Network monitoring and management are inevitable in any discussion about information technology. Accordingly, a major duty of an IT department or supplier is to maintain a company’s vital systems operationally. Networking equipment, such as firewalls, routers, switches, and Wi-Fi access points, must be constantly monitored by IT personnel. Using the end-to-end Network Performance Monitoring tool, IT professionals can instantly identify problems.
Every network component like routers and switches is constantly monitored, analyzed, and improved thanks to network monitoring, which is a vital aspect of this position. Active monitoring may help avoid network failures or downtime and remotely managed IT environments save the time and resources required to execute important upgrades or make on-the-fly adjustments to an IT system.
What is Network Monitoring?
Devices and connections may be monitored by a network monitoring Device to discover and report faults, schedule repair, and ensure compliance and security. Several significant components are included in such systems, such as:
- Network device monitoring In the event of network device failure, downtime, productivity losses, or even security threats might occur. Hardware problems and failures may put the whole infrastructure to a standstill, while heavy CPU or network utilization can grind activities to a halt. A network monitoring system makes it possible to swiftly locate and fix these potential problems. Additional benefits include detecting malicious behavior, mapping network topology, and alerting administrators about potential security breaches.
- Alerting system The network monitoring system sends notifications to the IT personnel when it detects problems, so they can address them. Technicians may begin the remedy process as soon as the issue is a real problem or hazard.
- Reporting Many network monitoring software can create reports based on a set of results.
How to monitor network performance?
The device should have the ability to do proactive network monitoring as a standard feature. Proactiveness is a key value proposition in the current IT sector, which relies on the capacity to identify and fix problems before they affect a network.
SNMP systems are generally used for proactive network monitoring, which provides tools with several critical capabilities:
- Monitoring and polling in real-time
- Data on the performance of the hardware
- Automated configuration of devices is also possible
- Data from Netflow
- Alerts that can be customized
What is the Purpose of Using a Network Monitoring Device?
At this point, you may be wondering, “Why use this solution instead of alternative methods?” GFI Software, a long-time player in the industry, lists distinct advantages of implementing a network monitoring system.
- Real-time monitoring allows you to be alerted quickly if there is a problem or abnormality, such as by SMS, pager, email, or network message.
- To keep an eye on an ongoing issue, consider using a network monitoring service. It may be time to repair a piece of hardware that keeps tripping, for example.
- Recognize problems that assume that one of your company’s websites is offline. No way of knowing if the issue is with the website, web server, or apps running on it is possible without network monitoring.
- Network monitoring reports may help you notice patterns in system performance, establish the need for upgrades or replacements, and demonstrate your worth, by documenting the usually hidden effort that maintains the IT systems you manage in top condition.
- The time saved by being warned quickly may be utilized to bring in a backup system to replace the present failure, ensuring that your clients and your users get a smooth and efficient service from your company.
- Despite investing a lot of money, time, and resources on security software and hardware, businesses cannot be certain that the devices are working properly without a network monitoring solution.
- You should keep an eye on your online applications since many of the services you provide to your clients and users are likely to be web apps. Using network monitoring technologies, you can keep an eye on your website and fix problems before your consumers notice.
Significance of network monitoring device
Networks have progressed from a few parts to increasingly sophisticated architectures with advanced technology and devices. Network monitoring tools help administrators to know about the entire network’s health, performance, and possible concerns. To facilitate network monitoring and administration, having real-time network information is vital.
The function of network monitoring protocols is to deliver important data and critical information about different network activities. They’re meant to allow the monitoring of data and traffic traveling to and from the network connections (host and client).
The data aggregated by the network monitoring tools utilizing standard protocols is shown visually to enable administrators to utilize the information in controlling a network’s activities.
Best practices for network monitoring devices
- Disk Monitoring Organizations use storage arrays with many drives to store their most private and confidential data. Business continuity might be jeopardized if there are problems with the hard drive. Analyzing I/O actions on logical drives may be done by using disc monitoring. To obtain notifications when network metrics hit a critical level specified by organizations or teams, teams might use I/O disc monitoring. When errors, effective space use, free space, big file statistics, changes to disc space consumption, and I/O performance are being monitored through disc monitoring, this is a huge aid. To limit downtime and identify storage-related issues, effective disc monitoring is necessary.
- Tracking the availability of resources When it comes to keeping a company’s IT infrastructure up and running around the clock, availability monitoring—the tracking of all network components and resources utilized by an organization to guarantee business continuity—is essential. Monitoring the availability of resources such as firewalls, switches, and routers is an important tool for system administrators. Monitoring storage space, bandwidth use, and system-level services are all made easier with availability monitoring.
- Monitoring Interface High-speed fiber-optic networks and Gigabit Ethernet are common networking technologies. The interface serves as a point of entrance and exit for data packets. In the event of an interface failure due to data packet loss, device failures, or usage constraints, there are many possible causes. Network performance, bandwidth (use and consumption), and faults may be monitored using a trustworthy interface monitoring tool that collects data relating to the network’s performance, bandwidth, and defects. The final findings are shown on a single screen by the tool and typically help the administrator determine the root cause of an issue in real-time. Interface monitoring is a useful tool for keeping tabs on network interfaces and taking proactive measures to address performance problems.
The Network’s Standard Operating Procedures
It is critical to be able to recognize abnormalities in the network’s baseline behavior, such as CPU use and the temperature of a core switch, to take preventative measures and avert network failures. A network administrator may establish alerts and reminders to avoid network downtime by knowing the network’s threshold values.
Configuration management
Network difficulties and data loss may result from even simple configuration modifications. By using configuration management, you can ensure that all of your routers, firewalls, and switches are properly configured without compromising the overall system’s performance.
Configuration management may also be utilized for backups and mass updates. This saves time and avoids unauthorized modifications that might lead to data theft, hacking, and other significant security failings.
User access and configuration modifications may be tightly controlled by administrators using a solid network monitoring solution with configuration management features.
Escalation Matrix
Having an escalation matrix is critical for firms that have a high number of employees and/or network administrators. The appropriate team is notified of any networking difficulties, which aids in their quick resolution. This may lead to significant network difficulties such as slowdowns and breakdowns if the alarms are not followed and the escalation matrix is not followed.
An organization’s monitoring and reporting have to be set up so that the right people are informed of difficulties based on their area of expertise. An inquiry may be sent to another level if the appropriate team or person isn’t immediately accessible. This minimizes the amount of time it takes to conduct an investigation.
Planned Capacity Growth
This means that the IT infrastructure of a business increases as well. WAN bandwidth and the number of networked systems, servers, and storage devices grow in tandem with the company’s personnel base, as well.
System and network monitoring enable managers to keep an eye on resources, how they are being used, and how much they are being used. It is possible to use free monitoring tools to plan for capacity. Organizations may use licensed or subscription-based technologies to fill up the gap since every monitoring tool has a limit on the number of resources and components it can monitor. These authorized monitoring tools provide cutting-edge features and smooth functionality. A network administrator may monitor changes in RAM, CPU consumption and add-on install to improve the system’s performance.
It’s better to have a multi-featured network monitoring system in place than to acquire and update many products to keep track of various network characteristics.
Implement Failover Options for High Availability
To gather data from the devices, monitoring systems have been implemented. All acquired data becomes worthless and unavailable for analysis if a network slowness or outage occurs. If you have a high-availability monitoring plan and failover solutions, you can prevent these kinds of problems.
High availability means that the monitoring system has no single point of failure and is accessible throughout, giving critical data for detection and resolution even if the network goes down. Alternatively, there is the use of a failover to aid in the replication and storage of data acquired from the monitoring systems. Having a failover system in place may help with troubleshooting if the main system fails.
How to pick the right network monitoring device
The Simple Network Management Protocol (SNMP) is already available on every network device that you buy. It is also available within Windows – you just have to activate it. In the SNMP system, device agents scan their hosts and each compiles a structured report, called a management information base, or MIB. The SNMP system requires an SNMP Manager because the device agents won’t do anything with the MIBs unless they are asked for them.
Auvik – FREE TRIAL
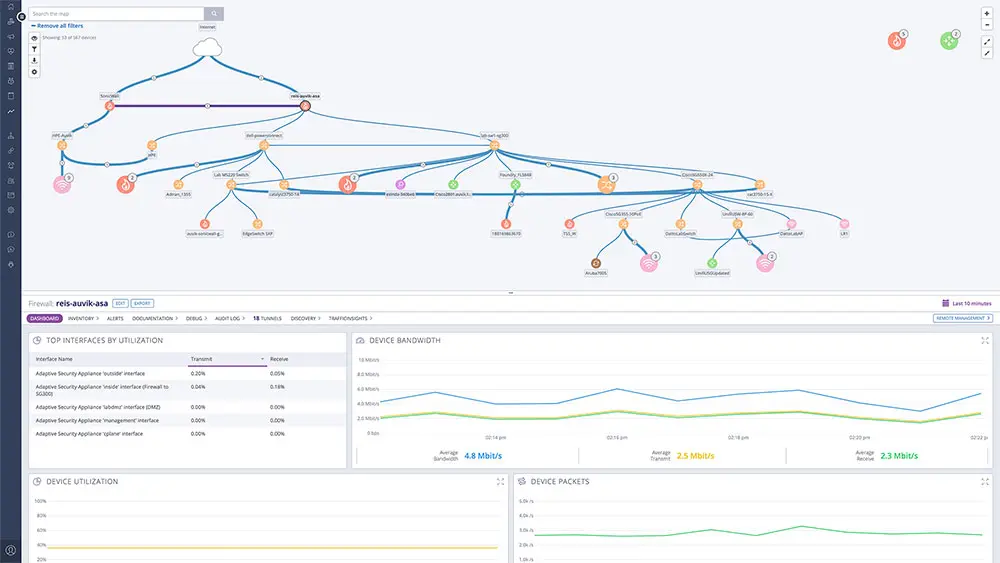
A typical network device monitoring tool is usually called a “network performance monitor.” For an example of these systems, take a look at Auvik. This is a cloud platform and it installs a data collector on a server that is connected to the enrolled network. This unit fulfills the role of the SNMP Manager. The collector doesn’t need a list of devices on the network because it broadcasts an SNMP Request across the network. All the SNMP device agents are constantly listening for a request. When they pick one up, they send back their MIBs and then continue scanning their devices, updating their MIBs ready for the next request. The collector uploads the MIBs to the Auvik cloud server for processing.
The MIB provides information about its device and this goes into a system inventory. The Auvik package is able to generate a network topology map from the MIB data because the form includes information on each interface on the device and which other device it connects to. Status data goes into the device monitoring screen. Thus, SNMP provides Auvik with an autodiscovery service, details for a hardware inventory and a network topology map, plus status information for live device monitoring.
While Auvik is sorting through the uploaded MIBs, the collector sends out a new SNMP Request and the whole process starts all over again. With this continuous cycle, the Auvik console can keep its inventory and map up to date without having to implement any special custom-built routines.
SNMP allows a device agent to send out a MIB without waiting for a request if it detects a system error on its device. This is called a Trap and gets interpreted into an alert in the Auvik network performance monitoring console. Auvik also provides network traffic analysis, extracting data from switches and routers by using flow protocols. You can examine the Auvik system by requesting a 14-day free trial.
Network Device Monitoring FAQs
What types of metrics can be monitored with network device monitoring tools?
Network device monitoring tools can monitor a wide range of metrics, including network bandwidth utilization, CPU usage, memory usage, packet loss, and error rates.
How does network device monitoring differ from network performance monitoring?
Network device monitoring focuses specifically on the performance and availability of network devices, while network performance monitoring involves monitoring the overall performance of the network infrastructure, including devices, applications, and services.
Can network device monitoring tools be used for cloud monitoring?
Yes, network device monitoring tools can be used for cloud monitoring by tracking network activity and performance in cloud environments, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP).
What types of support are available for network device monitoring tools?
Most network device monitoring tools offer a range of support resources, including technical support, online documentation, and a knowledge base.