We are frequently required to let another person use either our laptop or our personal computer. A person who is malicious and possesses a pen drive that is infected with viruses and other malicious files can inject these malicious files into the system, which can cause damage to the device.
Additionally, someone who is malicious can steal our important documents through the use of a pen drive. When it comes to the safety of our information, we can never take enough precautions. To safeguard our device from viruses and any other vulnerabilities, disabling the USB Ports is a very good option that we may utilize.
By preventing unauthorized devices from accessing endpoints and sensitive data, a USB lockdown program, which is also referred to as USB blocking software, can assist businesses in preventing the leakage of sensitive data. A USB blocker prevents data from being copied onto removable devices that cannot be verified, providing an extra layer of security.
And if we ever find ourselves in a situation where we need to use USB Devices through USB Ports, we can enable these ports by employing a variety of methods, such as the device manager, the registry editor, or any other third-party software.
Some of you may have encountered a situation in which the computer at your place of employment or school did not respond when you attached a USB drive to it. This is because the administrator has deactivated the USB ports; as a result, USB drives will not be recognized.
Disable USB Ports using Device Manager
Additionally, using the Device Manager to turn off the USB ports is a relatively basic process. To access the Device Manager, right-click the Start menu and select the option. Once the window has appeared, select the Universal Serial Bus controller from the menu that displays. (This is the final possibility on the list.) You also have the option to choose the uninstall option for the USB drive. If you do this, Windows will be unable to locate the drivers for the USB drive if anyone inserts one.
Through the use of Device Manager, you can disable/enable or disable the USB ports. If you want to prevent other people from accessing your computer to transfer data or if you want to utilize your USB device on the computer you use at work, then follow these instructions to disable the USB drivers on your computer:
- Step 1: Launch the Device Manager by going to the Start menu and entering “devmgmt.msc” into the Search box.
- Step 2: Select the Universal Serial Bus Controllers menu option with a click. You will now be presented with a list of available USB ports.
- Step 3:With the mouse’s right button, select the USB port to either disable or enable it.
How to Disable USB Ports through the use of Group Policy
You may find a tutorial on the CurrentWare blog that will provide you with in-depth instructions on how to utilize a Group Policy Object to prevent employees from using USB devices. The guide can be accessed by clicking here.
Even while implementing group policies is a helpful method for controlling the use of USB storage devices inside an organization, some drawbacks must not be ignored and should be brought to everyone’s attention.
When using a GPO, it can be difficult for the average user to implement specific USB restrictions that apply to different departments and users. To administer at a large scale, you will also need expertise with Active Directory.
Because dedicated software for blocking USB mass storage devices is straightforward to handle, such as the AccessPatrol program, it is possible to delegate the modification of policy changes to individuals who are less knowledgeable about technology. When employing specialist software to prevent USB connections, the management of specific USB rules for particular users is simplified and made more intuitive.
How to Disable USB Ports so they can only be used with Mass Storage Devices
You can do this with AccessPatrol if you want to disable only the USB ports that are used for mass storage (for example, without limiting the use of keyboards, mice, and other USB devices that you want to use).
When you disable USB ports using AccessPatrol, the software will make a distinction between USB mass storage devices and other peripherals, such as keyboards and mice, before turning off the ports. In addition to that, it offers granular management over various portable storage devices including SD Cards, mobile phones, and external hard drives.
Because it can differentiate between mass storage and keyboards, AccessPatrol is the most effective software available for banning USB mass storage devices in a business setting.
Disable or enable a USB Drive using a Registry
If you want to try to disable a USB drive via utilizing the registry, you can do so by typing “run” into the search box (though maybe first take a look at our guide on creating a backup of your registry). Once it does, start typing regedit into the box that comes up, and the registry editor should display. When you are in the Registry Editor, navigate to the following directory:
- Double-clicking “Start” in the pane on the right will open the “Edit DWORD (32-bit)” box for you to work in.
- The data for the value will be initialized to “3” by default. Simply changing the “Value data” to “4” and clicking “OK” will turn off the USB storage.
- Simply changing the value data back to “3” will (re)enable the USB storage; once this is done, the USB storage will once again be enabled.
Enable the CurrentWare Console on your computer
- Step 1: Choose the user or computer groups that you want to have administrative privileges over.
- Step 2: Choose Device Permissions from the submenu of the AccessPatrol tab.
- Step 3: Select USB from the list of storage devices in the menu.
- Step 4: In the Access Permissions section, select the level of restriction you would like (Full Access, Read Only, No Access)
- Step 5: After clicking the Apply button, click the OK button.
If you follow these instructions, you will be able to prevent USB mass storage devices from functioning while still enabling keyboards and mice to do their jobs.
Use Device Control Software
There are a number of Device Control systems that are available to buy. Here are two packages that you could consider.
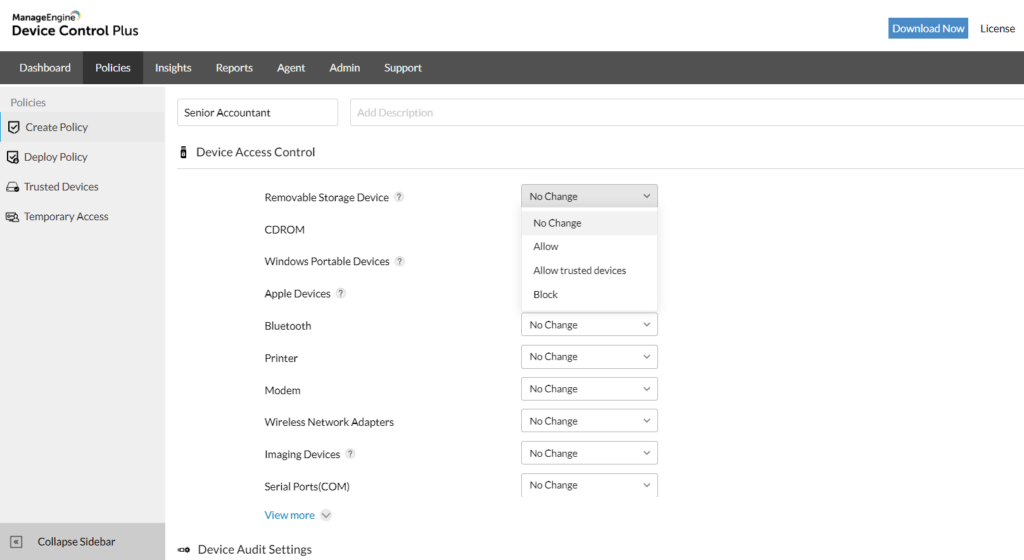
1. ManageEngine Device Control Plus – FREE TRIAL
ManageEngine Device Control Plus is a package of device security that includes procedures to control data movements on and off USB devices, secure data on those devices, and lockdown USB ports, providing selective usage permissions.
Key Features:
- Blocks all USB ports by default
- Selectively activates ports
- Blocks all USB sticks
- Allows specific USB sticks
- Creates a unified security policies
Why do we recommend it?
ManageEngine Device Control Plus is able to apply a single security policy to all of the endpoint USB ports. The package includes a library of templates, which makes security policy definition easier. The system will prevent file movements over a stated size and can create copies of all files moved onto USB devices to check for off-site changes.
This system identifies each USB stick by serial number and can allow its use on a specific computer or anywhere in the company. The tool blocks all software on a USB device from running. This prevents the execution of malware and those executable files can never be copied onto a protected computer.
The package also includes file access controls, which can permit specific users or user groups to access specific files. The service also tracks the activities of users when accessing files and it logs those events for compliance auditing.
A file shadowing service moves a copy of each file to a cloud storage account as that file is copied onto a USB stick. The system can also place a limit on file sizes that can be transferred and also a limit on the number of files that each user can transfer.
As well as logging all file access events, the system will raise an alert if a user attempts to access a file that is not allowed. Other triggers for alerts are a sudden increase in file movement activity or attempts to copy an altered file back onto the computer. This is where the shadow copy comes into play because it acts as a reference to the file’s original state.
All of the endpoints that are protected by Device Control Plus can be controlled from a central console. This dashboard includes screens for setting up security policies and alert trigger rules. The dashboard also provides a library of report templates that can be run on-demand or on a schedule.
Who is it recommended for?
This security policy is essential for any business, not only those that hold the personally identifiable information of private individuals. All of the data held by a company, such as client lists, price deals, sales campaigns, price calculations, and supplier data can be valuable to a rival business. Intellectual property is another type of data that needs to be protected.
Pros:
- Discovers all endpoints and lists them in an inventory
- Installs an agent on each endpoint for USB port monitoring
- Controls access to USB ports for both users and devices
- Can provide temporary permission for a USB device to attach
- Includes templates for security policies and guides on best practices
Cons:
- Doesn’t include a sensitive data discovery routine
ManageEngine provides a Free edition, which is limited to monitoring USB ports on 25 endpoints. The paid version is called the Professional Edition. Both editions will operate controls on endpoints running Windows and macOS and the software for the central server and dashboard installs on Windows Server. You can get a 30-day free trial of the Professional edition.
2. CoSoSys Endpoint Protector
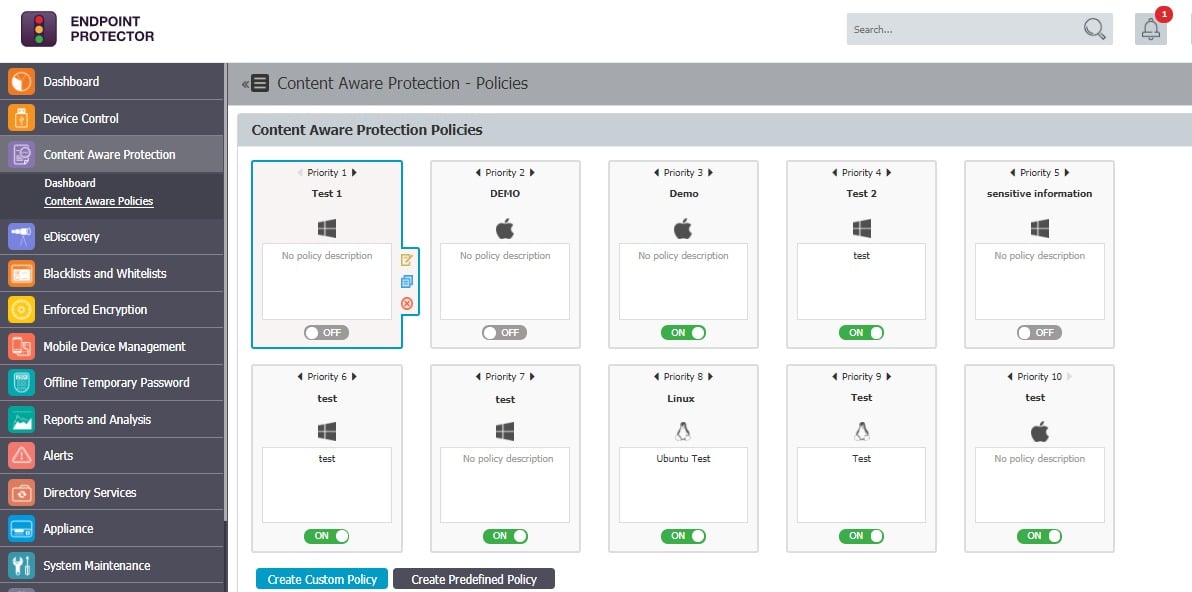
CoSoSys Endpoint Protector is a data loss prevention and antimalware package that operates a Zero Trust Access model for software. The functions of this package extend to USB ports. The strategy of Endpoint Protector is to disable everything. That includes software as well as devices. While USB ports are blocked, they are not completely deactivated and they can still be reached by the central controller of Endpoint Protector.
Key Features:
- Default deny for software
- Blocks all USB devices by default
- Creates an allowlist
- Prevents malware from executing
- Logs all activity
Why do we recommend it?
CoSoSys Endpoint Protector uses the same protection method for endpoints and for USB devices. All actions are blocked by default and then the administrator sets up a list of software and devices that are permitted. USB devices are identified by their serial numbers and can be approved for use on one device or all of the endpoints on the network.
Endpoint Protector is driven from a central dashboard. This unit will install an agent on each endpoint that is to be protected and that program implements USB port blocks. That unit is available for Windows, macOS, and Linux. The agent communicates with the central server to check whether specific devices are allowed to attach. If it’s not on the list, it’s not getting in.
The administrator needs to set up rules for USB usage and these are available to all endpoint agents, So, a USB can be approved for one device, some endpoints, or all of the computers connected to the network. The endpoint agent also writes logs for all file access events, which includes the movement of files.
The endpoint agent checks regularly with the central controller but also maintains its own rules locally. Log messages are transferred to the server periodically, The local capabilities of the agent mean that it can keep implementing the security policies that are relevant to its host and storing logs locally even if the computer gets disconnected from the network.
The endpoint agent will also encrypt USB drives to protect files from unauthorized access. The encryption system requires credentials for file access, which makes access to the files impossible if an outsider acquires the device.
The local agent monitors USB ports and knows which devices are allowed to connect. The tool also scans for Bluetooth devices and allows or blocks those depending on its allowlist. Endpoint Protector has a Content Aware unit, which implements data loss prevention for sensitive data. This is implemented by the same endpoint agent and it will apply to file movements to USB sticks.
So, the control of file movements to and from USB sticks can be selective and the permission for that action is influenced by the authorization that the user has for access to specific files according to their sensitive data contents.
Who is it recommended for?
This tool is useful for any business. The combination with the Content Aware function will interest businesses that manage sensitive data. The blocks on software on USB sticks mean that the tool protects endpoints against malware as well. The package includes compliance management for PCI DSS, HIPAA, NIST, ISO 9001, and GDPR.
Pros:
- Blocks all USB and Bluetooth devices apart from those on an allowlist
- Blocks all software from running on a USB stick or coping over to the computer
- Can allow a device for use on a computer by a specific user or on all computers and for all users
- Encrypts USB drives to protect the files transferred onto them
- Includes compliance enforcement and reporting
Cons:
- I couldn’t find the price list on their site
The server for Endpoint Protector is available as a SaaS platform or it can be activated as a service on AWS, GCP, or Aure. It is also possible to get the software package and install it on a network device or run it as a virtual appliance. The software runs on Oracle VM VirtualBox, VMware vSphere, Citrix Xen Server, and Microsoft Hyper-V. There isn’t a free trial for Endpoint Protector but you can request a free demo.
Conclusion
You can activate or deactivate the USB ports in Windows 10 by utilizing any one of the ways described above. Endpoint Protector, made by CoSoSys, is a very potent piece of software designed for companies that need to exercise command over the flow of data into and out of their enterprises. Depending on the requirements of your company, the platform can either be quickly implemented using a pre-configured server, or it can be completely adapted to work in a cloud environment.
In addition, this company specializes in data protection and offers role-based, granular permissions for users, which can make it easier for your IT staff to manage your network. In the end, I sincerely hope that you enjoyed reading this article.
USB Ports Lockdown FAQs
How can you lockdown USB ports on a Windows computer?
You can lockdown USB ports on a Windows computer by disabling USB ports through the device manager, setting permissions and access controls through group policy settings, or using third-party software solutions.
How can you lockdown USB ports on a Mac computer?
You can lockdown USB ports on a Mac computer by setting permissions and access controls through system preferences, or using third-party software solutions.
Can USB lockdown affect other devices that connect through USB ports?
Yes, USB lockdown can affect other devices that connect through USB ports, such as printers, scanners, and external hard drives. It is important to carefully manage and configure USB lockdown to ensure that essential devices are not affected.
Can USB lockdown be bypassed or circumvented?
USB lockdown can be bypassed or circumvented by physically modifying or disabling USB ports, or by using software and hardware tools to bypass security measures. It is important to regularly monitor and assess USB security measures to ensure their effectiveness.
Can USB lockdown be used for mobile devices?
Yes, USB lockdown can be used for mobile devices, such as smartphones and tablets, by disabling USB debugging and access through settings or using third-party security solutions.
How can you manage USB devices and access in a Bring Your Own Device (BYOD) environment?
In a BYOD environment, you can manage USB devices and access by implementing mobile device management (MDM) solutions, enforcing access controls and policies, and regularly monitoring and auditing USB usage.
Can USB lockdown affect productivity or business operations?
Yes, USB lockdown can potentially affect productivity or business operations if essential devices or workflows are impacted. It is important to carefully plan and test USB lockdown measures before implementation, and to regularly monitor and assess their impact.