered by AWS, you get benefits such as low overhead costs, scalability, flexibility, and more.
- Comprehensive Classification and Discovery Digital Guardian DLP classifies data based on context and sensitivity. Such classification makes data discovery quick and easy, and at the same time, gives you complete control over their access and use. You can see everything that happens to your sensitive data and can implement finely-grained controls to log, monitor, backup, and protect all the data before it gets corrupted, lost, or stolen.
- Protects Data This platform is backed by an experienced team of analysts who are constantly on the lookout for cyber threats. This team understands the sensitivity of your data and accordingly comes up with a set of policies that greatly reduce insider and outsider attacks. Every action and strategy is also logged, so you can stay on top of every security measure that’s implemented within your organization.
Why do we recommend it?
Digital Guardian DLP is a SaaS platform of data loss prevention tools, including sensitive data discovery. The discovery process can be tailored for specific types of data, according to the requirements of a specific data protection standard. The system scans through files and identifies groups of data fields that are close to each other that collectively could identify an individual.
Who is it recommended for?
The cloud platform of the system removes any operating system restrictions on using the package. However, the company doesn’t publish a price list and that will deter small businesses. Companies that don’t have the right staff to manage data privacy could opt for the Digital Guardian Managed Security Program.
Overall, Digital Guardian DLP is designed to protect your sensitive information while helping you comply with regulations. Plus, you also get to enjoy the benefits of a SaaS-based application.
Pros:
- Simple and sleek interface keeps insight easy to read
- Balances simple visualizations with recent events
- Available for Windows, Linux, and Mac
- Agents can still work to stop access, even when offline
- As options to protect compliance data as well as company intellectual property
Cons:
- Plugins can sometimes cause issues, especially the email plugins
- False positives can be excessive
Pricing: Contact the sales team for a custom quote.
Demo: Click here for a free demo.
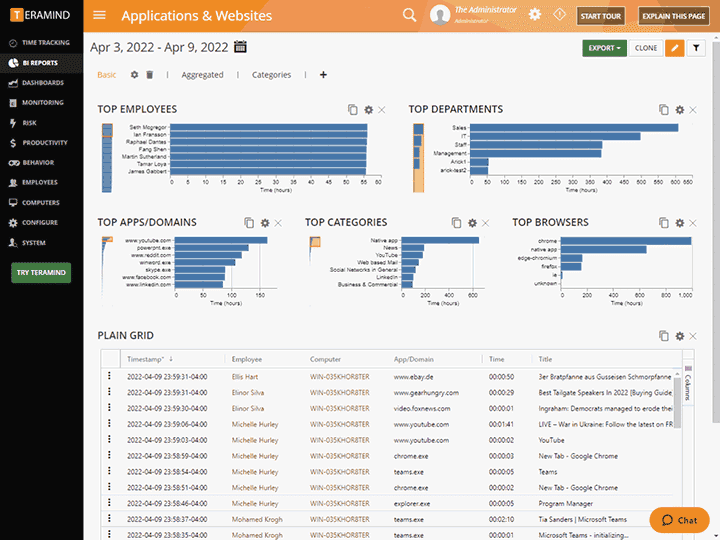
6. Teramind DLP
Teramind DLP protects your sensitive data from insider and outsider attacks using a combination of user activity monitoring strategies. Along with it, the extensive reporting capabilities help with internal auditing and compliance.
Key Features
Below are some important features of Teramind LLC.
- Protects from Insider Threat This platform secures your data from insider attacks using a combination of different strategies. It uses intelligent data-backed behavior that optimizes employee monitoring and ensures that the possibility of insider attacks is identified before they occur.
- Prevents Data Loss Teramind DLP protects your data against accidental loss, intentional thefts, negligent leaks, and more. Its comprehensive strategy protects your sensitive data from all possible angles. In turn, this enhances your company’s reputation and helps to build trust among your employees.
- Compliance This platform ensures that your data storage and security strategies align with the industry’s standards. It also takes into account the human aspect of compliance management. Further, it makes sure that all data activities are in tune with the prevailing laws and legislation.
- Detailed Analytics Teramind DLP provides detailed analytics and reports that can be used to analyze user and entity behavior. It can also help with internal auditing. Overall, Teramind DLP is a comprehensive platform that can protect your data from loss and insider threat, besides helping with compliance and internal audits.
Why do we recommend it?
Teramind DLP is a plan level of the Teramind employee tracking system. Teramind focuses on insider threats and this edition adds sensitive data discovery to the package. The tool is able to scan PDFs and images as well as text documents. So, it will examine the behavior of users with respect to their data access privileges.
Who is it recommended for?
This service can be tailored to protect data according to HIPAA, PCI DSS, and GDPR requirements. The Teramind charge rate is levied per user per month – that is the end user in the business. So, it is a very scalable package that would be suitable for any size of business.
Pros:
- Great user interface, simple to navigate and learn
- Highly visual reporting and real-time monitoring
- Built with compliance in mind
- Goes beyond PII with options for actively monitoring and keylogging
Cons:
- Steep learning curve
Pricing:
Teramind offers four plans and there are two editions per plan, one for cloud and the other for on-prem.
- Starter – The cloud-based plan is $10/user/month and there’s a minimum of five users. The On-prem edition starts at $5/endpoint/month. The minimum is 10 endpoints per plan.
- UAM: The cloud edition starts at $20/83/user/month and there’s a minimum of five users while the on-prem edition starts at $10.42/month with a minimum of 10 endpoints.
- DLP: The cloud edition is priced at $25/user/month and there’s a minimum of five users. The on-prem edition costs $12.50/endpoint/month, and the minimum is 10 endpoints per plan.
- Enterprise: Contact sales for a custom quote
Demo and Free Trial: Click here for a live demo of Teramind and here for a trial version.
Thus, these are the best five PII scanning and data protection tools.
Conclusion
PII scanning tools are a must-have for today’s business environment as it helps businesses to straddle the worlds of compliance and data security. These tools allow you to safeguard your data from external hackers, insider threats, accidental loss, and intentional leaks. In addition, it helps your business to comply with an ever-growing list of regulations and standards.
The tools that we have described are comprehensive in every sense and offer the best possible protection for your data. They also offer fine control over your data access and visibility. That said, some tools have a few additional features, so it’s up to you to pick the one that best meets your business’ needs.
PII Scanning Tools FAQs
What is PII scanning?
PII scanning is the process of scanning files, databases, and other sources of data to identify and protect personally identifiable information (PII), such as social security numbers, credit card numbers, and addresses.
What are some common types of PII scanning tools?
Common types of PII scanning tools include data loss prevention (DLP) software, identity and access management (IAM) software, and security information and event management (SIEM) systems.
What are some best practices for PII scanning?
Best practices for PII scanning include identifying and prioritizing high-risk areas for scanning, implementing policies and procedures for handling sensitive data, regularly monitoring and reviewing scan results, and maintaining compliance with applicable regulations and standards.
How do PII scanning tools handle different types of data sources?
PII scanning tools can handle different types of data sources by using a variety of scanning techniques, such as keyword matching, regular expressions, and machine learning algorithms, to identify and protect sensitive data.
Can PII scanning tools be customized to fit specific organizational needs?
Yes, many PII scanning tools can be customized to fit specific organizational needs, such as by adjusting scanning policies and thresholds, configuring alerts and notifications, and integrating with other software systems.
What are some considerations when choosing a PII scanning tool?
Considerations when choosing a PII scanning tool include the level of automation and customization needed, the ability to handle different data sources and types of PII, and the scalability and performance of the tool.
What are some common use cases for PII scanning?
Common use cases for PII scanning include identifying and protecting sensitive data in databases, emails, documents, and other sources, complying with privacy regulations and industry standards, and ensuring that third-party vendors and partners are handling sensitive data appropriately.