The setting of your operating system has a significant impact on the ransomware protection system that is going to be the most effective for you. For instance, you need to make sure that the ransomware scanner is compatible with the operating systems that you are using on your websites, and that it can communicate with those systems.
Additionally, if you store data in the cloud, you need to be sure that your antivirus software can recognize ransomware even before it is uploaded to your server. As well as these considerations regarding the operating system, there are a few more significant criteria to determine.
Here is our list of the best Ransomware Scanners:
- ManageEngine Endpoint Central – FREE TRIAL This remote monitoring and management package provides a Security edition that has an Anti-Ransomware unit with an integrated backup service. Available as a SaaS platform or for installation on Windows Server. Get a 30-day free trial.
- CrowdStrike Falcon Insight CrowdStrike provides this significant SIEM operation with a threat intelligence feed, which in turn provides the operator with information to inform its threat-hunting efforts.
- SpinOne A ransomware protection, backup and recovery, data loss prevention, and compliance reporting cloud solution that is designed to work with the major SaaS productivity platforms.
- BitDefender GravityZone A suite of security applications that performs antivirus scans at multiple points throughout the system, including the moment just before data is uploaded to a backup storage location.
- Rapid7 InsightIDR System The service will install agents on every endpoint so that it can do direct scans for ransomware and other forms of malware. This service is also helpful for detecting potential intrusion attempts.
- Exabeam A next-generation SIEM that identifies an abnormal activity, such as actions taken by ransomware, using methods from artificial intelligence. This cloud-based technology will also protect against malicious software and unwanted visitors.
- LogRhythm’s Next-Gen Security Information A collection of anti-malware programs that work together to detect, stop, and remove ransomware as well as other types of malicious software and invaders. They can be purchased as a service provided over the cloud, as an appliance, or as software for Windows Server.
If you store a significant amount of personally identifiable information on your system, you may need to give serious thought to investing in several different solutions to fully secure your business from ransomware attacks.
Our methodology for selecting the best Ransomware Scanner tool:
We’ve broken down our analysis for you based on these key criteria:
- Compatibility with various operating systems, ensuring broad applicability.
- Cloud data protection capabilities, critical for modern digital environments.
- Advanced threat detection methods, such as AI-driven user behavior tracking.
- Comprehensive endpoint management, including mobile and workstation security.
- Integration of backup and recovery solutions for post-attack resilience.
The Best Ransomware scanners
We have compiled a list of some good security suites that will protect you against ransomware by using the selection criteria that were presented earlier in this article.
1. ManageEngine Endpoint Central – FREE TRIAL
ManageEngine Endpoint Central gives IT departments tools to monitor and manage a fleet of endpoints. The package has a number of editions that have an increasing number of facilities with each higher plan. The top plan is the Security Edition, which provides data loss prevention tools. ManageEngine is offering an Anti-Ransomware add-on to this package for free while it’s in Beta.
Key Features:
- Spots unexpected file changes
- Scans processes for unauthorized software and kills them
- Backs up files
- Automatically restores damaged files
- Logs activities for post-attack analysis
- User behavior tracking with AI-based assessments
- Alerts for suspicious activities by people or processes
Why do we recommend it?
We recommend ManageEngine Endpoint Central for its comprehensive endpoint management capabilities and robust anti-ransomware features. It efficiently spots unexpected file changes, terminates unauthorized processes, and backs up and restores files, making it a reliable tool for both prevention and recovery from ransomware attacks.
The Anti-Ransomware unit is an extra layer of protection on top of all of the features of the Security Edition, which itself adds extra features onto the facilities available in the UEM and Enterprise plans. So, you end up with a very large package of endpoint management and data security services.
The Endpoint Central system watches over mobile devices as well as workstations. It can track devices, lock them, and wipe them remotely if they get misplaced or stolen. Security Edition users also get the software management features of the Enterprise plan, including OS deployment, device onboarding with software profiles, patch management, software license management, and mobile app controls.
Who is it recommended for?
ManageEngine Endpoint Central is highly recommended for IT departments managing a diverse range of endpoints, including both mobile devices and workstations. Its suitability for varied operating systems and features like AI-based user behavior tracking make it ideal for businesses seeking a multi-faceted approach to ransomware protection.
Pros:
- Manages endpoint hardware and software
- Provides mobile device management services for fleet devices and BYOD
- Includes an automated patch manager
- Discovers sensitive data and protects it
- Backs up files and restores them after unauthorized changes
- Detects rogue software and kills its processes
Cons:
- No network management features
ManageEngine offers a Free edition of Endpoint Central. That’s a great choice for small businesses because it will manage 20 workstations and five servers. However, that plan doesn’t get the Anti-Ransomware unit. You have to go all the way up to the top plan, the Securitry edition to get the ransomware protection system. You can get a 30-day free trial of the Security edition, which is available on the SaaS platform or with the download for Windows Server, and the Anti-Ransomware unit is available during the trial.
EDITOR'S CHOICE
ManageEngine Endpoint Central stands out as our top choice for a ransomware scanner. Its robust Anti-Ransomware unit, currently free in its Beta version, offers comprehensive security enhancements on top of its Security Edition. The tool excels in managing and securing endpoints, an essential aspect in today’s diverse device environments. Its ability to spot unexpected file changes, terminate unauthorized software, and restore damaged files ensures a high level of data protection.
Its AI-based user behavior tracking and alert system for suspicious activities provides an advanced layer of security against ransomware threats. Its added value is evident in its mobile device management, automated patch management, and sensitive data protection. The tool is available both as a SaaS platform and for Windows Server installation.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/products/desktop-central/anti-ransomware.html
OS: Cloud-Based
2. CrowdStrike Falcon Insight
A cloud-based service and on-premises components are both included in the CrowdStrike Falcon Insight offering. The on-premises agents are deployed as a next-generation antiviral software package, whereas the cloud system is a service that provides SIEM. In addition, the agents can be purchased as a solo product under the brand name Falcon Prevent.
Key Features:
- Detects zero-day ransomware in addition to other recently discovered forms of malware
- Integrates features present on each device with a monitoring component hosted in the cloud
- Deploys a next-generation AV system in addition to a SIEM
- Consists of UEBA for activity baselining
- Is provided with a feed of threat intelligence
- The installation of the endpoint software is compatible with all operating systems
Why do we recommend it?
CrowdStrike Falcon Insight is recommended for its advanced ransomware detection capabilities and comprehensive endpoint protection. Its ability to detect zero-day ransomware and integration of SIEM features with endpoint security make it a formidable tool against sophisticated cyber threats.
Because the device agents can function on their own, endpoints are still protected even when they are not connected to the network. This service runs continuously, collecting activity samples and searching for unusual occurrences. The presence of a possible threat causes certain steps to be taken, such as terminating programs, deleting files, suspending user accounts, and isolating the device from the network. One example of this type of malware is ransomware. This includes a cloud-based service that is similar to SIEM with endpoint protection modules that incorporate features of next-generation antivirus software.
The log messages are gathered by the agents, and then they are uploaded to the cloud service. This centralized system conducts secondary scans on the activity data and alerts the other endpoints if an agent finds a problem. CrowdStrike provides this significant SIEM operation with a threat intelligence feed, which in turn provides the operator with information to inform its threat hunting efforts.
Who is it recommended for?
This tool is particularly suited for organizations looking for a robust security solution that combines HIDS, endpoint protection, and advanced threat detection. It’s ideal for businesses that need a versatile solution that can be deployed on-premise or in a cloud-based architecture.
Pros:
- Doesn’t rely on only log files to threat detection, uses process scanning to find threats right away
- Acts as a HIDS and endpoint protection tool all in one
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Can install either on-premise or directly into a cloud-based architecture
- Lightweight agents won’t slow down servers or end-user devices
Cons:
- Would benefit from a longer trial period
Because the strategy that is implemented by CrowdStrike Falcon Insight can spot new ransomware and malware before the cybersecurity industry becomes aware of it, the likelihood of a company that operates the software becoming an early victim of a new strain of ransomware is significantly reduced. This method is also very effective in identifying dangers coming from within the organization as well as outsiders.
3. SpinOne Ransomware Protection
SpinOne is a package of data protection technologies that are supplied from the cloud and connects to three of the most extensively used cloud platforms, namely Microsoft 365, Google Workspace, and Salesforce. SpinOne is a product of Spin.ai and is known as SpinOne. The scanning and removal of ransomware are both included in this bundle. The SpinOne platform has both a backup and recovery system as an integral part of its design.
Key Features:
- A service for backing up and recovering data
- Protection against ransomware
- Security for confidential information
- Monitoring and analysis of user activities and behaviors
- Methods of preventing automated ransomware attacks
Why do we recommend it?
SpinOne Ransomware Protection is recommended for its specialized focus on protecting data across cloud platforms. Its automated workflows for addressing ransomware incidents and quick recovery SLAs make it an excellent choice for robust cloud data security.
SpinOne offers automated workflows that can be used to deal with an encrypting ransomware incident that has been identified. Because ransomware cannot infiltrate cloud file storage systems unless it runs on a server hosted by a third party, SpinOne quickly cuts off API access to the filespace as soon as it detects an infection. The ransomware will not be able to infect any other files as a result of this.
Who is it recommended for?
This tool is best suited for businesses heavily reliant on cloud platforms like Microsoft 365, Google Workspace, and Salesforce. Its capabilities are particularly beneficial for companies prioritizing cloud data security and rapid recovery from ransomware attacks.
Pros:
- Specializes in protecting data stored across cloud platforms
- Includes both backup and recovery
- Prevents ransomware by isolating threats
- Includes a two-hour SLA for recovery
Cons:
- Better suited for cloud-based businesses
The malware will be contained within the quarantined files while the service searches through its activity logs to determine where it originated. After that, it compiles a report on its findings, removes the encrypted files, and restores the originals using replacements from the backup.
4. Bitdefender GravityZone
Bitdefender GravityZone is a suite of security products that, when used together, can defend any device on a network from ransomware and other forms of cybercrime. This package is quite effective in detecting malware entrance and conducting sweeps against malware, which take place at multiple places throughout the system. In addition, anti-virus software is installed on every endpoint, and this software examines all new files that are transferred to the device.
Key Features:
- Ransomware performs scans at all of the system’s essential areas, including endpoints
- A backup manager that does comprehensive malware scanning
- Maintaining a check on the files’ integrity
- It is a Vulnerability manager
Why do we recommend it?
Bitdefender GravityZone is recommended for its comprehensive approach to ransomware protection, combining endpoint security with backup management. Its dual-method threat detection and file integrity checks provide a layered defense against ransomware.
The backup manager included in this program is an essential component that is missing from a variety of other anti-ransomware systems. You can link this backup service to an existing cloud storage account that you already have, or you can build a cloud file space account with BitDefender. Before uploading a file to storage, this backup system examines each file to determine whether or not it contains malicious software. You will have the best possible security against encryption ransomware if you do this.
Who is it recommended for?
It’s ideal for organizations seeking an all-encompassing security solution that includes disk encryption, device control, and vulnerability management, alongside traditional anti-ransomware measures.
Pros:
- Simple UI reduces the learning curve and helps users gain insights faster
- Uses both signature-based detection and behavior analysis to identify threats
- Offers disc encryption on top of endpoint protection
- Includes device control options for locking down USB ports
Cons:
- Could use more documentation to help users get started quicker
GravityZone comes equipped with a vulnerability manager that not only strengthens the system’s defenses but also makes it more resistant to ransomware that uses RDP. In addition to that, it comes with a file integrity monitor that prevents the theft of data and encryption.
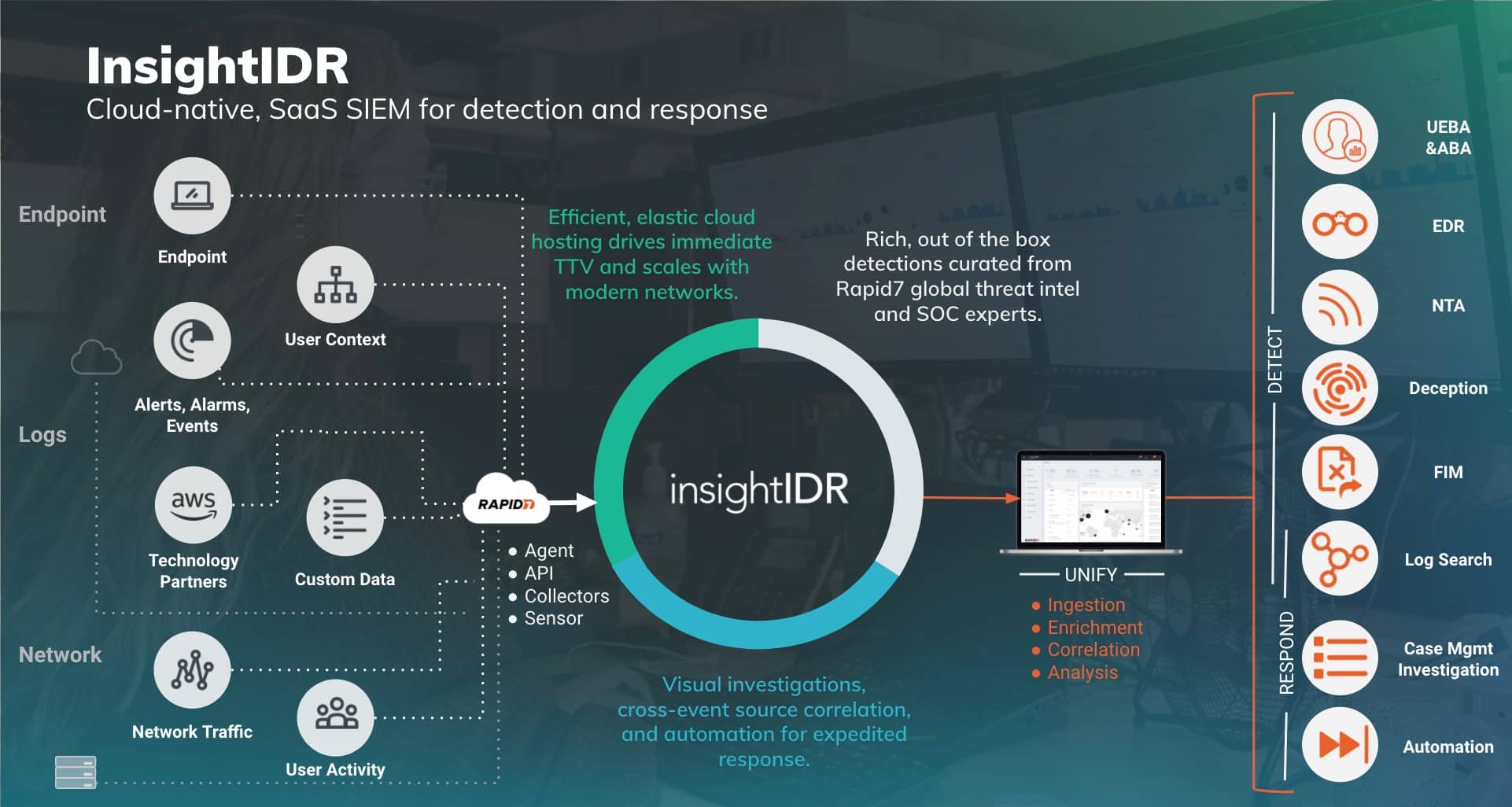
5. Rapid7 InsightIDR
Extended detection and response (XDR) is a service that is provided by Rapid7 InsightIDR. The software is hosted in the cloud but its primary focus is on defending endpoints, which are the locations where ransomware first makes its appearance. The service will install agents on every endpoint so that it can directly scan for ransomware and other forms of malware. This service is also helpful for detecting potential intrusion attempts.
Key Features:
- Endpoint agents identify newly created files that may be associated with ransomware
- A source of intelligence on the potential danger
- Honeypots are used to lure hackers and malware into the open
- Use of UEBA for activity baselining
Why do we recommend it?
Rapid7 InsightIDR is recommended for its extended detection and response capabilities, particularly its use of behavioral analytics and multiple data streams for advanced threat detection. Its automated remediation and honeypot features make it a strong contender in ransomware defense.
A feed of threat intelligence is included as one of the modules of InsightIDR, and UEBA is used to detect anomalies. The stream and the activity reports are both input into a SIEM system that does a rapid search for potential dangers. Honeypots are created on the network by InsightIDR, which is one of the program’s many useful features.
Who is it recommended for?
This tool is particularly suitable for organizations looking for a comprehensive XDR solution with a strong focus on endpoint security and innovative threat detection methods. It’s best for businesses that require up-to-date threat analysis and robust automated responses.
Pros:
- Leverages behavioral analytics to detect threats that bypass signature-based detection
- Uses multiple data streams to have the most up-to-date threat analysis methodologies
- Allows for robust automated remediation
Cons:
- Pricing is higher than similar tools on the market
- Some features may require paid plugins
By luring in malicious software and hackers, honeypots make it simpler to identify security breaches. A SIEM of the next generation that incorporates automation actions to prevent ransomware and other forms of malicious activity. This is a software-as-a-service platform.
6. Exabeam
Exabeam is a next-generation SIEM that is offered on a cloud platform that goes by the name Exabeam. This system works in conjunction with device agents to identify newly created files and keep a log of activity; this is an effective method for identifying ransomware.
Key Features:
- Rapid detection of ransomware files and other forms of malicious software
- UEBA baselines powered by AI for the detection of anomalies
- A threat intelligence stream from SkyFormation that has received high marks
- Responses that can be programmed to automatically stop ransomware and hacker activities
Why do we recommend it?
Exabeam is recommended for its next-generation SIEM capabilities, particularly its rapid ransomware detection and AI-powered UEBA baselines. Its integration with SOAR for automated responses adds an extra layer of security against ransomware and internal threats.
The log scanning procedure can be improved with the help of the threat intelligence feed that is included in the Exabeam system’s features. Device agents are responsible for the collection and uploading of logs, as well as the on-site analysis of the activity that they do. In addition, Exabeam’s anomaly detection system works in conjunction with UEBA to create a normal activity baseline, after which it searches for actions that deviate from the norm set by the baseline.
Who is it recommended for?
This tool is ideal for organizations requiring advanced SIEM features, incident response automation, and compliance reporting. It’s especially beneficial for businesses focused on internal threat detection and automated security orchestration.
Pros:
- Supports incidents response workflows, playbooks, and automation
- Offers usefully query features for filtering large datasets
- Can be used for compliance reporting and internal audits for HIPAA, PCI DSS, etc.
Cons:
- Lacks live network monitoring capabilities
- Wasn’t initially designed as a SIEM tool
The Exabeam service provides an additional module that may communicate with the various other systems on your network to prevent assaults. Orchestration, automation, and response to security incidents are the terms used here (SOAR). It does this by integrating with firewalls and access rights management systems, which together block ransomware and other forms of malware automatically. Additionally, it can thwart attempts at data theft and threats from within the organization.
7. LogRhythm NextGen Security and Event Management Platform
The LogRhythm NextGen SIEM Platform is composed of a group of individual security modules that are arranged in the form of a stack. This is an outstanding solution for detecting ransomware as it combines the gathering of local intelligence with the operation of a significant threat hunter.
Key Features:
- Collects event data from endpoints to detect the introduction of ransomware
- Coordination with endpoint agents and other onsite security products to feed activity data into a security information and event management system (SIEM).
- Reactions that can be programmed to stop malicious software and hacker activities
- A variety of deployment choices, such as on-premises installation, cloud-based service, and a network appliance
Why do we recommend it?
LogRhythm NextGen SIEM is recommended for its comprehensive event data collection and analysis, effectively detecting ransomware introductions. Its combination of AI, machine learning, and UEBA for behavior analysis enhances its capability in live data processing and threat detection.
The LogRhythm package is structured using services as its building blocks. UEBA for activity baseline analysis and a threat intelligence feed for identifying indicators of compromise are among these. In addition, log message uploads are augmented by real-time monitoring of network activities as well as device agent reporting on events occurring at endpoints. These serve as inputs for the security incident and event management system (SIEM).
Who is it recommended for?
This platform is best suited for organizations needing a user-friendly yet powerful SIEM solution with a variety of deployment options. It’s ideal for businesses seeking a customizable, AI-enhanced tool for real-time security monitoring and event management.
Pros:
- Uses simple wizards to setup log collection and other security tasks, making it a more beginner-friendly tool
- Sleek interface, highly customizable, and visually appealing
- Leverages artificial intelligence and machine learning for behavior analysis
- Does an excellent job at live data processing
Cons:
- Would like to see a trial option
- Data correlation could use improvement
When potential dangers are discovered, the LogRhythm system activates SOAR to coordinate block operations with the other security software running on your system. This service can instantly detect malicious software attacks, insider threats, and hacker activity, and then shut down those activities and threats. The on-premises software for LogRhythm is compatible with Windows Server, and it is also offered as an appliance and as a hosted SaaS system.
Ransomware Scanners FAQs
Can ransomware scanners be used to recover encrypted data?
No, ransomware scanners cannot be used to recover encrypted data. However, they can be used to detect and block ransomware activity before it encrypts data, which can help prevent data loss.
What is the difference between ransomware scanners and antivirus software?
Ransomware scanners are a type of antivirus software that is specifically designed to detect and block ransomware. However, they may not be as effective against other types of malware such as viruses and trojans.
How do ransomware scanners work?
Ransomware scanners work by using a combination of signature-based detection, behavioral analysis, and machine-learning algorithms to detect and block ransomware activity.
What are some common features of ransomware scanners?
Common features of ransomware scanners include real-time scanning, behavioral analysis, file integrity monitoring, and remediation capabilities.
How does machine learning help ransomware scanners detect threats?
Machine learning algorithms can analyze large volumes of data and identify patterns and anomalies that may indicate the presence of ransomware. This can help ransomware scanners detect and block threats that may not be detected by traditional signature-based antivirus solutions.