The technique that Forcepoint employs helps clients alleviate the load of administration caused by traditional point product approaches, simplify security operations by working with fewer suppliers, and save expenses by a substantial amount. The authors of the Gartner report that was published on December 1 2021, and titled “Predicts 2022: Consolidated Security Platforms Are the Future” wrote that by the year 2025, 80% of businesses will have adopted a strategy to unify web, cloud services, and private application access from a single vendor’s security service edge (SSE) platform.
They went on to say that “single-vendor solutions provide significant operational efficiency and security efficacy, compared with best-of-breed”, which includes reduced agent bloat, tighter integration, fewer consoles to use, and fewer locations where data must be decrypted, inspected, and encrypted.
Key Features:
- Track intellectual property in both organized and unstructured forms using Forcepoint.
- Automatically avoid data breaches.
- Automatic policy enforcement, interoperability with categorization vendors, and database flexibility.
- Delivers risk-adaptive protection, risk-based policy enforcement, and behavioral analytics.
By unifying essential security services such as Secure Web Gateway (SWG), Remote Browser Isolation (RBI), Content Disarm and Reconstruction (CDR), Cloud Access Security Broker (CASB), and Zero Trust Network Access, Forcepoint ONE makes it easier for customers and partners to adopt Security Service Edge (SSE) (ZTNA). Integrated Advanced Threat Protection (ATP) and Data Loss Prevention (DLP) also prevent malware from entering the system and secure sensitive data across business applications and BYOD devices, hence removing the need for many fragmented products.
With Forcepoint ONE, security teams can now administer a single set of rules across all apps using one cloud-based dashboard, one endpoint agent, and agentless support for unmanaged devices. This is made possible by Forcepoint ONE’s ability to enable agentless support for unmanaged devices.
EDITOR'S CHOICE
Download: Forcepoint One
Official Site: https://www.forcepoint.com/product/forcepoint-one
OS: Cloud-Based
Here is our list of the Best Forcepoint One Alternatives:
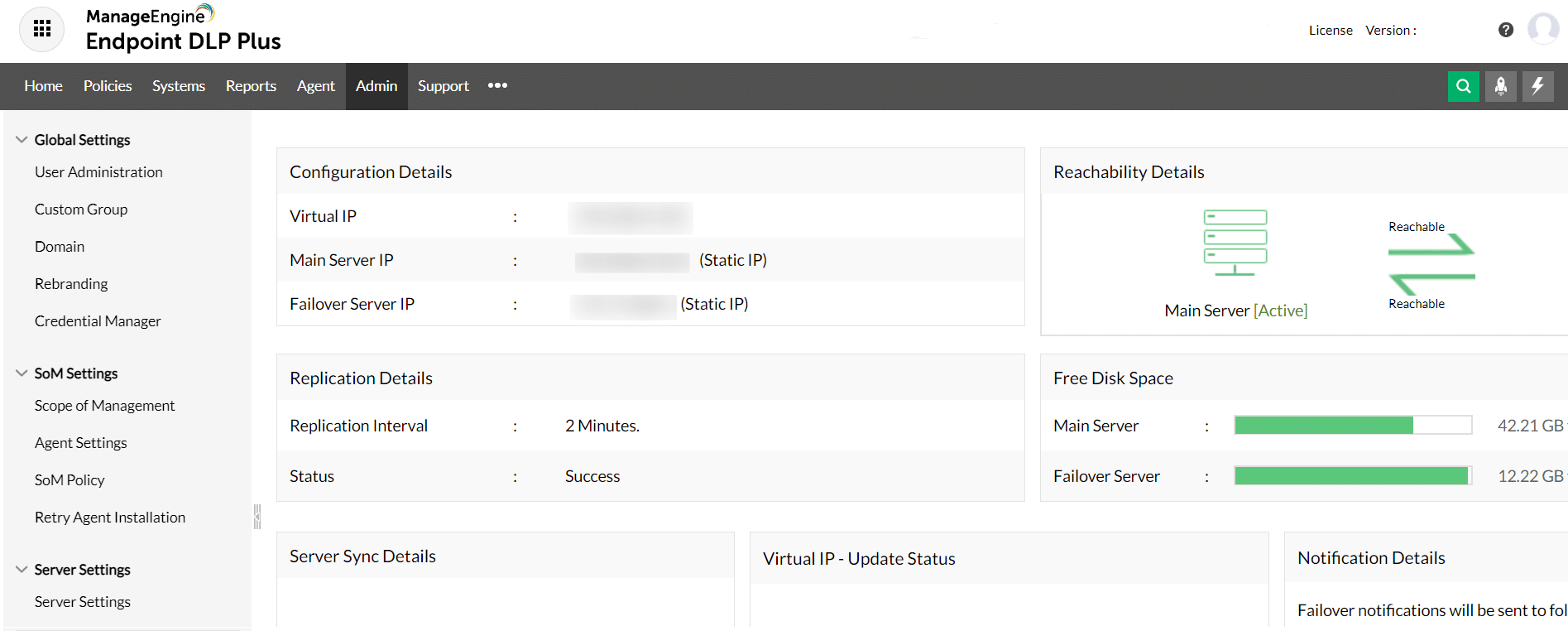
- ManageEngine Endpoint DLP Plus – FREE TRIAL A package of measures to protect sensitive data that includes data discovery and classification and policies to allow controlled access. Runs on Windows Server. Get a 30-day free trial.
- CrowdStrike Falcon It’s a security tool developed by CrowdStrike that runs in the cloud. The platform offers protection for personal computers running Windows, Mac OS X, and Linux, in addition to mobile devices and Windows servers
- Barracuda CloudGen Firewall The Advanced Threat Protection engine, which is housed in the cloud and tasked with the mission of stopping different cyber threats, including zero-day
- Zscaler Cloud Protection Composed of components that offer users fast, redundant, and robust performance. With this functionality, users may securely access apps, services, and content
- Fortinet Fortinet Fortigate VPN solutions all offer reliable protection thanks to their foundation in IPSec and SSL technologies.
- Endpoint Protector Endpoint Protector is a Data Loss Prevention (DLP) product that works across several platforms.
Our methodology for selecting a Security Service Edge (SSE) tool:
We’ve broken down our analysis for you based on these key criteria:
- Integration of multiple security services.
- Ease of administration and operations.
- Effectiveness in risk-adaptive protection.
- Flexibility in policy enforcement and analytics.
- Efficiency in securing data across applications and devices.
1. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP Plus aims to protect sensitive data. It will discover all sensitive data locations, with respect to specific data protection standards. So, the process will look for different types of data, such as bank card numbers or social security numbers depending on how you set up the service.
Key Features:
- Data discovery
- USB blocks
- File containerization
- Granular access controls
- Data egress monitoring
Why do we recommend it?
We recommend ManageEngine Endpoint DLP Plus because it offers comprehensive data protection strategies tailored to specific data protection standards, making it ideal for organizations with strict compliance requirements. Its integration with Active Directory and robust USB controls ensure that sensitive data remains secure across various endpoints.
This package has a number of strategies to protect data and all of these systems are adapted according to access rights. You can set up permissions for user access to specific types of data and that process can be threaded into your existing Active Directory domains.
Endpoint DLP Plus provides options over how to protect data stores and one of these is a data containerization function. This provides an encrypted cocoon around files or folders. The system plugs into the access rights manager, so only certain users are allowed to get to those data stores.
Other controls include the management of data movement tools, such as cloud upload facilities, synching, USB sticks, file transfer utilities, and email systems. These controls vary. Most of them scan data movement attempts and refer to the access rights manager to see whether that action is allowed.
The big exception to this is the device control module, which has many more features than other data movement control utilities. This system also examines the movement of files to printers.
USB controls start with blocks on USB ports. This action doesn’t disable the port – it is still active and can be communicated with for control. The administrator then has the option of allowing the use of specific devices. These are identified by their serial numbers. This system will also link into access rights management because the device can be approved for use by specific users or specific data types, accessed by specific users.
The USB control blocks software on the stick, which freezes malware and it won’t be able to copy onto the computer or access resources there. The tool can allow some actions but block others.
All file access events are logged and copies onto a USB can be shadowed. This involves simultaneously copying a file onto a cloud platform when it is moved onto a USB stick. This prevents files being altered off-site to circumvent on-device controls.
Who is it recommended for?
This tool is recommended for IT administrators and security professionals in organizations that require stringent data protection measures, particularly those that handle sensitive information like financial data or personal identifiers. It’s especially beneficial for companies that rely heavily on Windows Server environments.
Pros:
- Links into Active Directory for data access permissions
- Logs all interactions with stores of sensitive data
- Controls the use of peripheral devices
- Can block screenshots and printouts
- Monitors all data movement channel
Cons:
- Only available for Windows Server
The Endpoint DLP Plus system is a software package that will run on Windows Server. ManageEngine offers Endpoint DLP Plus on a 30-day free trial.
2. CrowdStrike Falcon
CrowdStrike is a company that has just recently emerged on the scene of the cyber security industry. The company was established in 2011 as an alternative to the conventional, labor-intensive approach to information technology security. Within a relatively short period, the Falcon platform received a great deal of acclaim and recognition for its forward-thinking approach to endpoint security.
Key Features:
- Integrated threat intelligence
- Able to manage thousands of endpoints
- Anti-Exploit Technology
- Threat intelligence
Why do we recommend it?
CrowdStrike Falcon is a platform of services and presents a series of modules and packages of modules that can match the features of Forcepoint ONE. The cloud protection features of Forcepoint are similar to the CrowdStrike Falcon Cloud Security system. To get protection for on-premises systems, you would need CrowdStrike Falcon Insight XDR.
It’s a security tool developed by CrowdStrike that runs in the cloud. Clients may save money on hardware and maintenance costs by using cloud-based antivirus software, in contrast to traditional on-premise antivirus systems, which can be hacked by cybercriminals.
When it comes to security services, CrowdStrike does not employ a “one size fits all” method. Because of this, your company will have the ability to pick the items that it needs. An example of this would be a CrowdStrike Falcon module that reveals how your software development team is utilizing containers and offers visibility into this activity.
CrowdStrike’s Falcon is an information technology security solution that might be beneficial to businesses of any size. There are no restrictions placed on the maximum number of endpoints that may be serviced by it.
To employ CrowdStrike Falcon, small businesses need to have a skilled information technology team. If you do not have that degree of technical understanding, the platform might be quite intimidating for you.
Due to the extensive collection of features, security insights, and managed services that it offers, CrowdStrike Falcon is ideally suited for usage by both moderate and large enterprises. Organizations that already make use of a security operations center will profit significantly from this in particular (SOC).
The platform offers protection for personal computers running Windows, Mac OS X, and Linux, in addition to mobile devices and Windows servers. Additionally safeguarded are the data centers that rely on CrowdStrike for their security needs.
Who is it recommended for?
Both CrowdStrike Falcon and Forcepoint ONE have a lot of modules, so it is difficult to ma; exactly the services of one to the other. CrowdStrike offers a Data Protection unit, which matches the DLP feature of Forcepoint ONE. Overall, CrowdStrike Falcon is more suited to large organizations than the Forcepoint ONE system.
Pros:
- Excels in hybrid environments (Windows, Linux, Cloud, BYOD, etc.)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Lightweight agents take up little system resources
Cons:
- Would benefit from a longer trial period
The Falcon solution offered by CrowdStrike not only safeguards your data but also abides by the relevant legislation. It counts healthcare organizations and monetary entities like banks and governments among its clientele. It also serves clients in the public sector.
3. Barracuda CloudGen Firewall
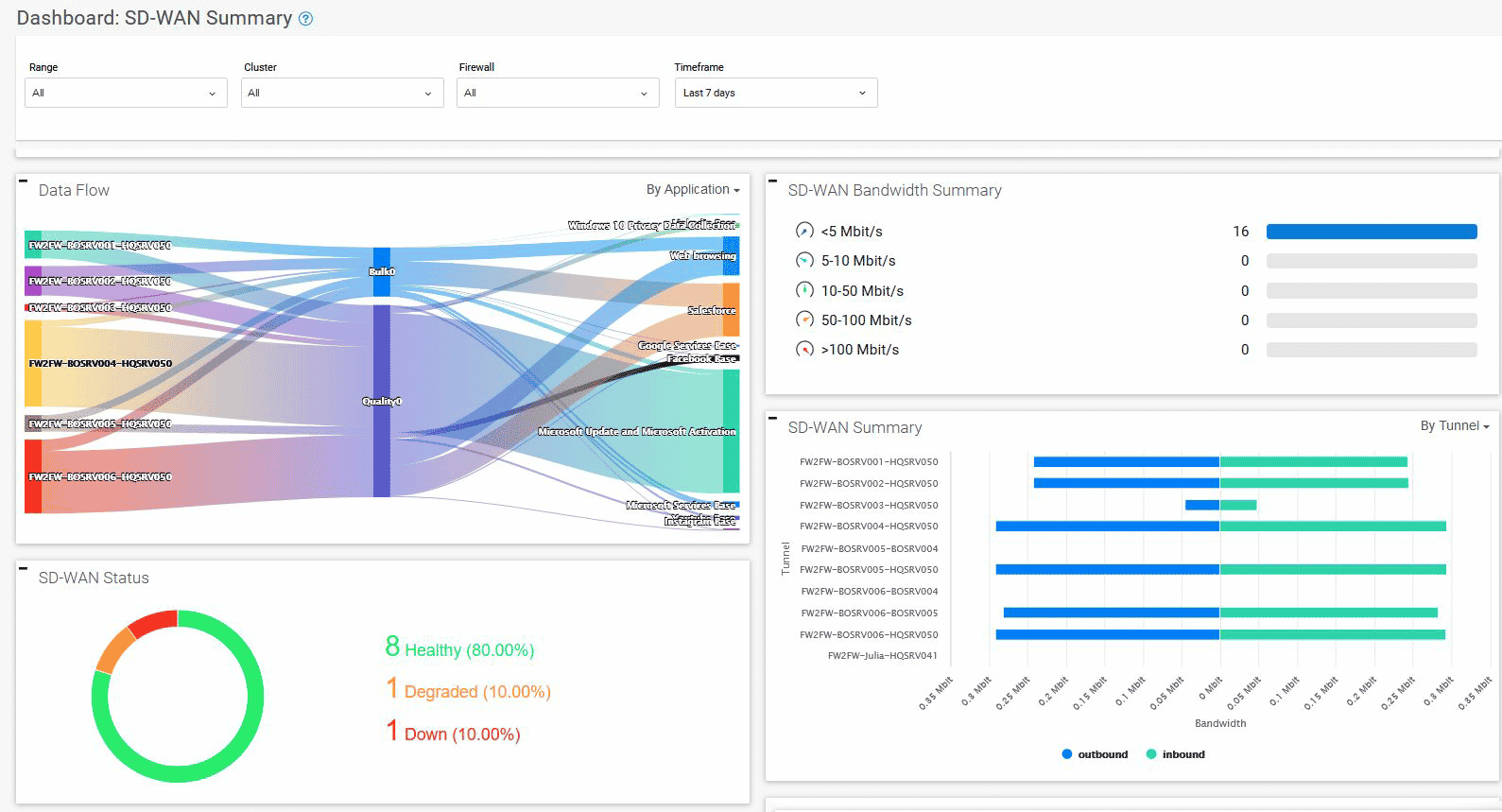
In marketing materials, the Barracuda CloudGen Firewall is said to go beyond the capabilities of next-generation firewalls, whatever that term may entail. In any event, you will be provided with a multi-layered security package that is suitable for hybrid as well as cloud networks. The Advanced Threat Protection engine, which is housed in the cloud and tasked with the mission of stopping different cyber threats, including zero-day ones as well as targeted assaults such as ransomware, serves as the system’s central component.
Key Features:
- Advanced Threat Protection (ATP)
- Intrusion detection and prevention
- Malware Protection
- SSL interception
Why do we recommend it?
Barracuda CloudGen Firewall is an edge service and you can set it up to receive all of your traffic, clean it, and then pass on valid traffic to your site over a VPN connection. You can also use it to front a virtual network that stretches across the internet.
The Barracuda CloudGen Firewall is incredibly quick because it has access to a worldwide threat intelligence network. This network compiles information from millions of “protection points” all around the world, giving it a massive advantage in terms of speed. Barracuda will use this data to provide you with a truly global level of coverage when it comes to tracing down the origins of threats, in addition to being nimble when it comes to the identification of potential dangers.
The information that was acquired on these threats includes vulnerabilities, network threats, and exploits such as viruses, trojans, spyware, worms, SQL injections, cross-site scripting, denial of service attacks, and other similar types of assaults.
Who is it recommended for?
This system is a different proposition to Forcepoint ONE because it is primarily a cloud-based firewall for on-premises systems and it doesn’t include systems such as access controls or connection protection for remote workers. The Barracuda system can be enhanced with reverse firewall functions to examine outgoing traffic for data loss prevention.
Pros:
- Offers automated threat responses options to malware attacks
- Includes IDS/IPS settings to stop probing and DoS attacks
- Offers VPN service with mobile support
Cons:
- Better suited for enterprise networks
Sandboxing technology is at the heart of Advanced Threat Protection, which enables intelligent threat detection that is informed by learning. Any threat that gets through the previous layers of protection without being deemed safe will be eliminated as a result of this feature.
When it has finished doing that, the system will then convey this information to the previous security levels and supply them with the intelligence on the danger that can be put to use proactively the next time the Firewall comes across the same threat. The system also includes security against malware and botnets, which controls all connection requests and diverts traffic away from harmful servers and websites.
4. Zscaler Cloud Protection
Zscaler is a cloud-based security system with scalable performance and customizable scalability. It relies on more than 100 data centers dispersed across all continents, enabling the software to assist enterprises in delivering their content without delay. The Zscaler Cloud Security Platform has partnered with the world’s leading internet exchange points, enabling it to provide enhanced performance and consistent uptime.
Key Features:
- Internet Traffic Examination
- User Trailing Policies
- Threat Recognition
- On-Demand Global Visibility
Why do we recommend it?
Zscaler is a very similar platform to Forcepoint ONE because it provides a ZTA package that protects connections between remote workers, sites, and cloud platforms and also integrates an access rights management service. You can apply different Zscaler modules to assemble different security configurations including DLP.
Additionally, it scales effortlessly to meet the traffic demands of users, even the difficult-to-examine SSL. With this service, organizations and their users are safeguarded against cloud-based security threats. This is achievable because the cloud security solution responds immediately to blockages and breaches to safeguard its users.
Zscaler is composed of components that offer users fast, redundant, and robust performance. With this functionality, users may securely access apps, services, and content. The software’s enforcement nodes provide users with an exceptional experience. The traffic is delivered straight to them, which firmly and consistently implements key regulations. These nodes do not keep data logs, but they have examined and cleaned them in RAM. This just indicates that data logs are produced in memory after being delivered to the Zscaler logging plane.
Who is it recommended for?
Zsacler is a flexible platform that is evolving quickly. The company has created three groups of plans, which are Zscaler Internet Access, Zscaler Private Access, and Zscaler Digital Experience. There is also a package called Zscaler for Users, which combines all of the other three plans. This is the closest system to Forepoint ONE.
Pros:
- Based as a flexible cloud-based SaaS
- Offers DLP features for file recovery and integrity monitoring
- Can inspect SSL traffic for malicious packets
- Excellent interface and monitoring dashboard
Cons:
- Must contact sales for pricing
Zscaler has an activity monitor that analyses the whole cloud system and gives a uniform interface for configurations, threat data, and software and database upgrades. The core administrative portion is distributed across many data centers throughout the globe, ensuring optimal performance and redundancy. You may need to monitor the data log to gain deeper network insights and assess the traffic flow. Utilizing Nano log technology, Zscaler guarantees that all logs are both compressed and lossless. Because the program may transmit the data to third-party SIEM services, it is possible to send logs on drives while adhering to local rules.
5. Fortinet
Fortinet should be on your list of products to evaluate if you are interested in top-tier protection at an affordable price range. Fortinet is one of the most popular firewall suppliers and a regular contender on business shortlists since the company’s FortiGate firewalls provide robust protection at an affordable price range.
Key Features:
- Safety and effectiveness
- Support
- Cloud characteristics
- Management
Why do we recommend it?
Fortinet is a major cybersecurity provider and its star product is the FortiGate firewall. Fortinet created its own physical architecture for its FortiGate appliance and stuck to the hardware format for decades. The company has now branched out to cloud-based and virtual appliance firewalls, which makes the range more accessible.
This business, along with Palo Alto and Check Point, was recognized by Gartner as a leader in its Enterprise Network Firewall Magic Quadrant. This excellent ranking was validated by NSS Labs testing, in which Fortinet’s firewalls achieved high scores for their efficacy as a security measure, their performance, and their value.
In the future, businesses will need to be able to allow remote work for a variety of reasons, including decentralized workplaces, distant labor, and emergency scenarios such as pandemics and natural disasters. Because of this, ensuring business continuity is an essential component of every company’s plan to recover from a disaster.
IT services have evolved to the point that they are critical to the operation of enterprises. Even if you can locate information technology services and networking facilities both during and after a disaster, there is no assurance that the data and applications utilized by your firm will be safe. In a situation like this, you will need a powerful Remote Access solution that provides both security and flexibility.
Fortinet Fortigate VPN solutions all offer reliable protection thanks to their foundation in IPSec and SSL technologies. It provides a wide variety of solutions for individuals as well as organizations, including VPN clients, clientless experiences provided by FortiAP, thick clients, and other options.
Who is it recommended for?
Fortinet is an expensive system. The FortiGate product is very popular for site protection and the software and cloud options are relatively new. The company produces a range of modules that you can load onto a FortiGate plan but the total cost will work out a lot higher than the Forepoint ONE package.
Pros:
- Uses machine learning and AI to detect and stop threats
- Can identify threats even when embedded in encrypted traffic via SSL inspection
- Ideal for enterprises and MSPs
Cons:
- Better suited for larger environments
Your users won’t have to create new accounts if you use Fortinet Fortigate since it interfaces seamlessly with Microsoft Active Directory (AD) and other Single Sign-On (SSO) systems. In addition to this, it assigns users to one of three distinct categories—Basic Teleworker, Power User, and Super Admin—so that specific permissions may be assigned to each group. Your system administrators will have less work to do as a result of these features as well.
6. Endpoint Protector
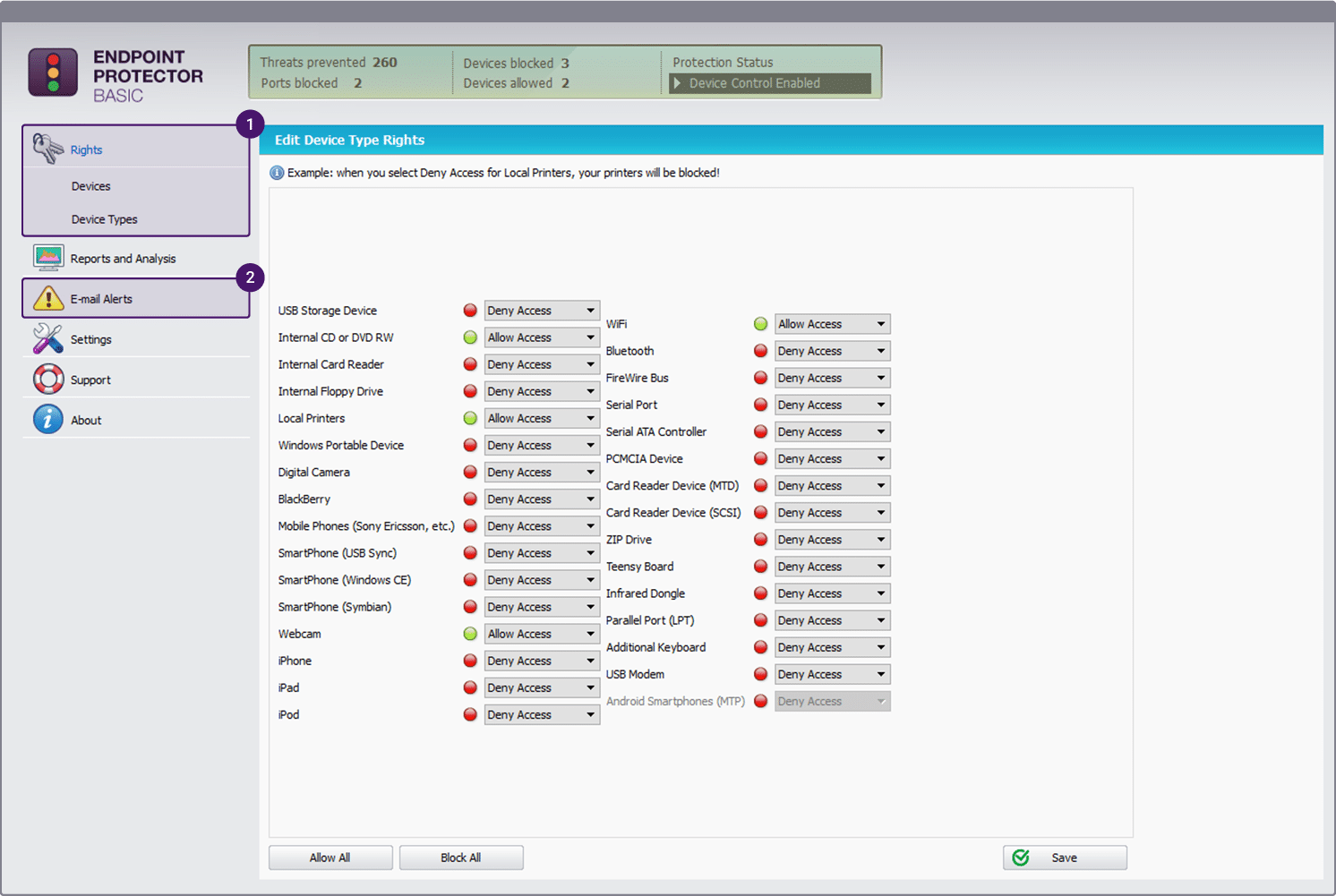
Endpoint Protector is a Data Loss Prevention (DLP) product that works across several platforms. Through sophisticated data loss prevention on several operating systems, this all-encompassing DLP solution will find, inspect, and safeguard the private and sensitive information you have. It protects data both while it is being transferred and when it is stored.
Key Features:
- Device Control
- Manage Computer Rights
- Cross-platform
- Extensive Number of Device Types
Why do we recommend it?
Endpoint Protector is a DLP package, so it doesn’t include many of the application and connection protection features in Forcepoint ONE. This service includes sensitive data discovery and classification and then implements controls on data access and movement. This matches the Forcepoint DLP plan rather than the full Forcepoint ONE package.
It puts a complete end to data leaks and data thefts and provides control of portable storage devices that is perfect. Within the endpoint, protectors are modules that are packed with features.
By monitoring all of the entry and exit points, it places restrictions on the material that has been predetermined by the administrator or management of the business. The Endpoint Protector’s device control module and content-aware protection module are both utilized in the process of protecting data while it is in transit. The content-aware protection module is in charge of monitoring the data that is sent between all of the online apps, while the device control module monitors all of the peripherals that are connected to your computer system.
Who is it recommended for?
Endpoint Protector is an easy-to-use data protection system and malware blocker because it prevents all software from running on an endpoint by default. The administrator then creates a list of allowed packages. This automatically prevents users from installing their own software and it kills all malware.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
It performs a scan of the information that is stored on the user’s machine and provides you with the ability to take any required corrective measures for data that is “at rest”. The scan is based on the sensitive content rules of your company. Endpoint Protector’s eDiscovery module protects data while it is at rest.
Forcepoint One & Alternatives FAQs
What are some key features of Forcepoint One?
Key features of Forcepoint One include cloud access security broker (CASB) functionality, secure web gateway (SWG) capabilities, endpoint protection, and data loss prevention (DLP) features.
What types of organizations can benefit from Forcepoint One?
Any organization that needs to secure cloud applications, endpoints, and network traffic can benefit from Forcepoint One, including small and medium-sized businesses, enterprise organizations, and government agencies.
Can Forcepoint One integrate with other security solutions?
Yes, Forcepoint One can integrate with other security solutions such as security information and event management (SIEM) tools, as well as network and endpoint security solutions.
What are some alternatives to Forcepoint One?
Alternatives to Forcepoint One include other cloud security solutions such as CrowdStrike Falcon, Barracuda CloudGen Firewall, and Zscaler.