Dealing with viruses and malware is a big headache for any size business. Thousands of dollars are spent each month by enterprises in web gateways subscriptions. The worst part is most of them still face viruses and malware invasions in their system.
In this blog post, we’ll cover the top 11 best secure web gateways for small and enterprise networks.
Here is our list of the best secure web gateways:
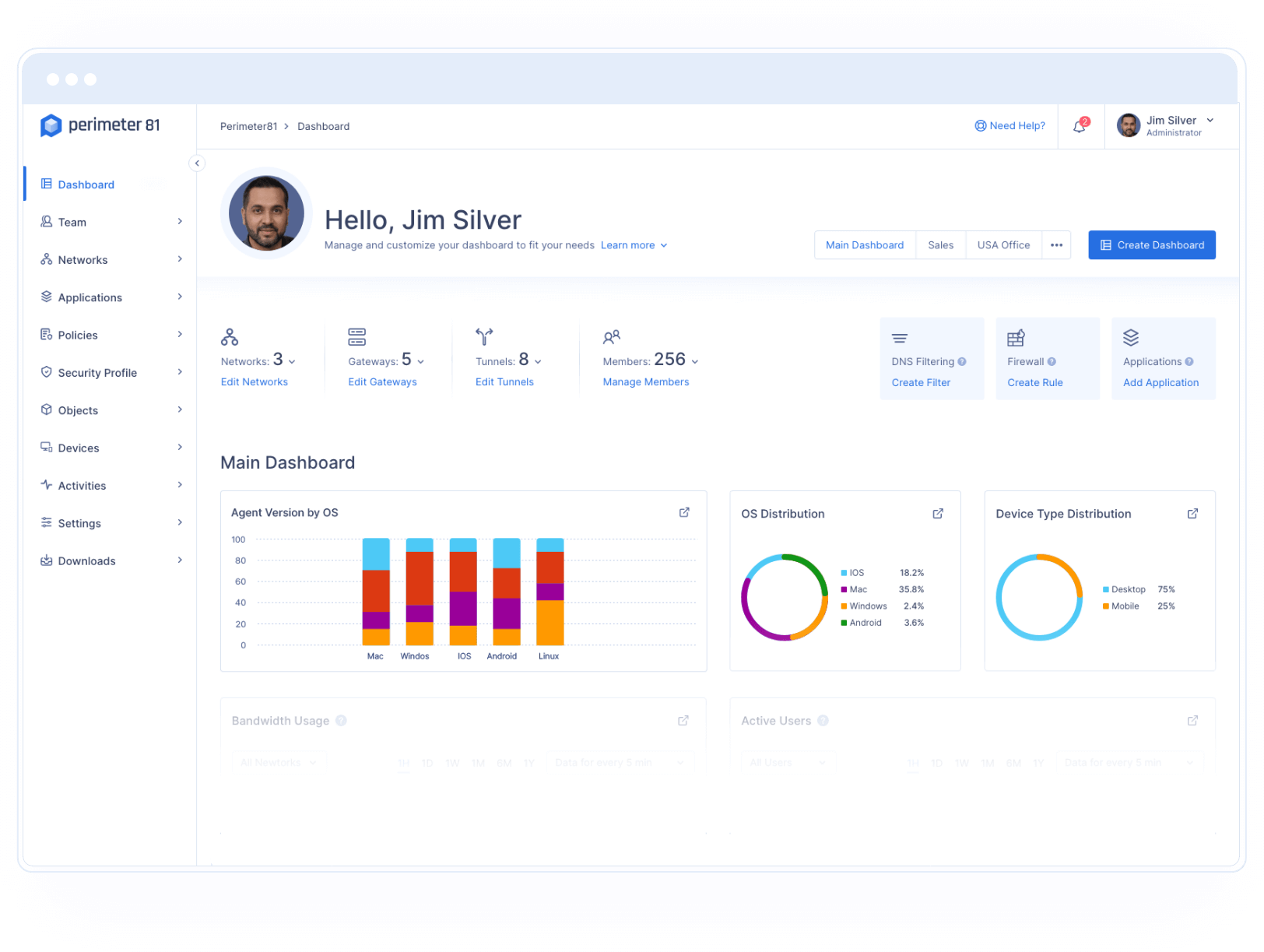
- Perimeter 81 – GET FREE DEMO Using Perimeter 81 Web security systems, users are prevented from accessing websites that may be dangerous or unsuitable. The service is hosted on the cloud. Start with a free demo.
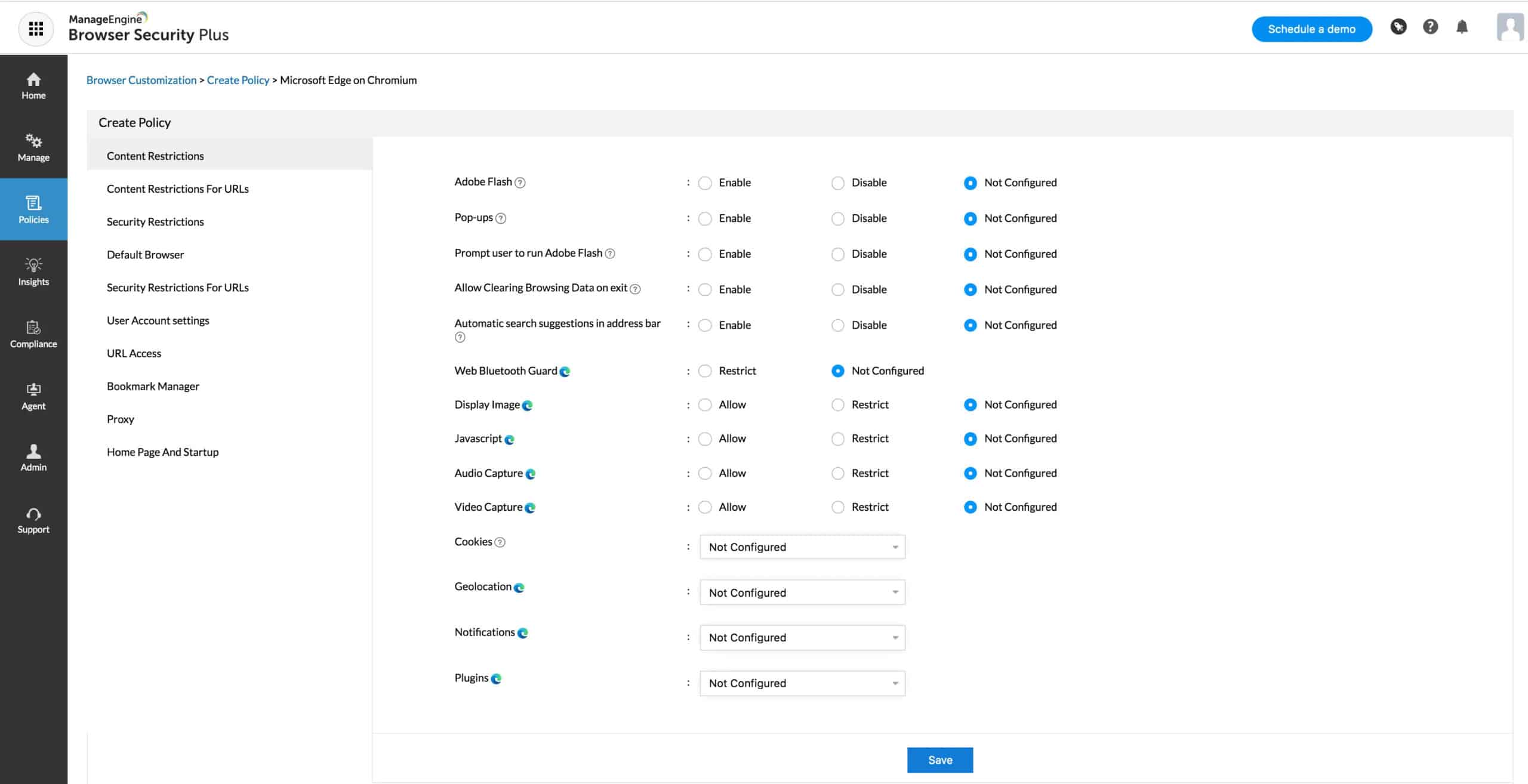
- ManageEngine Browser Security Plus – FREE TRIAL A software tool that helps organizations defend against web-based threats, such as malware, phishing attacks, and other cyber threats. Get a fully functional 30-day free trial.
- Symantec Secure Gateway Secure Gateway from Symantec. A cloud-based web gateway with cloud access security, data loss prevention, enhanced threat protection, and email security is offered.
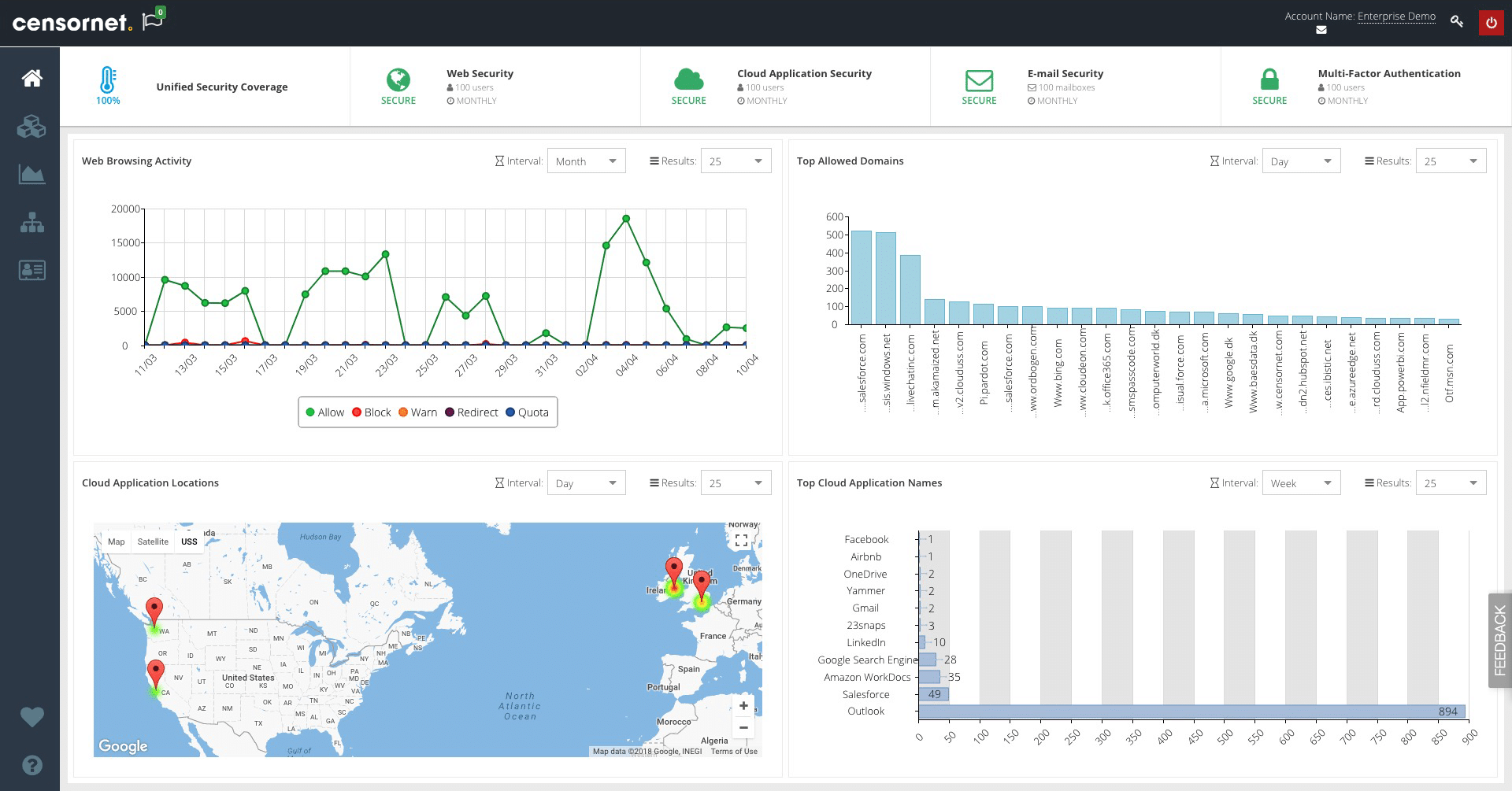
- Censornet Web Security Filtering out offensive text and images is the main goal of this content filter. Encrypted messages can be processed by this tool.
- Barracuda Web Security Gateway Firewall for the Internet of Things even when harmful code is encoded, a remote content filter can still detect and stop it from running.
- Forcepoint Web Security Firewall with URL filtering, data loss protection, and powerful malware detection powered by Forcepoint Web Security.
- McAfee Web Gateway Anti-malware, threat prevention, and an outbound inspector to prevent data theft are included. Other security solutions are also integrated with it.
- FortiProxy Web filtering, DNS filtering, antivirus, intrusion prevention, and data loss protection are included in this web threat intelligence solution for small and medium-sized businesses, making it perfect for SMEs.
- N-able Mail Assure It is a cloud-based email threat prevention solution that checks outgoing emails for data loss. Begin a 30-day free trial now.
- Sophos Web Gateway A web-based security gateway by Sophos For security reasons, this traffic monitor inspects both incoming and outgoing internet signals.
- Zscaler Web Security Zscaler Web Security is a cloud-based system that filters URLs and DNS, as well as a firewall, antivirus, and anti-spam.
The Best Secure Web Gateways
Our methodology for selecting secure web gateways
We reviewed various secure web gateways and analyzed the options based on the following criteria:
- Support for enterprise environments
- Reporting and auditing capabilities
- Simple configuration and monitoring
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
1. Perimeter 81 Secure Web Gateway – ACCESS FREE DEMO
Perimeter 81 runs a Web filtering system that protects the business’s network and endpoints from harmful infections that can be spread through websites.
The automatic site access blocks also look for fake websites that look like legitimate sites by having login screens that look real. These sites are used to get people’s passwords who don’t give them back. Businesses can’t get to imposter websites through the Secure Web Gateway, making them impossible.
System administrators can also set up their own filtering rules with the help of this tool. These can be used to ensure that your company doesn’t allow you to use the Internet at work. It makes it easier to keep company resources from going to bad websites. Attempts to get to sites that aren’t supposed to be there are kept track of.
This system runs in the cloud so that the administrator dashboard can be accessed from any computer with a web browser, like Chrome. The software isn’t limited to protecting employees in one place. It can also protect the devices of workers who work from home.
The system places a background agent on each device that is being protected. This makes sure that individual devices can be protected, not just those on the company network behind a firewall, which is why this is important.
Pros:
- Cloud-based software with device-agents
- Block all potentially harmful sites
- Detect fake and inactive websites
Cons:
- Would like to see a free trial
The service helps protect against types of attacks that most firewalls can’t see. An internet privacy service and DNS filtering are part of the package.
You can start by accessing a free demo.
2. ManageEngine Browser Security Plus – FREE TRIAL
ManageEngine Browser Security Plus includes features like web filtering, malware detection, and real-time monitoring to protect against web-based threats.
Key Features
- Advanced web filtering based on content
- DNS-based protection against malicious URLs
- Automated alerts based on web activity
Browser Security Plus can block access to malicious websites, prevent the download of malicious files, and detect and remove malware that has already been downloaded. It can also protect against phishing attacks by blocking access to known phishing websites and warning users of potential phishing attempts. Overall, Browser Security Plus can help organizations improve the security of their networks and devices by protecting against web-based threats.
Pros:
- Highly customizable content filtering
- Robust reporting capabilities, suitable for enterprise networks
- It can support large teams due to its scalability
- Flexibility to run on different operating systems
Cons:
- The ManageEngine ecosystem is extensive and may require time to learn all of its features
Download: Click here to download and start using this tool.
3. Symantec Secure Gateway
The Symantec Secure Gateway is a cloud-based web gateway that integrates into an enterprise’s security stack. Data loss prevention, sophisticated threat protection, email security, and a cloud access security broker are all part of the package. You may authenticate users and analyze encrypted communications as part of Symantec Secure Gateway’s sophisticated threat detection capabilities.
Symantec Secure Gateway uses the Symantec Global Intelligence Network’s real-time threat intelligence to keep you ahead of new threats. Cyberattacks are detected by the Symantec Global Intelligence Network, which uses machine learning and image analysis. Global security operations centers receive around 1.2 billion online requests every day.
Using the Symantec Secure Gateway with the Symantec Integrated Cyber Defense Platform provides you with the ability to automate the remediation of threats. To reduce the risk to the network, known threats might be placed on a blocklist. Automation aids in the rapid demise of dangers.
Pros:
- Updating client databases is possible by utilizing a global network of intelligence sources.
- Ensures that threats are automatically remedied.
- Businesses that employ numerous cloud services may find this option useful.
Cons:
- Additional alternatives for reporting on compliance can make it more reliable.
4. Censornet Web Security
Internet material may be filtered using Censornet Web Security, a cloud-based web security solution. The program prevents the downloading of offensive, unlawful, viruses, and unsuitable pictures. This add-on combines AI and deep learning to automatically detect inflammatory, extremist, or adult photos with few false negatives.
Advanced anti-malware and threat intelligence are used to combat more sophisticated attacks. Additional security is provided by processing encrypted SSL/TLS communication. With an average response time of 35 milliseconds, Censornet Web Security provides employees with a high level of responsiveness.
Security may be managed across the network through the Guest and Captive portals of Censornet Web Security. Policies can be created by the user and applied to specific network devices. Categories, groups, and keywords can be used to restrict or permit access to specific devices.
Pros:
- Better suited for educational institutions and safeguarding kids from inappropriate web content.
- Employs artificial intelligence-based approaches and picture fingerprinting to prevent explicit material from being shown.
- Content may be restricted based on URL, keyword, and category.
Cons:
- The port mapping tool may be improved to make it more user-friendly.
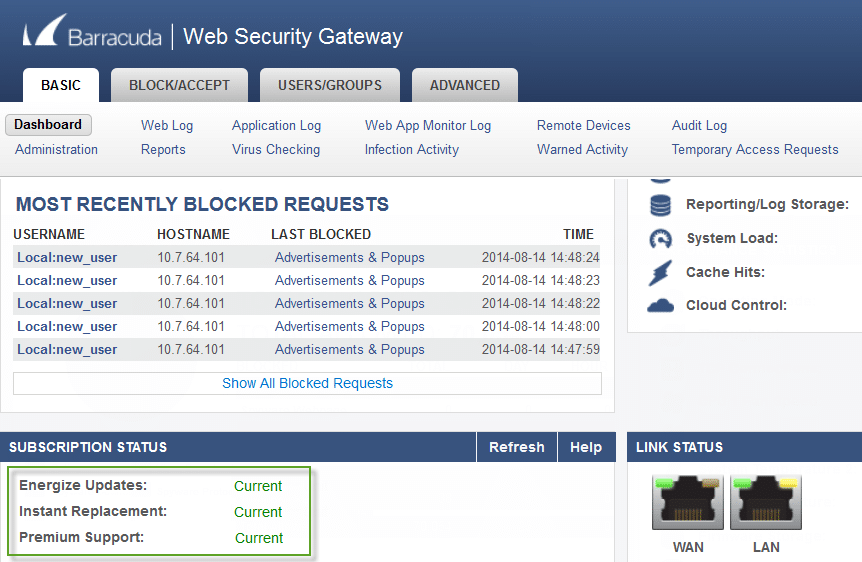
5. Barracuda Web Security Gateway
If your company’s goal is to keep its network free of viruses and malware, you’ll want to use Barracuda Web Security Gateway. The program may inspect SSL-encrypted communication, and online material can be remotely filtered. Antivirus and spyware are only a few of the tools that Barracuda Web Security Gateway employs to keep you safe online.
A cryptographic hash database, for example, is used by Barracuda Advanced Threat Protection (ATP) to screen incoming files for harmful activities. There is no risk to the larger network since any files that don’t match are forwarded to a virtual sandbox for verification.
Additionally, the platform provides dashboards that allow you to monitor both threats and user activities. When a security incident occurs, the app will notify you with an alert. After an event, you may utilize a reporting function to see how it went.
Pros:
- Deployments might be on-premises, on the cloud, or in a combination of the two.
- Redirects DDoS assaults from network infrastructure to a different location.
- Additional protection is provided through email encryption.
Cons:
- The UI for NOCs could use additional data visualization
6. Forcepoint Web Security
Forcepoint Web Security provides URL filtering, data loss prevention, and sophisticated malware detection (AMD) in the cloud-based configuration. More than 10,000 analytics and machine learning and behavioral baselines are included in Forcepoint Web Security’s Advanced Classification Engine (ACE).
Forcepoint Web Security’s primary protection against malware is the AMD function. AMD utilizes cloud sandboxing to isolate the malicious code to protect your network from malware. Removing risk factors and returning to regular operations becomes easier with sandboxes in place.
Since fingerprinting assaults can be detected with 100% accuracy, the approach can also protect against less visible risks. The data loss prevention feature of Forcepoint Web Security can protect your data in the case of an attack or a disaster. One central console can efficiently handle all of your data loss protection strategies.
Pros:
- The interface is straightforward to understand.
- Detects and eliminates threats through the use of fingerprinting and behavioral analysis.
- A cloud-based sandbox environment is capable of containing hazards.
Cons:
- Could benefit from more self-help documentation
7. McAfee Web Gateway
A well-known online filtering tool, McAfee Web Gateway is noted for its powerful anti-malware capabilities. McAfee Web Gateway can look for malicious code in HTTP, HTTPS, and SSL communications. By this, I mean that even deep within internet information, the technology can detect risks.
Moreover, McAfee Web Gateway’s antivirus protection is excellent. Look up files’ reputations and discover infections with the help of the McAfee Global Threat Intelligence (GTI). Assigning a reputation score to websites, emails, and IP addresses helps McAfee GTI identify those with the most danger.
Security measures built into McAfee Web Gateway are designed to prevent the loss of critical data from the network. Outbound traffic is scanned for data loss prevention to guard against the loss of company assets. Encryption is used to safeguard data stored in the cloud from unauthorized parties.
Pros:
- It uses a sophisticated correlation engine to assist in the speedier detection and elimination of threats.
- Integration with Active Directory environments is seamless.
- Large networks were taken into consideration when designing the system.
Cons:
- More integration possibilities would be beneficial.
8. FortiProxy Web Gateway
Fortinet’s Secure Web Gateway solution, FortiProxy, is a stand-alone product. Data leak protection, antivirus, web filtering, DNS filtering, and application restrictions are just a few of the features that FortiProxy has to offer.
It also provides traffic shaping and caching and support for the ICAP Client/Server protocol and remote access through a VPN. Integration with Fortinet’s Security Fabric enables it to use zero-trust web surfing, sandboxing, and central reporting.
The Secure Web Gateway may thoroughly examine SSL and SSH traffic, which detects risks that could otherwise go undetected. Both transparent and explicit forms of L2/L3 deployment are available for Active/Passive clusters for failover and Active/Active clusters (scalable to a maximum of 8) with the option for single cache collaborative storage.
Threat Intelligence is supported by FortiGuard Labs, with over 200 researchers in 31 countries committed to detecting new threats. The FortiGuard online filtering service, for example, blocks more than 150,000 URLs each minute. Certain websites can even be blacklisted or whitelisted.
User access policies can be specified for authenticated web application control. Social media platforms can be restricted by user or group, for example. Three thousand applications may be supported by this tool. To protect important files from slipping into the hands of the wrong people, there is data loss prevention (these files can also be watermarked or fingerprinted).
Pros:
- A web gateway protects against enormous quantities of traffic.
- L2/L3 traffic may be inspected.
- Long-term usage of more than 3000 applications is supported.
Cons:
- Users/sessions can be used as a metric for determining the cost of a subscription.
9. N-able Mail Assure System
The N-able Mail Assure system used to be provided by SolarWinds MSP, but now it is provided by N-able. Mail Assure can be added as an extra service by MSPs. The MSP can include the supervision of technicians in its pricing plan when it sells Mail Assure to its customers, as long as they agree.
If you work for an IT department, you should also use the Mail Assure system. Even though N-able sells this service to MSPs, there is no reason why you should not, too.
The Mail Assure system is on N-able servers, so all MSP’s clients’ emails must go through that system via a VPN. The Mail Assure server receives all incoming emails first then sends them to the client’s computer through the VPN. This is also how it works.
As soon as an email meant for the customer arrives at the Mail Assure server, the server checks for security threats like spam and phishing attempts, as well as address spoofing. It also checks for malicious content and poisoned links.
When N-able serves its customers worldwide, it makes a threat intelligence database from all of the attacks that it sees on them. This centralized attack profile means that any threat found in one part of the world can be used to protect all of the other users of Mail Assure.
It also checks for typical attack signatures and looks at an email address blacklist sourced.
Besides continuity and archiving, the edge service also has these features. Encrypted archives of real emails are automatically kept and can be retrieved at any time. The continuity service includes online mailboxes for all accounts on the protected system. This means that all users can access and send emails even when the main email server is down.
Pros:
- There are no unexpected infrastructure charges because it is hosted in the cloud.
- Designed for managed service providers (MSPs) and multi-tenant environments
- If the system is self-learning and uses internal data to enhance threat detection, it is considered successful.
- Provides safety for email servers deployed in the cloud.
Cons:
- Can take a significant amount of time to explore the N-able platform.
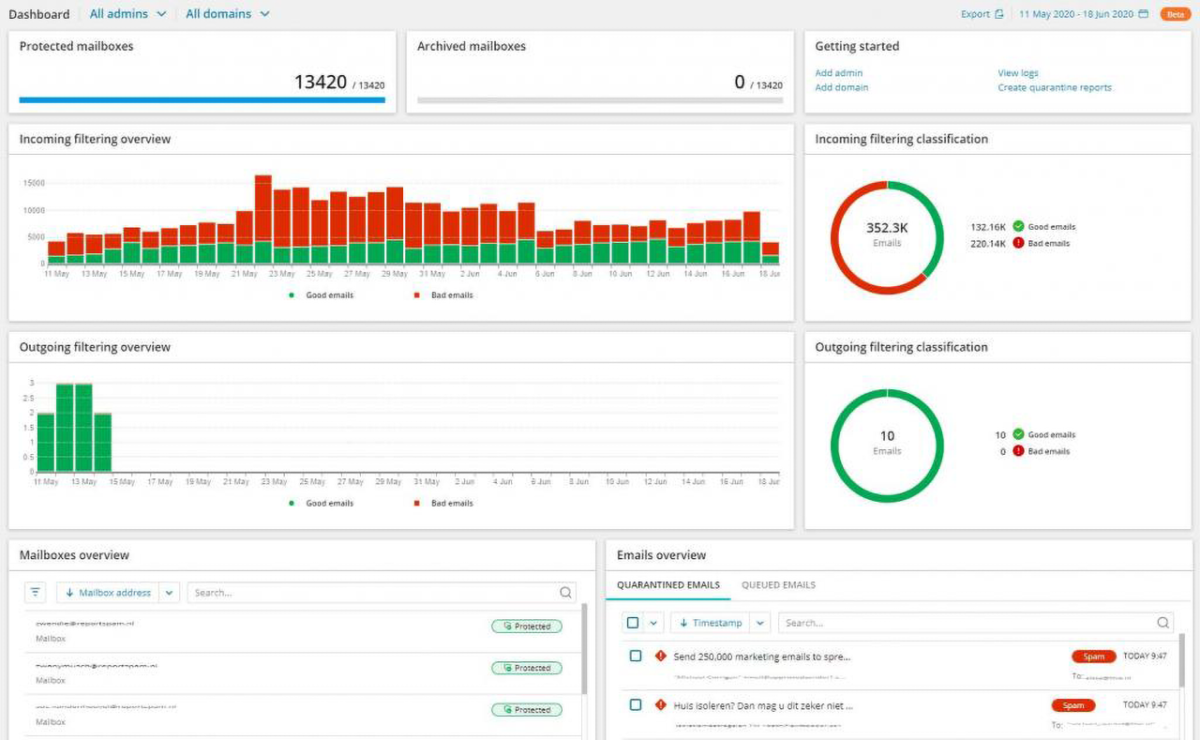
10. Sophos Web Gateway
The Sophos Web Gateway is a very powerful and secure web gateway device. This program has zero-day vulnerabilities, which can also read HTTP/HTTPS traffic. As a result, the software employs a staff of threat experts that track out the most recent malware threats. Behavioral analysis may also be used to identify and inhibit hateful conduct.
Because it features a comprehensive dashboard, Sophos Web Gateway stands out from the competition. You may monitor both incoming and outgoing traffic and other performance metrics from the dashboard.
Thanks to the dashboard, you may get a bird’s eye view of the situation whenever a security event occurs. On the Web Application Usage and Top Web Application Users graphs, you can observe if issues need to be fixed.
Using the platform, you can even design your security policies. Many choices are available to you, such as enforcing a bandwidth limit, restricting access to certain programs, and enforcing an acceptable use policy. More than 100 distinct report templates are available to help you capture security incidents in greater detail, making event management easier.
Pros:
- It can be installed remotely, on-premises, or in the cloud, among other options.
- This software protects against both inbound and outbound attacks.
- It can recover deleted emails while also serving as a data loss prevention tool.
Cons:
- Reporting appears to be standardized, with little room for personalization.
- Want to explore a broader range of integration possibilities
11. Zscaler Web Security
In addition to URL filtering and a firewall, Zscaler Online Security also includes anti-spam and antivirus software, as well as DNS filtering and other web security features.
With over 120,000 security updates every day to guard against the latest attacks, one of the benefits of being part of the cloud gateway is that any danger discovered by any user is instantly banned for all clients. Many other platforms have difficulty deciphering SSL traffic, but our program does.
The antivirus uses signatures from over 60 different threat sources to find new threats. In addition to monitoring security incidents, the software may also improve network speed. Web security service Zscaler can prioritize critical applications over less critical traffic.
There are a few ways to ensure that your files are safe from being lost or destroyed. Use Data Loss Prevention to keep your users’ information safe. In addition, a Cloud Application Security Broker and File Type Controls limit user access to apps and files on the network, respectively.
Pros:
- Based on a scalable cloud-based SaaS platform
- Provides Data Loss Prevention (DLP) functionality for file recovery and integrity monitoring.
- Can examine SSL traffic for malicious packers and flag them as such.
Cons:
- Setup can take longer than competing products.
Secure Web Gateways FAQs
How does a Secure Web Gateway work?
A Secure Web Gateway typically uses a combination of techniques, such as URL filtering, malware detection, and content analysis, to monitor and filter web traffic in real-time, blocking access to malicious websites and content.
What are some common features of Secure Web Gateways?
Common features of Secure Web Gateways include URL filtering, content filtering, malware detection, SSL inspection, application control, and user authentication.
How can a Secure Web Gateway benefit an organization?
A Secure Web Gateway can benefit an organization by providing protection against web-based threats, enforcing web usage policies, reducing bandwidth consumption, and enhancing network performance and productivity.
What types of threats can a Secure Web Gateway protect against?
A Secure Web Gateway can protect against a wide range of web-based threats, including malware, phishing attacks, botnets, and advanced persistent threats.
How can a Secure Web Gateway enforce web usage policies?
A Secure Web Gateway can enforce web usage policies by blocking access to certain websites and web applications, controlling user access based on user roles and permissions, and providing reports on web activity and usage.
What is SSL inspection, and why is it important for Secure Web Gateways?
SSL inspection is the process of intercepting and decrypting SSL traffic to analyze its content for potential security threats. SSL inspection is important for Secure Web Gateways because it enables them to detect and block encrypted web traffic that may contain malicious content or activity.
How can machine learning and artificial intelligence be used for Secure Web Gateways?
Machine learning and artificial intelligence can be used for Secure Web Gateways to automate the detection and analysis of potential threats and adapt to changing threat landscapes, improving the accuracy and efficiency of the solution.
How does a Secure Web Gateway differ from a firewall?
A Secure Web Gateway is designed specifically to monitor and filter web traffic, while a firewall is designed to protect an organization's network from a wide range of threats, including web-based threats, but also non-web-based threats such as malware and intrusions.