Data breaches have become more common than we’d like, and this frequency is attributed to a wide gamut of reasons that span from sophisticated strategies used by hackers to poor security practices of organizations.
One technology or practice that’s seen as a key strategy to protect your data is encryption. According to the Ponemon Institute, robust encryption strategies help businesses to save an average of $1.4 million per attack. But at the same time, not all organizations currently use encryption and this is evident from the fact that more than seven million unencrypted records are compromised every day.
There are many reasons for this gap in understanding the benefits and implementing them. In this article, we will focus on the implementation aspect. Encryption is often seen as an expensive and arduous process, but that’s not true, thanks to the availability of endpoint encryption software solutions.
What are Endpoint Encryption Software Solutions?
Endpoint encryption software protects your data at the endpoints where they are accessed. What this essentially means is that a user who wants to access data must have the decryption key to decrypt the data and use it. This mechanism weeds out random hackers because they can’t use the data even if they manage to hack into the system. It also ensures that only authorized people who have a valid decryption key can access the data from these systems.
Many endpoint encryption software solutions are available today, and here’s a brief look at some of your top choices:
- Symantec Endpoint Encryption This tool encrypts all files on the hard drive to provide high levels of security for your information. It can also encrypt hard drives and removable media and supports a wide range of operating systems such as Windows and Mac.
- Virtru An advanced data encryption platform that keeps your data safe at all times, regardless of where it is stored and how it is shared or transferred.
- Sophos Central Device Encryption This is full-disk encryption software that works well on both Windows and macOS. Its web-based management eases the setup and maintenance processes as well.
- Check Point Endpoint Media Encryption and Port Protection This tool offers centrally enforceable encryption of all drives and removable media to protect your sensitive data from losses and thefts.
- Trend Micro Endpoint Encryption This platform encrypts data across a wide range of devices, including removable media, to prevent unauthorized access to your sensitive data.
Let’s take a detailed look at each of these tools to help you make an informed buy decision.
1. Symantec Endpoint Encryption
Symantec Endpoint Encryption protects the sensitive information stored across your hard drives and removable media. As a result, there is a lesser risk of data theft and loss.
Features
Below are some of the salient features related to encryption and data security.
- Protects Customers’ Data One of the biggest security requirements of most organizations is to protect customers’ data and privacy to reduce the impact of a potential data breach. Using PGP technology, Symantec ensures that customers’ sensitive data is not exposed to unauthorized users, even in the event of a data breach.
- Compliance An integral part of security is compliance with the local laws and industry regulations such as PCI-DSS, HIPAA, GDPR, and more. Many times, organizations must have a mandatory encryption system in place to protect customers’ data. Further, these organizations have to inform the government and regulatory bodies in the event of a data breach. However, if they have encryption systems in place, these organizations don’t have to disclose a breach, which in turn, can save their reputation and possible fines.
- Strong Cryptographic Standards Symantec uses FIPS 140-2 encryption, an advanced cryptographic algorithm that uses both symmetric and asymmetric techniques to protect sensitive data. This encryption is also mandated by many governments and industry standards.
- Easy to Use Despite being so advanced, Symantec is simple to use from an end user’s standpoint. All that users have to do is just enter the passphrase once and the underlying single sign-on technology validates the user. This eliminates the need to enter the passphrase multiple times for authentication. You can even use smart cards for seamless encryption and decryption processes.
- Multiple Recovery Tools One of the biggest downsides to encryption is the loss of passphrases. But the good news with Symantec is that it allows you to recover your passphrase in multiple ways. You can choose to set up localized questions and answers and use them to recover or you can do so through a web help desk after authenticating your identity.
Other than the above features, Symantec is highly flexible and scalable and comes with a robust reporting engine for generating reports for external and internal audits.
Pros:
- Takes a forensic level approach to identity, blocking, and documenting threats
- Highly flexible – available on-premise or as a cloud-based service
- Uses SIEM features to ingest information from across the network to identify threats from anywhere
- Includes advanced threat detection tools – ideal for manual investigations
Cons:
- Would like to see more data visualization options
Pricing
You can buy this product through a partner or distributor. Click here to find someone in your city.
Downloads/Free trials
There are no downloads or free trials at the time of writing this piece.
2. Virtru
Virtru is a comprehensive data protection platform that uses encryption to protect your data both at rest and during transit. It also works well with Google Workspace, Microsoft 365, and other SaaS apps and platforms.
Features
Let’s now look at some of Virtru’s features pertaining to data encryption.
- Single, Unified Framework Virtru is a single and unified framework that works well across different frameworks, platforms, and environments. This means you can encrypt your data and keep it safe, even if it travels through custom apps, SaaS, cloud, emails, and more.
- Simple to Use Research shows that most data breaches involve some form of human error. A good way to avoid these errors is to make encryption an intuitive part of a user’s workflow, and that’s exactly what Virtru does. The encryption is automatic for your sensitive data, and users are not expected to do anything. In turn, this automation greatly reduces the errors.
- Secure Data on Google Workspace Virtru works across the entire Google workspace to secure your data across every component such as Docs, Sheets, Gmail, and more. Every file and email stored on the Google Workspace is encrypted, so the chances of a breach reduce greatly. You can even use your encryption keys to keep your private information secure on the Google Cloud Platform.
- Works well with Microsoft Like Google, Virtru also encrypts data on the Microsoft platform. So, all enterprise applications, emails on Outlook, and all files sent and received are encrypted. You can even use the control information to trace contacts, plan resources, and more.
- Compliance Virtru has all the features and reports needed to comply with leading industry specifications such as HIPAA, GDPR, ITAR, CCPA, FERPA, and more. It generates the reports you need for auditing as well.
Overall, Virtru is a handy endpoint encryption tool as it works well not just with your on-prem infrastructure, but also with Google Workspace and Microsoft 365. This way, all sensitive information will be safe regardless of where and how your employees access them.
Pros:
- Simple management console
- Flexible pricing – affordable for most businesses
- Supports Google Cloud workspace
- Detailed compliance features and options
Cons:
- It can take some time to fully explore all features and options
Pricing
Virtru offers three pricing plans:
- Starter – $79/month. Ideal for small teams that have to meet compliance requirements.
- Business – $249/month. A good choice for large teams and enterprises that want to secure their data.
- Enterprise – Custom quote. Ideal for large companies that are looking for advanced data security solutions.
Demo
Click here to book a demo.
3. Sophos Central Device Encryption
Sophos Central Device Encryption is a full-disk encryption tool that is compatible with both Windows and macOS. It allows you to manage both Windows BitLocker and macOS FileVault encryption systems.
Features
Here’s a look at the features of Sophos Central Device Encryption.
- Full Disk Encryption The highlight of Sophos is its full-disk encryption feature as it protects both your data and the devices that store or use them. Further, it comes with a password-protected HTML wrapper that ensures that only authorized users can access a document or file.
- Simple to Use Sophos Central Device encryption is simple to use and quick to set up. It entails no cumbersome server setups or configurations, so you can start using it within minutes. More importantly, its self-service portal helps to reset passwords and fix other minor issues related to devices. This reduces the workload on IT teams and at the same time, resolves your issues faster.
- Control and Visibility Sophos provides admins with the control and visibility they need to manage devices across the entire infrastructure. You can get all the information you need about disk usage, encryption methods, and other pertinent information needed to understand who has accessed devices, what data was accessed, and more. All this information can be used to reduce the chances of internal threats and at the same time, understand and plug-in vulnerabilities.
- Compliance The work-from-anywhere culture has made it difficult to secure devices and meet the necessary compliance. This is where Sophos can help as it can be installed across devices to encrypt information and the same can be used to increase compliance. Overall, Sophos is a comprehensive tool that encrypts your sensitive data and acts as the first line of defense in the event of an attack.
Pros:
- Leverages machine learning and artificial intelligence to stop new and evolving threats
- Offers protection against fileless malware and ransomware
- Users can implement automation to stop threats, or immediately escalate issues
- Scans external devices as soon as they’re plugged into the computer
Cons:
- Better suited for small to medium-sized companies
Pricing
The pricing structure is simple and is based on your specific needs. Click here to contact the sales team for a custom quote.
Free Trial
Click here for a free trial.
4. Check Point Endpoint Media Encryption and Port Protection
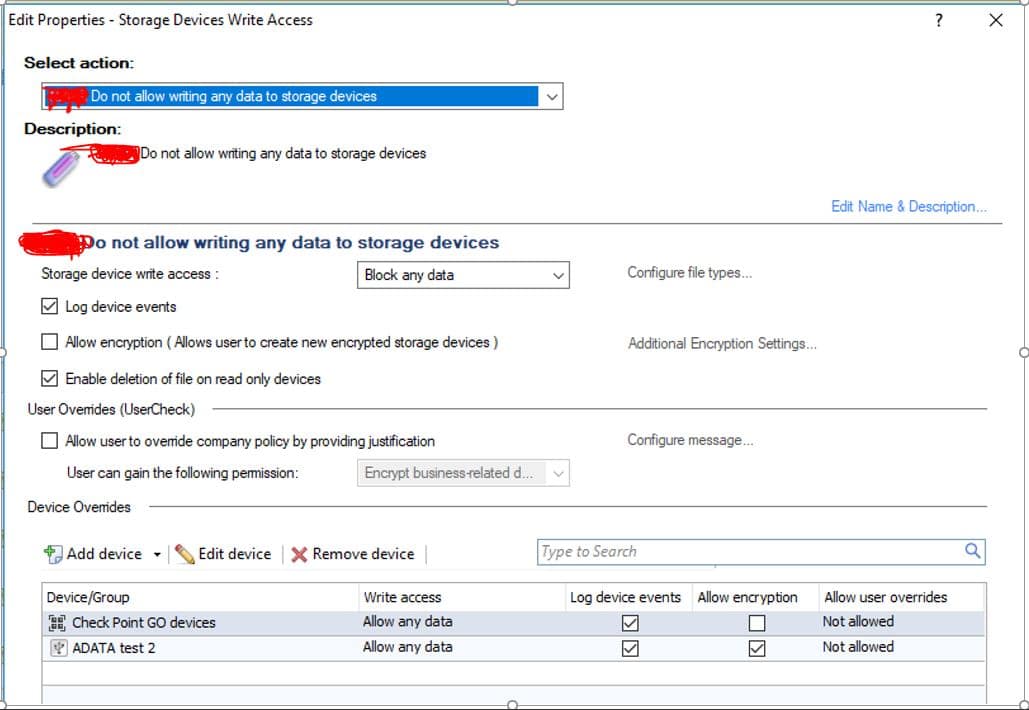
Check Point Endpoint Media Encryption and Port Protection helps you to centrally enforce encryption on all devices, removable media, and ports. This ensures that your data is not lost or stolen.
Features
Below is a set of important features related to encryption and data security.
- Comprehensive Data Protection CheckPoint provides comprehensive data protection across your entire infrastructure. Specifically, it encrypts the data stored on removable devices and hard drives, so it is of no use, even if the data is stolen by unauthorized users. It even encrypts data on CDs and DVDs that were burned from endpoint devices.
- Improves Operational Efficiency This tool improves the operational efficiency of your devices as it consumes minimum memory and processing resources. Further, the scan times are quick, which also means optimum resource usage.
- Granular Control Your employees can have granular control over device access settings and usage. You can also customize the configuration settings for removable media and ports. Moreover, all these devices, endpoints, and ports can be managed centrally through a single dashboard. Another advantage is that you can set usage limits for employees based on their job profile and department, and this ensures that no unauthorized user accesses your data. Further, you can track which employee accessed which data, and this can help with tracing as well.
- Logs and Alerts Check Point logs all access information related to devices, endpoints, and ports, so you can refer to them when needed. All this information is stored centrally to help you quickly find what you want. Based on this, you can also set custom alerts for different situations, and these can be sent through multiple channels such as email, SMS, and more.
In all, this is an advanced tool that encrypts data across all ports and endpoints, and with it, minimizes data theft and loss.
Pros:
- Leverages artificial intelligence to detect and prevent cyberattacks
- Offers bot protection by continuously monitoring the threat landscape
- Provides ransomware detection and phishing protection
- Works well on both smaller networks and enterprise environments
Cons:
- It can take time to fully explore and configure all of the settings available on the platform
Pricing
Contact the sales team for a custom quote. You can also find a local partner in your city to buy.
Free Trial
Click here for a free trial.
5. Trend Micro Endpoint Encryption
Trend Micro Endpoint Encryption is an advanced tool that encrypts your data across different devices. It also supports enterprise-wide, full-disk, and removable media encryption to keep your data safe and secure at all times.
Features
Read on to know how Trend Micro Endpoint Encryption can protect your data.
- Supports a Wide Range of Devices Trend Micro works well on a wide range of devices, so your employees have the flexibility to install them on any device they use. In particular, it provides extensive visibility into Microsoft BitLocker and Apple’s FileVault – the two most popular tools used for enforcing encryption across devices.
- Streamlines Authentication Trend Micro offers a lot of flexibility when it comes to streamlining authentication and enforcing policies in this regard. It also integrates with Active Directory and supports Multi-factor Authentication (MFA) where required. All this means you can update authentication policies across all devices for uniformity. At the same time, you can configure lockouts and failed password attempts to protect against unauthorized access. Lastly, you can choose to wipe out data remotely on lost and stolen devices.
- Simple to Use A salient feature of this tool is that it is complex enough to provide overarching protection and at the same time, it can be easily managed through a single console. The advantage is that you can centrally manage users and devices and also, simplify access to the existing IT infrastructure.
- Reporting and Auditing This tool enables you to use policy-based encryption to enforce regulatory compliance. It also provides an audit trail that can help with meeting compliance standards. Real-time auditing and unified policy deployment are the other advantages that come with this tool.
Overall, Trend Micro Endpoint Encryption is a handy tool to streamline access to your IT infrastructure and meet mandatory compliance requirements.
Pros:
- Can encrypt virtually all hard drives and removable media
- Centralized management for a simple view of your device security
- Offers advanced reporting capabilities as well as automated audits
- Is FIPS 140-2 certified
Cons:
- Better suited for larger networks
Pricing
Click here for a custom quote.
Free Trial
Click here for a free trial.
Thus, these are some of the popular endpoint encryption tools available today. We hope this information comes in handy to decide on the appropriate tool for your needs.
Final Thoughts
To conclude, endpoint encryption tools are those that encrypt data across all devices and ports in your IT infrastructure to ensure that your data is not accessed by unauthorized users. Needless to say, these tools greatly reduce the chances of data loss or theft.
There are many endpoint encryption tools available today and this article has a detailed explanation of five tools that are known for their comprehensiveness, ease of use, and effectiveness.
Feel free to check out our other guides too!
Endpoint Encryption Software FAQs
What are some common features of endpoint encryption software?
Common features of endpoint encryption software include full disk encryption, file and folder encryption, device control, policy management, and remote wipe capabilities.
How does endpoint encryption work?
Endpoint encryption works by encrypting data stored on the endpoint device using cryptographic algorithms that scramble the data in a way that can only be unscrambled with the correct encryption key.
What are some of the benefits of endpoint encryption?
Some benefits of endpoint encryption include improved data security and privacy, compliance with regulatory requirements, and reduced risk of data breaches and data loss.
What are some common use cases for endpoint encryption?
Common use cases for endpoint encryption include protecting confidential data on laptops and mobile devices, securing data on endpoints used by remote workers, and compliance with data protection regulations.
What types of data can be encrypted with endpoint encryption software?
Endpoint encryption software can be used to encrypt a wide range of data types, including files, folders, databases, and entire hard drives.
How does endpoint encryption software protect against insider threats?
Endpoint encryption software can protect against insider threats by preventing unauthorized access to sensitive data stored on endpoints, and by providing audit logs and monitoring tools that can be used to detect and investigate suspicious activity.