The term “data at rest” refers to any data that your workload requires you to keep in a non-volatile storage medium for any length of time. This includes file systems, databases, archives, Internet of Things devices, and any other storage medium on which data can be persisted. When encryption and other appropriate access controls are implemented, the risk of unauthorized access to your data is reduced when it is protected while it is at rest.
One of the three states of digital data is called “data at rest,” and it refers to any digital information that is immobile and stored within permanent storage devices, such as hard drives and tapes, or information reservoirs, such as off-site backups, databases, archives, and so on. Data at rest is one of the three states of digital data.
When data has been moved to its ultimate location and has become stationary there, we refer to it as “data at rest” for the duration of the time during which it is inactive. If the data needs to be used for whatever purpose, and it is currently being processed, then the data is considered to be data that is in use.
Attackers can eventually find their way to classified data by utilizing a variety of exploit tactics, which they can use to their advantage. If the systems that have direct access to the data at rest are vulnerable, if the networks in which the data is stored become contaminated, or if the control over the various devices that contain the data is hijacked, then the integrity of the data that is at rest will be threatened.
Why Data at Rest Needs to be Protected
These days, a significant portion of the data that is being saved in computer systems and other electronic devices contains private information. This can include anything from personal information and business secrets to financial details and trade secrets.
These kinds of information can be extremely valuable to rival businesses as well as to people who commit cybercrime. Certain types of data can be sold on the dark web or in other shady marketplaces by cyber criminals, while other types of data can be used by competitors to gain an unfair advantage.
Why, then, target data that is already stored? The acquisition of data that is at rest, as opposed to data that is in motion, which refers to data that is moving across a network, is much simpler. If the information is kept in a transportable device, such as a USB stick, a mobile device, or a laptop, the adversary can easily take possession of that device and access the data. They are even capable of stealing a whole hard drive.
Data that is not being actively used is especially susceptible to being compromised due to the carelessness of employees. If someone gains unauthorized access to a work computer or if a company device is stolen or lost, the data that is at rest on it can be easily accessed and stolen by booting a device using a USB flash drive and bypassing login credentials.
This can be done even if the computer is password protected. This became a particularly pertinent issue during the COVID-19 pandemic when most companies were forced to permit their employees to work remotely and take their company-issued devices home with them. This is when this issue became particularly relevant.
Even if the data is not stored in a portable device, the possibility of obtaining a large volume of valuable information from just one location (such as a database or a server) is sufficient motivation to break into systems that store data at rest.
Securing Data at Rest
Firewalls, password protection, anti-virus software, and disk encryption are some examples of conventional perimeter barricades that are commonly utilized by businesses to protect their data while it is slumbering. Although these data security measures can prevent more obvious intrusions, malicious attackers frequently penetrate networks using more covert exploitation techniques. These techniques include employee deception through phishing scams or corporate espionage through the infiltration of peripheral devices.
Implementing encryption solutions is one of the most effective and straightforward ways for businesses to begin protecting their data while it is at rest from the carelessness of their employees. The native data encryption tools of operating systems, such as Windows BitLocker and macOS’ FileVault, enable organizations to encrypt the hard drives of their employees. This ensures that if someone were to steal or find a company device, they would not be able to access the device without an encryption key, even when booting a computer using a USB.
Tools for the Prevention of Data Loss That Protect Data at Rest
The practice of detecting and preventing data breaches, exfiltration, or the unwanted destruction of sensitive data is referred to as Data Loss Prevention, or DLP for short. DLP (Data Loss Prevention) is used by companies to safeguard their data and ensure compliance with various regulations.
The protection of businesses from both the loss of data and the disclosure of sensitive information is what is meant by the acronym DLP. The term “data loss” refers to an occurrence in which essential data is lost by an organization, such as when it is attacked by ransomware. The prevention of data loss focuses on preventing the unauthorized transfer of data outside of the boundaries of the organization.
DLP is typically utilized by organizations to:
- Maintain the confidentiality of personally identifiable information (PII) and adhere to any applicable regulations.
- Ensure the security of the organization’s most valuable intellectual property
- Achieve data visibility in large organizations
- Implement and enforce security measures in Bring Your Own Device (BYOD) environments, as well as for mobile workers.
- Ensure the safety of data stored on remote cloud systems
On the dark web, stolen data is frequently offered for sale, and users and organizations can buy it to use for their purposes after making the purchase. There is a clear financial incentive for data theft given that certain data types can sell for up to a few thousand dollars.
Data Loss Prevention Best Practices
Determine the most important goal you have for protecting your data. Are you looking to safeguard your intellectual property, improve your visibility into your data, or ensure that your business complies with all applicable regulations? With the main objective in place, it’s easier to determine the most appropriate DLP deployment architecture or combination of architectures. The four main DLP deployment architectures are Endpoint DLP, Network DLP, Discovery, and Cloud.
DLP is not solely a matter of security consideration. If you don’t have an approved budget for a DLP program yet, you need buy-in from other executives like the CFO and the CEO. Make use of the problems experienced by various business units so that you can demonstrate how DLP can solve those problems. Utilizing assets effectively and achieving profitable growth are two examples of pain points for the Chief Financial Officer. Managed DLP services alleviate these problems by doing away with the necessity of employing additional personnel and incurring additional CapEx to deploy and maintain a DLP program.
DLP tools can search for sensitive information based on predefined or custom content, file name, or particular compliance profiles in the hundreds of file types that are stored locally on employees’ computers. This is accomplished through the use of content inspection and contextual scanning. It will be possible to take corrective actions based on the findings. It is possible to delete or encrypt the sensitive information that was discovered so that it will not be taken or misused.
DLP solutions provide a method for remotely controlling the sensitive information that is stored on the computers of employees, removing the information when access to it is no longer desirable, and acting as an additional layer of security when it comes to managing data.
It is abundantly clear that the consequences of protecting only one category of data, whether it is data in motion, data in use, or both, and ignoring data that is at rest can be disastrous. For this reason, businesses must look for comprehensive solutions that can handle all sensitive data in any form it may exist.
ManageEngine Device Control Plus
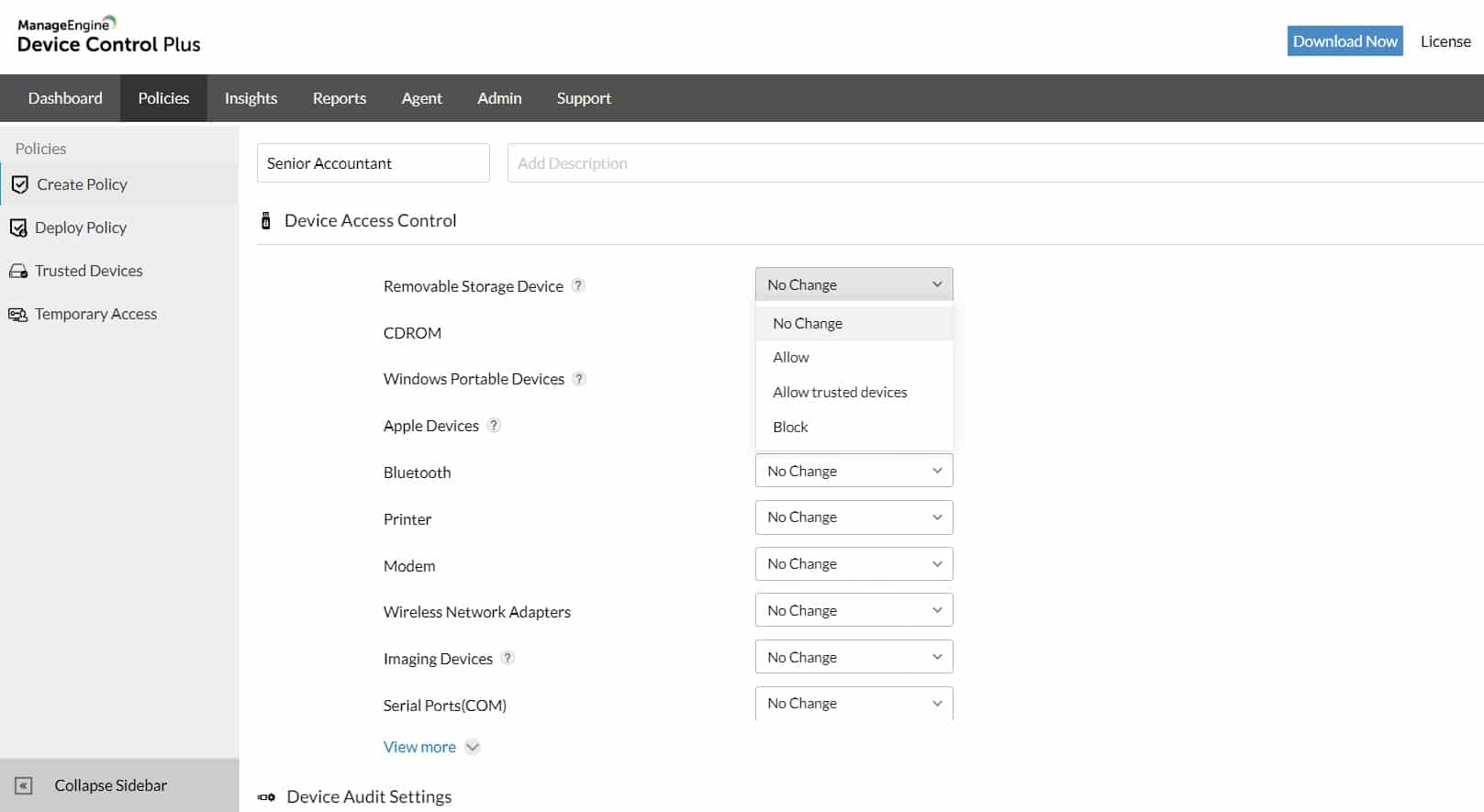
ManageEngine Device Control Plus is a package of data storage controls that covers USB devices. The system monitors USB ports, which effectively means that it blocks them. This is an allowlisting package, so if a US stick isn’t on the list, you can plug it in, but the operating system won’t allow it to attach.
- Port Management This system will control USB ports and also parallel ports and serial ports. It can watch over any device connecting to your computer, which includes cameras, iPods, CD-ROMs, and even printers. The tool doesn’t completely turn the port off – it is still active. However, it is controlled so that new devices can be detected and profiled even when they are not allowed to interact with the computer.
- Device Control The package doesn’t just block or allow devices. Administrators can apply different levels of access to each device. These can be read-only, copy blocking, copy on but not copy off, or full access. The system will block software from running on a USB while allowing files to move.
- Activity Tracking Every time a USB device plugs into a port on a monitored computer, Device Control Plus generates a log record. This is the case whether or not the device is allowed. For permitted devices, all file movements are recorded. This is a good audit trail for research in the event that the file movement controls are not sufficiently planned and data gets leaked.
Device Control Plus sees USB devices as a facilitator for data to be taken outside of the businesses and for viruses to be brought in. so, the tool includes processes to reduce those risks. For example, you can activate a shadow copy service that stores on a cloud account a copy of every file that is moved onto a USB stick. This is designed to prevent users from evading file modification controls on site by taking a file away and then changing it elsewhere, then copying it back onto the computer.
Pros:
- Identifies devices by serial number
- Granular controls over access to allowed devices
- Blocks software on USBs to prevent virus transfer or tampering from a USB host
- Logs all USB activity
- Prevents off-site changes to files
- Blocks all USB devices by default
- Continues to monitor blocked ports
Cons:
- No SaaS option
ManageEngine Device Control Plus is only available for Windows Server. You can assess the system with a 30-day free trial.
CoSoSys Endpoint Protector
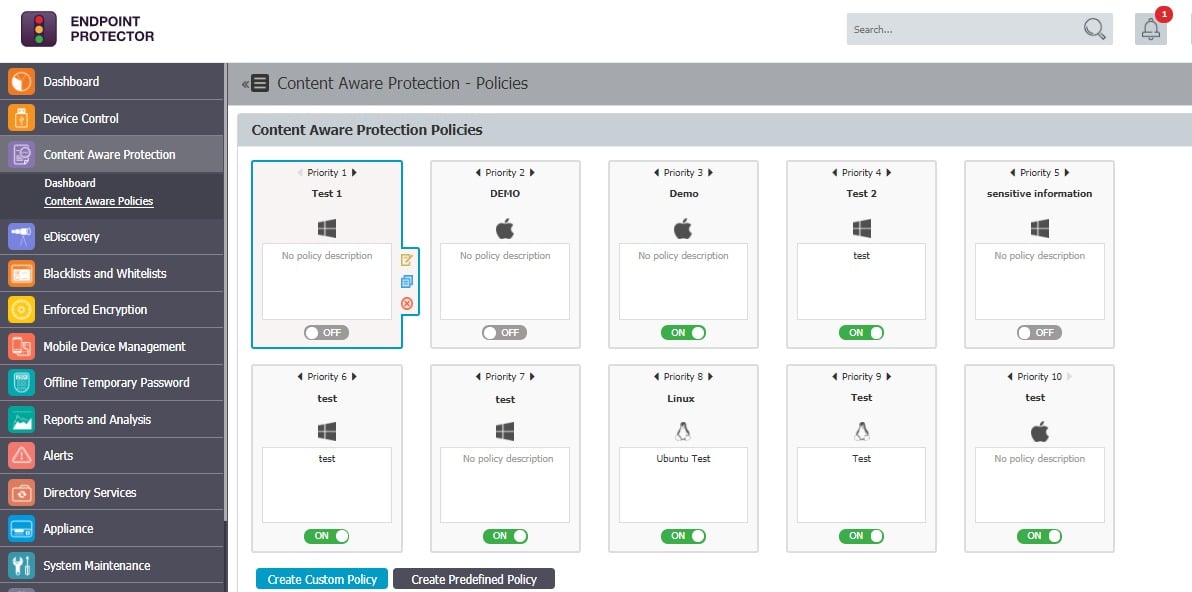
Endpoint Protector by CoSoSys is a comprehensive Data Loss Prevention (DLP) solution that is compatible with PCs running Windows, macOS, and Linux, as well as Thin Clients and Desktop-as-a-Service (DaaS) platforms. The solution protects against data leaks, theft, and exfiltration. It also reduces the risk of insider threats and assists businesses in meeting the requirements of various data protection regulations, including the GDPR, CCPA, PCI DSS, HIPAA, and others.
- Device Control Device Control is a powerful method for controlling the connections of physical devices that can be connected to a machine in a variety of different ways. These tangible devices may take the form of webcams, USB drives, Bluetooth, external drives, mobile phones, keyboards, or anything else that is capable of being connected to a computer. Endpoint protector gives you the option to select from one of six distinct modes: Normal, Stealth, Panic, Hidden icon, or Silent. In most cases, the Normal, Hidden, and Silent modes are the most effective, and any one of these would be the ideal choice for your requirements.
- Content-Aware Protection This is the module of Endpoint Protector that receives the most attention. An analysis of the data contained within the files themselves is carried out using this component. It encompasses everything, from Word documents and spreadsheets to emails and other electronic communication. By utilizing this module, you will essentially be able to control the flow of information. Strong content policies can be enforced by Admin through this module to prevent unintentional or intentional file transfers of sensitive data belonging to the enterprise.
- eDiscovery This module’s major objective is to safeguard data that is now “at rest” from both internal and external threats. It does this by encrypting the data. eDiscovery performs an intuitive scan of the sensitive and confidential data that is stored on your workstations and gives you the ability to remotely take corrective actions such as deleting or encrypting data.
It provides clients with a variety of specialized modules from which they can select the ones that best meet their requirements. These modules include Device Control, which controls USB and peripheral port access; Content Aware Protection, which protects data while it is in transit; eDiscovery, which examines data while it is stored; and Enforced Encryption (secures USB storage devices).
Pros:
- The confidentiality of customer records and information is ensured.
- All of the most popular computer operating systems are compatible with Endpoint Protector.
- The granularity that Endpoint Protector provides regarding which users or computers receive which policies makes it simple to implement.
- Endpoint Protector offers a comprehensive feature set for endpoint security.
- A superficial examination of the current state of the Endpoint Protector entities.
- Export/import devices/computers.
- Make a fresh device or computer using manual means.
Cons:
- Has a variety of features and customized controls that can take time to fully explore.
It performs a scan of the content that is stored on the user’s system and provides you with the ability to take any necessary corrective actions for data that is “at rest”. The scan is based on the sensitive content policies of your organization. Endpoint Protector’s eDiscovery module protects data while it is at rest.
Conclusion
Some solutions, such as Endpoint Protector, even provide employees with the ability to use company-approved USB devices while ensuring that any files that are copied onto those devices are encrypted. This feature is known as enforced encryption.
If data is essential to the success of your company, then the CoSoSys Endpoint Protector is an excellent piece of software that is well worth the investment. This program offers outstanding 360-degree security and protection for your sensitive and confidential data, whether the data is at rest or in motion.
Protecting Data at Rest FAQs
What does "data at rest" mean?
Data at rest refers to data that is stored or saved on a device, such as a hard drive, USB drive, or memory card, and is not actively being used.
What are some common methods for protecting data at rest?
Common methods for protecting data at rest include encryption, access controls, physical security, and data backups.
How can access controls be used to protect data at rest?
Access controls can be used to limit who has access to data at rest, such as by implementing role-based access controls, password policies, and user authentication mechanisms.
How can physical security be used to protect data at rest?
Physical security measures, such as locks, security cameras, and access controls, can be used to prevent theft, loss, or damage to devices that store data at rest.
What are some data protection regulations and standards?
Some data protection regulations and standards include the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS).
What are some common mistakes businesses make with data protection?
Common mistakes businesses make with data protection include using weak passwords, not encrypting sensitive data, not backing up data regularly, and not training employees on data protection best practices.
How can businesses monitor data protection?
Businesses can monitor data protection by using data encryption and access control software, reviewing data logs and reports, and setting up automated monitoring and alerting systems.
How can businesses respond to data protection incidents?
Businesses can respond to data protection incidents by quickly identifying and isolating the affected systems, containing the incident to prevent further damage, and notifying affected parties and authorities as needed.