File Integrity Monitoring (FIM) is an essential layer of your network’s defense mechanism as it helps to identify unauthorized access and malicious activities across your critical files. By implementing file integrity monitoring tools, you can reduce the chances of insider attacks and prevent any unwanted or accidental changes to essential documents and files.
Here is our list of the best File Integrity Monitoring (FIM) tools:
- ManageEngine ADAudit Plus – FREE TRIAL An activity monitoring tool that focuses on user actions on files and Active Directory objects and it includes compliance reporting. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine EventLog Analyzer – FREE TRIAL Handles log management, auditing, and IT compliance to provide insights into potential threats, so you can stop them before they turn into a full-fledged attack. Start a 30-day free trial.
- ManageEngine OpManager – FREE TRIAL Provides robust file integrity monitoring and real-time network insights, making it a comprehensive tool for IT management. Start a 30-day free trial.
- Site24x7 – FREE TRIAL This cloud-based platform includes a file integrity monitoring tool that tracks changes to critical files and directories in real time, ensuring system security and compliance. Start a 30-day free trial.
- SolarWinds Security Event Manager (SEM) This centralized FIM tool has advanced log management features that track and analyze your file system’s access and display the results in an intuitive dashboard.
- Datadog Security and Compliance Monitoring Continuously monitors files and their access and configurations to provide an additional layer of security for your organization.
- CrowdStrike Falcon FileVantage This file monitor is delivered from the cloud and can centralize the monitoring of multiple locations.
- Netwrix Auditor Detects security threats, proves compliance, and increases IT efficiency.
- Qualys FIM A cloud-based tool that specializes in monitoring integrity violations across your entire network in real-time, so you can address issues before they spiral out of control.
- OSSEC A popular open-source intrusion detection system, and it also comes with advanced file integrity monitoring.
- Trustwave Endpoint Protection Another comprehensive cloud-based security solution that delivers integrated protection against malware and other attacks on file systems.
- Fortra Tripwire Integrity Management A FIM that does not only generates alerts but also provides actionable intelligence that would make it easy to address the issue.
- Samhain File Integrity This host-based intrusion detection system combines file integrity monitoring with log file monitoring and analysis to give you a comprehensive view of the state of security within your organization.
File integrity monitoring tools and practices significantly reduce shutdowns to a system by identifying the possible threats, so the same can be mitigated at the earliest.
Another advantage of implementing FIM within your organization is compliance. For organizations that store or process credit card payments, FIM is a mandatory requirement to comply with the Payment Card Industry Data Security Standard (PCI DSS). For other industries, FIM is a requirement for many different standards as well.
The easiest way to implement FIM within your organization is to use tools geared specifically for this purpose. And this is also a challenge given the many tools that are available today. While choosing an FIM tool, make sure to run through its features to see if it’s a good fit for your organization. This is more important if you have hybrid environments, custom programs, and operate on limited resources as you don’t want the FIM solution to take up all your resources.
Based on these factors, we came up with the lightweight choices outlined above that work well across on-premises, cloud, and hybrid environments. Let us now explore the features of each of these tools to understand what is a good fit for your organization.
The Best File Integrity Monitoring (FIM) Tools
Our methodology for selecting file integrity monitoring tools and software
We reviewed various file integrity monitoring tools and analyzed the options based on the following criteria:
- Reporting and alerting features
- Ease of use and installation
- Integration support for other applications and platforms
- A facility to analyze file integrity over time
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
1. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is a compliance auditing system that lays down records for compliance auditing. The auditing process is intended to check the veracity of declarations made by a business in relation to the protection of sensitive data. In order to check on whether the data has been kept secure, the business needs to log all activity related to files. This is the purpose of the ADAudit Plus package.
Key Features:
- User profiles that establish a record of regular activity for each user account
- Anomaly detection for malicious activity
- Monitoring for account takeover and insider threats
- Detection for brute force account credentials cracking
- Compliance auditing for HIPAA, PCI DSS, GDPR, GLBA, SOX, and FISMA
- Compliance reporting templates
- Ransomware encryption warnings
- Alerts and notifications
- Formats to output to a SIEM
- Runs on Windows Server
Why do we recommend it?
ManageEngine ADAudit Plus is a user activity tracker that references Active Directory to compile information on each authorized user. The system looks for unusual activity that lies outside of the general pattern of work tasks usually performed by each user. The service also protects Active Directory records against unauthorized changes.
Who is it recommended for?
This package is a useful security service for any company, particularly those that store personally identifiable information. You should have access controls on all of your applications and files, which leaves insider threats and account takeover as the only security issues that you need to guard against.
Pros:
- Focused heavily on compliance requirements, making it a good option for maintaining industry compliance
- Preconfigured compliance reports allow you to see where you stand in just a few clicks
- Features insider threat detection – can detect snooping staff members or blatant malicious actors who have infiltrated the LAN
- Supports automation and scripting
- Great user interface
Cons:
- Better suited for larger environments
Pricing: ManageEngine doesn’t publish a price list, so you need to contact the Sales Department and request a quote.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top choice for monitoring and auditing Active Directory environments because it excels in both compliance and security. This tool is designed to ensure that your organization adheres to strict data protection regulations while also safeguarding against insider threats and unauthorized access.
ADAudit Plus offers robust reporting and alerting features that make it easy to monitor user activities and detect anomalies in real-time. We found the interface intuitive, making it easier to navigate through detailed audit logs and compliance reports. The system’s ability to automate processes and integrate seamlessly with existing infrastructure further enhances its value.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/products/active-directory-audit/active-directory-auditing-solutions.html
OS: Windows Server
2. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer is a log management, auditing, and IT compliance tool that provides an insight into the potential threats within an organization, so you can address them before they turn into an attack.
Key Features:
- Correlates log data with 30 predefined rules for extensive coverage
- Collects analysis and manages log data from over 700 sources
- Audits log data from perimeter devices as well
- Detects data thefts and attacks at the earliest
- Reduces the chances of downtime
- Comes with a custom log parser to quickly find the information you want
- Exports comprehensive compliance reports to other formats
- Comes augmented with threat intelligence
- Process log data at the rate of 25,000 logs per second
- Conducts quick forensic analysis to reduce the impact of a breach
- Automatically raises tickets in help desk consoles
- Speeds up incident resolution
Why do we recommend it?
ManageEngine EventLog Analyzer is a log server and SIEM service that provides compliance reporting. The service is able to protect files, providing alerts when any files or folders that are registered for protection are moved or updated. You would need to implement a data backup plan to restore files that have been changed.
Who is it recommended for?
This is a straightforward SIEM system and ManageEngine offers a more elaborate package, called Log360, which includes EventLog Analyzer for businesses that need more detailed activity scrutiny. The service includes compliance reporting for PCI DSS, GDPR, FISMA, ISO 27001, and SOX. You can prevent intrusion, thanks to the threat intelligence feed that provides an IP address blacklist.
Pros:
- Customizable dashboards that work great for network operation centers
- Multiple alert channels ensure teams are notified across SMS, email, or app integration
- Uses anomaly detection to assist technicians in their day-to-day operations
- Supports files integrity monitoring that can act as an early warning system for ransomware, data theft, and permission access issues
- Forensic log audit features enable admins to create reports for legal cases or investigations
Cons:
- Takes time to fully explore the entire ManageEngine ecosystem
Pricing: Contact the sales team for a custom quote.
Download: Start a 30-day free trial.
3. ManageEngine OpManager – FREE TRIAL
ManageEngine OpManager is a top-tier file integrity monitoring tool due to its advanced capabilities in tracking and recording changes to critical system files in real-time.
Key Features:
- File Integrity Monitoring: Continuously tracks and records changes to critical system files, ensuring data integrity and security.
- Customizable Dashboards: Allows for the creation of tailored dashboards to provide specific views of critical metrics.
- Real-Time Network Monitoring: Monitors network performance in real-time to quickly identify and resolve issues.
- Automated Alerts: Sends notifications based on predefined thresholds to promptly address potential problems.
- Application Performance Monitoring: Tracks the performance of various applications to ensure optimal functionality.
- Integration with Other Tools: Easily integrates with a variety of other IT management and monitoring tools.
- Scalability: Adapts to the needs of both small businesses and large enterprises.
- User-Friendly Interface: The interface is intuitive and easy to navigate, even for beginners.
Why do we recommend it?
ManageEngine OpManager is recommended for its robust file integrity monitoring capabilities, ensuring critical system files remain secure and unaltered. Its real-time network monitoring and customizable dashboards make it a versatile tool for proactive network and application management.
It leverages robust algorithms to detect unauthorized modifications, additions, and deletions, ensuring that any suspicious activity is promptly identified. This tool also integrates seamlessly with other security and IT management solutions, providing a comprehensive view of the system’s integrity. The customizable alerts and detailed audit logs enhance its effectiveness, allowing administrators to respond quickly to potential threats.
Additionally, ManageEngine OpM’s scalability and support for various environments, including Windows and Linux, make it suitable for organizations of all sizes. Its user-friendly interface and extensive reporting capabilities further solidify its position as a leading solution for maintaining data integrity and security.
Who is it recommended for?
This tool is ideal for IT administrators and security professionals who need to ensure the integrity of critical system files while maintaining optimal network and application performance. It’s also suitable for businesses of all sizes, from small startups to large enterprises, due to its scalability and extensive feature set.
Pros:
- Effective File Integrity Monitoring: Provides continuous tracking of changes to critical system files, enhancing security and data integrity.
- Highly Customizable: Offers extensive customization options for dashboards and reports, catering to diverse user needs.
- Real-Time Network Insights: Real-time monitoring allows for quick detection and resolution of network issues.
- Proactive Alerting System: Automatically triggers alerts based on set parameters, helping in rapid issue resolution.
- Comprehensive Application Monitoring: Ensures that critical applications are running smoothly with minimal downtime.
- Seamless Integration: Integrates well with other tools, enhancing overall IT management efficiency.
- Scalable Solution: Suitable for organizations of all sizes, allowing easy scaling as your business grows.
Cons:
- Learning Curve: The vast array of features can be overwhelming for new users.
Start by downloading a 30-day free trial.
4. Site24x7 – FREE TRIAL
Site24x7 provides a file integrity monitoring tool on its cloud platform of system monitoring and management services. The tool offers real-time tracking of changes to critical files and directories. It alerts IT teams about unauthorized modifications, deletions, or additions, ensuring proactive security management. By providing detailed reports, it helps organizations maintain compliance with regulatory standards and protect sensitive data.
Key Features:
- Tracks changes to files and directories as they happen, providing immediate alerts for any unauthorized modifications.
- Configurable notifications for specific file changes, deletions, or additions, ensuring rapid response to security threats.
- Monitors attributes like file size, permissions, content, and metadata to detect any alterations.
- Provides detailed reports on file integrity events, helping organizations track changes for security audits and compliance.
- Allows users to set specific monitoring policies based on critical files and directories for focused tracking.
- Establishes a baseline of file states for comparison, ensuring accurate detection of discrepancies and unauthorized changes.
- Automatically scans files and directories at scheduled intervals for unauthorized changes, reducing manual efforts.
- Maintains a history of all file changes and user activities, supporting forensic investigations and compliance audits.
- Offers a single platform to manage file integrity monitoring across multiple systems and locations.
- Helps meet compliance requirements for standards like PCI-DSS, HIPAA, and GDPR by maintaining file integrity reports.
- Ensures that alert data is securely transmitted, maintaining the confidentiality of critical security information.
- Integrates with other monitoring and management tools, providing a unified IT management ecosystem for enhanced security.
Why do we recommend it?
Site24x7 implements file integrity monitoring through real-time tracking, customizable alerts, and detailed reporting. It helps organizations proactively detect unauthorized file changes, ensuring system security and regulatory compliance. Its centralized management and integration with other IT tools make it an efficient solution for maintaining data integrity and supporting audits.
Who is it recommended for?
This tool is recommended for IT teams, security professionals, and compliance officers in organizations of all sizes that need to monitor and protect sensitive files and data. It is particularly beneficial for businesses in regulated industries, such as healthcare, finance, and retail, that must maintain strict compliance with standards like PCI DSS, HIPAA, and GDPR.
Pros:
- The platform offers a clean and intuitive interface
- Easy setup, configuration, and ongoing management
- Allows users to create customized monitoring policies for specific file types, folders, and system configurations
- Helps prevent potential security breaches and ensures that sensitive data is protected against tampering or accidental loss
Cons:
- Certain less common file types may not be fully supported for monitoring, limiting some use cases.
Pricing: The Infrastructure Monitoring plan starts at $9 perr month.
Download: Access a 30-day free trial.
5. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a lightweight and affordable security solution that watches out for any suspicious activity 24X7 and alerts you in real-time, so you can respond accordingly to reduce their impact.
Key Features:
- Automates compliance management with continuous risk management and monitoring
- Provides real-time and actionable insights from logs to handle security risks
- Audits logs on Azure AD to improve security practices
- Comes with advanced bot capabilities to provide situational awareness
- Provides centralized log management for granular control over file access
- Prevents cross-site scripting attacks
- Uses advanced cyber threat tools to protect your network
- Comes with database auditing tools to protect your databases from attacks
- Protects sensitive information present in files
- Tracks file and directory access
- Uses a file integrity checker to detect malware threats
- Meets compliance standards such as PCI DSS, HIPAA, FISMA, NERC CIP, and more
- Comes with monitoring templates that can be customized to meet your needs
- It can be set up with minimal configurations on Windows OS
- Works well on individual nodes as well as on connector profiles
- Allows you to customize the access criteria for your files and folders
- Keeps track of file changes in an intuitive dashboard
- Sends alerts when unusual file changes occur
Why do we recommend it?
SolarWinds Security Event Manager is a large SIEM tool that includes a number of file integrity monitoring features. The tool also logs access to registry settings and Active directory records. The tool coordinates with the IDS systems and anti-malware to spot irregular file access events and can also trigger automated responses to threats.
Who is it recommended for?
This package is a good choice for any company but it will probably be out of reach for small companies. The system will particularly interest companies that need to comply with data protection standards because it provides compliance auditing and reporting for PCI DSS, NERC SIP, HIPAA, FISMA, and SOX.
Pros:
- Enterprise-focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Historical analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product built for professionals, requires time to fully learn the platform
Pricing: Starts at $2,613 – see https://www.solarwinds.com/security-event-manager/registration
Download: You can test-drive SolarWinds Security Event Manager for a fully functional 30-day free trial.
6. Datadog Security and Compliance Monitoring
Datadog’s security and compliance monitoring continuously stays on top of misconfigurations, file and folder access, and compliance drifts to ensure that you have an additional layer of security besides meeting the compliance requirements.
Key Features:
- Identifies misconfigurations that can compromise your security
- Sends notifications to the concerned people in case of vulnerabilities
- Helps engineers to address security issues proactively
- Provides end-to-end visibility on cloud environments
- Tracks all cloud-native resources such as storage buckets, load balancers, and Kubernetes
- Identifies compliance drifts and raises alerts right away
- Discovers all assets and their configurations
- Ensures continuous compliance
- Collects local configuration from servers and containers
- Comes with easy and custom governance policies
- Integrates and automates infrastructure monitoring
Why do we recommend it?
Datadog provides file integrity monitoring in its Cloud Workload Security package. This is a new service from the Datadog platform that will track cloud platforms and containers and the applications and files that they host. The system watches over file access events and enables you to define which applications can be used for data access.
Who is it recommended for?
This service is designed for monitoring cloud systems and so you wouldn’t opt for it if you keep all of your sensitive data on your own servers. However, increasingly, businesses are moving all of their systems to the cloud and so the audience for this package is growing all the time.
Pros:
- Supports live log collection as well as long-term archival options for SIEM solutions
- Can monitor both internally and externally giving network admins a holistic view of network performance and accessibility
- Allows businesses to scale their monitoring efforts reliably through flexible pricing options
Cons:
- Would like to see a longer trial period for testing
Pricing: Datadog offers many pricing plans. For example, its Infrastructure plan offers three editions such as:
- Free – $0
- Pro – $15 per host per month
- Enterprise – $23 per host per month
When it comes to log management, the Ingest starts at $0.10 per ingested GB, and the Retain or Rehydrate plan starts at $1.70 per million log events per month.
The APM and Continuous Profiler plan starts at $31 per host per month for just the APM and $40 for both the APM and Continuous profiler.
The real-user monitoring starts at $15 per 10k sessions per month, the database monitoring starts at $70 per database host per month, and incident management begins at $20 per user per month.
Download: Click here to start a 14-day free trial.
7. CrowdStrike Falcon FileVantage
CrowdStrike Falcon FileVantage is a file monitoring service that records every action on files and registered the user account involved in that activity. This system is part of the CrowdStrike Falcon platform of cybersecurity tools and can integrate with other systems, such as the Falcon X threat intelligence feed.
Key Features:
- A centralized system that is delivered from the loud and can track activity on files located on multiple sites.
- File activity statistics on the dashboard summary page
- The option of a threat intelligence feed
- A system to define a security policy
- Compliance with PCI DSS, CIS, and SOX
- Option to integrate with Falcon Insight EDR or Falcon XDR
Why do we recommend it?
CrowdStrike Falcon FileVantage is a cloud-based service that is tied to compliance management. The dashboard for the system raises alerts for access events to registered sensitive files and records any changes. The subsequent actions from here are up to the system manager but they can be set up to trigger automated responses.
Who is it recommended for?
The tool focuses on files that store sensitive data. It won’t log actions on all files. So, this is specifically aimed at businesses that handle PII and need to implement compliance auditing and reporting. The FileVantage service works best as an add-on to the main security systems from CrowdStrike, such as Falcon Insight XDR.
Pros:
- Excels in hybrid environments (Windows, Linux, Cloud, BYOD, etc)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Lightweight agents take up little system resources
Cons:
- Would benefit from a longer trial period
Pricing: The Falcon Prevent platform pricing starts at $8.99 per endpoint per month. Access a 15-day free trial.
Download: CrowdStrike Falcon FileVantage is a cloud service so there is no download.
8. Netwrix Auditor
Netwrix Auditor is a comprehensive tool for detecting security threats and improving compliance with standards. It also increases the overall efficiency of IT teams and optimizes IT operations.
Key Features:
- Identifies gaps in your monitoring and infrastructure to help you fix them at the earliest
- Ensures timely detection of threats
- Its automated actions increase the accuracy of investigations
- Acts as a centralized platform to provide all the information you need regarding security
- Provides a consolidated audit trail
- Mitigates weak spots within the organization
- Automates data discovery and classification
- Generates alerts on threat patterns
- Improves the detection of sophisticated threats
- Helps to handle operational challenges related to security
Why do we recommend it?
Netwrix Auditor is a platform of system documentation and risk assessment tools that are useful for compliance management. The Auditor both checks security risks and identifies suspicious settings that could indicate the presence of an advanced persistent threat or an insider threat. It implements file integrity monitoring for system and configuration files.
Who is it recommended for?
This package is a type of vulnerability manager but it is also focused on compliance management. It generates logs for compliance auditing and reporting which show that work was implemented to ensure that all risks are uncovered and that steps were taken to reduce those risks. This is an on-premises package for Windows Server.
Pros:
- Offers detailed auditing and reporting that helps maintain chain of custody for sensitive files
- Offers hardware and device monitoring to track device health alongside security
- Allows sysadmin to implement automated remediation via scripts
- Integrates with popular help desk platforms for automatic ticket creation
Cons:
- The trial could be a bit longer
- Alerting could be made more intuitive
Pricing: Click here to request pricing.
Download: Click here for a 20-day free trial.
9. Qualys FIM
Qualys FIM is a cloud-based tool that detects violations on file integrity and alerts accordingly. All this is done in real-time to give you the best opportunity to protect your critical files and objects.
Key Features:
- Comes with out-of-the-box monitoring profiles
- Complies with PCI DSS specifications
- Automatically generates alerts to kickstart the remediation process
- Continuously monitors files and registries
- Captures critical events and sends them to the Qualys Cloud Platform for analysis and display
- Enriches event data with Threat Intelligence to give you a comprehensive idea of the problem
- Makes it easy to scale up or down depending on your business requirements
- Provides unified security capabilities
- Uses a real-time detection driver to monitor changes, so the performance impact is minimized
- Works well across diverse on-prem and cloud environments
- Captures advanced insights into the file changes, including the users who made the changes
- Can be used on both Windows and Linux systems
- Whitelists security patches and authorized changes
- Easy to export to the ELK stack for further correlation
- Reports vis native Splunk integration
Why do we recommend it?
Qualys FIM is a hybrid package and it can protect hybrid environments. The server for this tool is cloud-resident but the system installs agents on your servers for local searches. These agents are available for Windows and Linux. The service can also scan files hosted on cloud platforms. The package includes protection templates that tailor the file integrity monitoring for different data types.
Who is it recommended for?
This package is particularly useful for businesses that have to follow specific data protection standards, such as PCI DSS. The system records any event that takes place on a protected file, including the person who made the change. Alerts and automated responses mean that changes can be rolled back quickly where necessary.
Pros:
- Supports continuous monitoring and scanning for vulnerabilities
- Offers one-click remediation automation
- Includes built-in security policies
- Great user interface
Cons:
- Not the best option for smaller networks
Pricing: Contact the sales team for a custom quote.
Download: Click here to start a free trial.
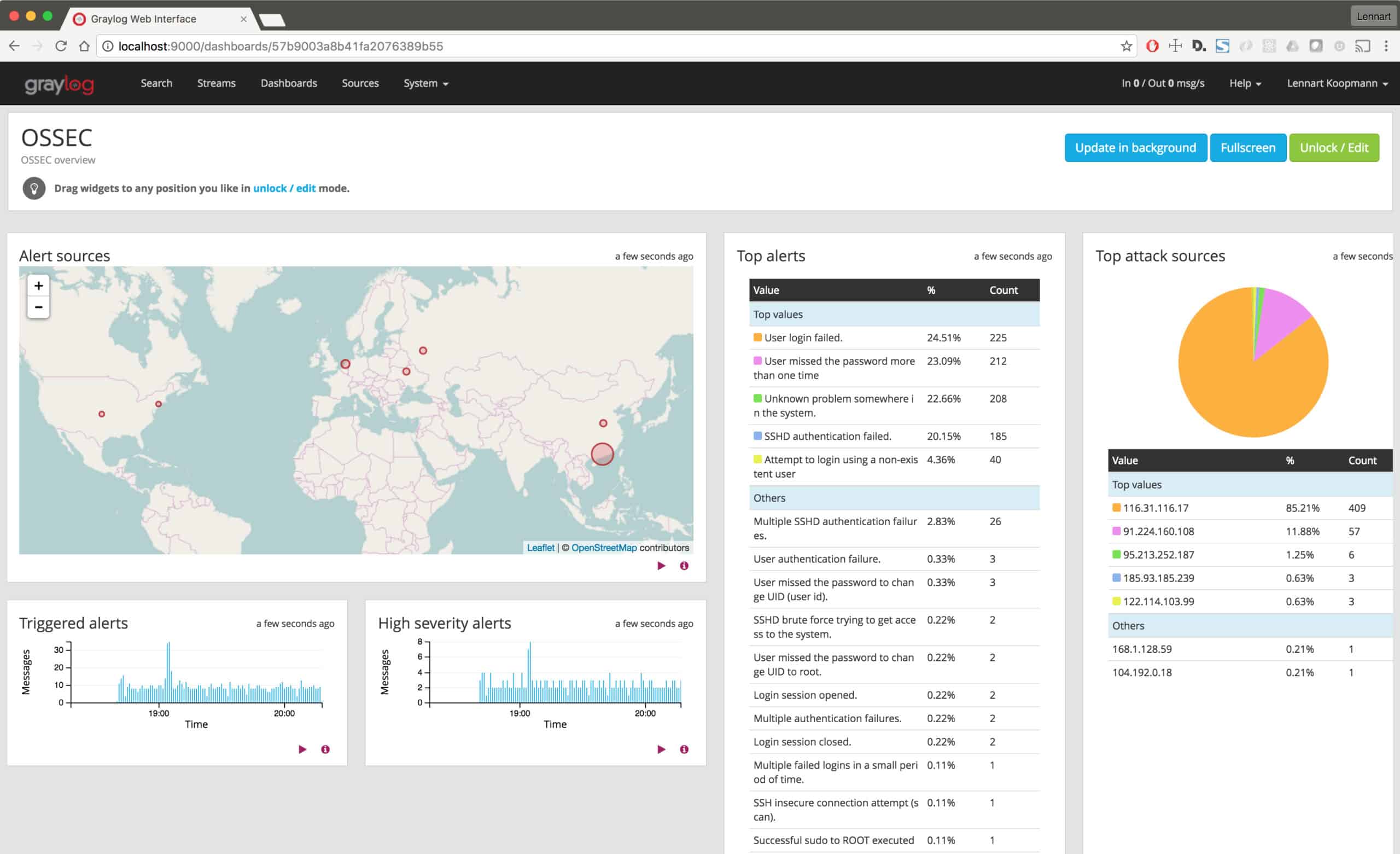
10. OSSEC
OSSEC is an open-source host intrusion detection system with file monitoring capabilities and other advanced features, especially in its advanced version.
Key Features:
- Comes with extensive configuration options to meet your security needs
- Enables you to add custom rules and scripts to describe the actions for each event. They will be triggered when the programmed event occurs
- Works well across multiple platforms such as Linux, Solaris, AIX, HP-UX, Windows, Mac, and Vmware ESX
- Helps to meet compliance requirements such as PCI DSS
- Detects unauthorized file system changes and sends alerts accordingly
- Identifies malicious behavior quickly so that you can remediate them at the earliest
- OSSEC+ version offers advanced capabilities such as machine learning, real-time community threat sharing, ELK stack, and more
Why do we recommend it?
OSSEC standard for Open Source HIDS Security. This is a free tool and iyt is highly respected. The system is managed by Atomic Corp, which has built its own commercial version. Now there are three versions of OSSEC to consider: OSSEC, OSSEC+, and Atomic OSSEC. The tool can be set up to implement FIM for system registries as well as files.
Who is it recommended for?
All versions of OSSEC include its file integrity monitoring feature. It can be set up to store a shadow copy of any file when it is changed, making it easy to restore its original values if the change is discovered to have been unauthorized. OSSEC installs on Linux and can manage files on Windows computers via an agent.
Pros:
- Completely free and open-source
- Utilizes checksums to verify log and file integrity
- Supports root account monitor on Unix/Linux systems
- Strong community support offering new templates and scanning profiles
Cons:
- Reliant on the community for support
- Could use better reporting and visualization features
Pricing: Both OSSEC and OSSEC+ are free, but the latter requires you to register. If you need advanced features and enterprise-level monitoring, opt for Atomic OSSEC for Enterprise.
Download: Click here to download OSSEC.
11. Trustwave Endpoint Protection
Trustwave Endpoint Protection is a cloud-based monitoring solution that provides integrated file monitoring and simplified compliance management for organizations of all sizes.
Key Features:
- Checks for additions and deletions in sensitive files
- Monitors modifications in stored data
- Indicates the presence of malware and other malicious programs within a network
- Informs users of unauthorized access to files and applications
- Reduces costs for organizations as it is an end-to-end solution
- Handles configuration and monitoring of all assets
- Generates advanced reports
- Audits what file resources were changed
- Meets compliance needs and auditing requirements
- Complements and extends FIM to include SIEM
Why do we recommend it?
Trustwave is evolving and now highlights is consultancy services more than its software products. The company offers a Managed Detection and Response service, which is a Security Operations Center for hire. This service will provide the management of all of your security software and provides cybersecurity experts for threat assessments.
Who is it recommended for?
The Trustwave solution is ideal for businesses that don’t have their own cybersecurity team. The company also offers a Co-Managed SOC package, which will appeal to companies that have some technician staff with cybersecurity knowledge but not enough to keep on top of all potential risks.
Pros:
- Simple and easy-to-use interface
- Supports robust file audits and reporting modules
- Supports natives alerting for file access and other events
Cons:
- Must contact for pricing
Pricing: Contact the sales team for a quote.
Download: Click here to get started.
12. Fortra Tripwire Integrity Management
Fortra Tripwire Integrity Management‘s capabilities not just identifies changes to the file system but also adds business context to the data to make it intelligent and actionable.
Key Features:
- Focuses on the root cause of problems for quick resolution
- Addresses trouble spots with actionable intelligence
- Provides deep insights into the issue
- Validates whether a change is a planned one to save time for you
- Reduces your signal to noise ratio
- Continuously captures file changes in real-time, so the chances for a miss is meager
- Its advanced automation capabilities reduce workload for organizations
- Integrates with existing ticketing solutions
- Its automated alerts trigger user-tailored responses when changes reach a severe state
- Integrates well with your existing security controls
- Makes it easy to manage the overall infrastructure of your organization
Why do we recommend it?
Fortra Tripwire Integrity Management is packaged in suites of tools, so you don’t just get FIM but also complementary units that enhance data protection. For example, the Enterprise edition includes security configuration management, providing threat detection as well as live file change tracking, while Tripwire IP360 implements risk assessment and vulnerability management with the FIM.
Who is it recommended for?
The Tripwire system is particularly useful for businesses that need to implement a specific data protection standard. The tool can be calibrated to manage data of a specific type, such as credit card data for PCI DSS compliance. This system is an on-premises software package for Windows and RHEL.
Pros:
- Supports real-time monitoring
- Can scan for vulnerabilities as well as detect and alert to config changes
- Better suited for larger networks
Cons:
- No free version – only free demo
- The interface could use improvement
Pricing: Click here to get a quote.
Download: Click here to schedule a demo.
13. Samhain File Integrity
Samhain File Integrity is a host-based intrusion system that comes with advanced capabilities for file integrity monitoring and log file monitoring and analysis.
Key Features:
- Client-server architecture supports central logging and storage of information for better analysis and control
- Comes with a web-based management console to monitor client and server activity
- Supports flexible logging across multiple applications, each of which can be configured differently
- Offers PGP-signed database and configuration files
- Supports a stealth mode
- Comes with rootkit detection, port monitoring, detection of rogue SUID executables, and more to protect your file system from unknown attacks
Why do we recommend it?
Samhain is a file integrity manager and intrusion detection system. The FIM works through checksum calculations, so it is able to see when a file has changed but not what has changed within it. Thus, it would be necessary to combine this tool with a shadow save or backup system to enable files to be restored.
Who is it recommended for?
Samhain is a free tool and it has been around for a long time, so it has gathered a lot of adherents. The tool is community supported, which might be a problem for companies that have liability insurance that requires the use of software with professional support. The software for this system runs on Unix and Linux.
Pros:
- Free open-source tool
- Can detect rouge processes as well as intrusions from log files
- Can monitor user access rights to detect privilege escalation and insider threats
Cons:
- No paid support options
- Not available for Windows operating systems
- Interface feels outdated and not easy to use
- Lacks robust community found in more popular open-source NID tools
Pricing: 100% FREE
Download: Click here to download Samhain.
Conclusion
To conclude, file integrity monitoring systems are an essential part of your organization’s security as they ensure that your sensitive files and the information contained in them are safe from insider and outside attacks. Therefore, it is an essential layer of defense in your organization’s security and is indispensable for every organization.
We have listed down some of the best FIM tools in this post, and we hope these help you decide the appropriate tool for your organization’s needs.
File Integrity Monitoring Tools FAQs
What is File Integrity Monitoring (FIM)?
File Integrity Monitoring is a security measure that monitors and reports on changes made to files on a system or network.
Why is FIM important?
FIM is important because it helps identify unauthorized changes to files, which can indicate a security breach or malware infection.
What types of files can be monitored using FIM?
FIM can monitor any file on a system or network, including system files, configuration files, and user-generated files.
What are some common use cases for FIM?
Common use cases for FIM include compliance monitoring, malware detection, and forensic analysis.
How does FIM work?
FIM works by comparing the current state of a file to a known good state. If any changes have been made to the file, FIM will generate an alert.
What are some common FIM tools?
Common FIM tools include Tripwire, OSSEC, and McAfee File Integrity Monitor.
What types of changes can FIM detect?
FIM can detect changes such as file creation, modification, and deletion, as well as changes to file permissions and access control lists.
What are some best practices for configuring FIM?
Best practices for configuring FIM include establishing a baseline of known good files, configuring alerts for specific types of changes, and limiting access to FIM data.
How can FIM help with malware detection?
FIM can help with malware detection by identifying changes to files that may be caused by malware, such as the creation of new files or modifications to system files.