When it comes to cloud Container Security Tools, you are likely to find yourself in a pickle of sorts, as there are just so many to select from. There are a lot of different kinds of containers. Even though they have only been around for a couple of years, application containers have already become an essential building component of modern application development.
Containers have been popular, and this has drawn the attention of hackers. Therefore, container security has become an important area of interest to augment an already wide-ranging cybersecurity portfolio. In this article, we will go through the top container security tools you should know about.
Here is our list of the best Container Security Tools:
- Anchore A full container security workflow for teams, helping to automate the process of vulnerability discovery and remediation.
- Aqua Security Provides security support for orchestrators like Kubernetes, including vulnerability scanning and management.
- Cilium Provides network security amongst container programs that are transparent to the user.
- Black Duck Hub Τhe leader in container inventory and picture inventory.
- Clair A free and open-source program that provides static security and vulnerability analysis for Docker and application (appc) containerized applications.
- Grafeas Α container security scanning tool built by IBM and Google that uses container metadata API-based components.
- Qualys Container Security Provides security information on both the container host and the containers themselves.
- Sysdig Falco A container security monitor that is free and open-source, and it is designed to detect unusual activities in your applications.
- Docker Bench An open-source script created by Docker to help developers perform audits of containers with Docker Community Edition to ensure the containers comply with standard security best practices.
What is a container security tool?
Container security tools ensure that everything in your container is operating in the manner you intended. When it comes to container security, the process must be run continuously, not only protecting the container host, its network traffic, and its management stack, but also monitoring the integrity of your build pipeline, your application’s security, and the foundation layers of your application within the container.
Why is container security important?
As development rapidly moves to containers, the need for container security will become increasingly important. Because of the relative opacity of containers, as described above, security and the accompanying security technologies are crucial in the initial development phase. Container security must be done appropriately from the beginning before a significant incident occurs because containers in general — and the approaches required to secure them — are still in their early stages.
Security is still a key worry (if not the most important concern) for anyone involved in the development and deployment of containerized applications. Many argue that container security has already fallen behind and that the industry has now been placed into a position to play catch-up regarding remediation and improvement. Furthermore, while several security technologies help enterprises improve their security posture, many organizations do not have a comprehensive container security strategy.
The Main Benefits of Container Security
A successful container security program allows teams to overcome limitations they previously imposed on moving fast without compromising the integrity of their environments. The following are the primary advantages:
- Adding container security to application development and delivery does not cause delays for DevOps teams, and the environment’s overall security is not jeopardized as a result.
- When using containers, you just need to safeguard the host and the application rather than actual physical servers, integrations, and other factors that would normally increase the attack surface.
- It is quite simple to see what is inside an image; however, seeing virtual computers is often far more complex. This facilitates the identification of security concerns within containers more quickly.
- Containers provide you with peace of mind about the security of your program. With them, you can always update to the newest versions of your application by pulling images from whatever registry you like.
Challenges To Container Security
Despite the numerous advantages that containers provide, their usage is not without its difficulties, which must be considered.
For starters, containers provide attackers with a bigger attack surface on which to focus their efforts. To maintain standard configurations and container profiles, standard configurations and container profiles, shared kernel architecture must be secured. Containerization is built around shared kernel architecture, and this architecture, besides being important for ensuring the host, requires extra maintenance.
An important point of worry is that it is difficult to identify risks because of visibility. That makes it more difficult to tackle issues that need fixing.
The pictures used in containerized environments are continually being added to the organization’s private registry or hub, and containers executing the images are being spun up and taken down on a regular basis.
Because of the constant flux of alternating runtimes, it will be more challenging to detect images or containers that are not currently in use at the time of a scan at the Kubernetes stage. Consequently, executing container security scanning earlier in the build process is required to ensure that no security vulnerabilities are overlooked.
The Best Container Security Tools
Our methodology for selecting container security tools and software
We reviewed container security tools and analyzed the options based on the following criteria:
- Support for various containers and host environments
- Scanning methodology, automation, and effectiveness
- Support for root cause analysis and remediations
- A facility to analyze container security over time
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
While other open-source container security tools are available, the following are the best, most mature, and most widely used, as determined by their user groups.
1. Anchore
Anchore, Inc., headquartered in Santa Barbara, California, was formed in 2016 by Sad Ziouani and Daniel Nurmi to assist enterprises in implementing secure container-based workflows without sacrificing speed.
Some key features of Anchore are:
- Scans and collects vulnerability data from registries automatically.
- Registry solutions like Harbor, Quay, JFrog, DockerHub, AWS, Azure, and Google all have container registries.
- The CLI and Anchore Enterprise UI can be used to view reports and assessments. At the same time, webhooks can invoke additional system action.
- For developers, Anchore Enterprise provides a secure container workflow solution that does not slow down development.
- Analysis of container workloads is performed using open-source tools for image inspection and vulnerability scanning.
- Enables you to maintain control over containers via software inventory management (IAM) for container workloads in-house and in the cloud.
- It has zero security flaws like passwords and API keys in pictures.
- Identifies third-party software libraries, including DotNet, JAVA, and Python PIP, in addition to Node.js NPM, Ruby GEM, and DotNet.
Anchore Enterprise is a full container security workflow for teams, helping to automate the process of vulnerability discovery and remediation. It allows groups to conform to set industry security standards because it integrates effortlessly with a wide array of development tools and platforms. It is possible to audit and verify compliance throughout an organization using the Anchore Enterprise user interface, which gives insight to security teams. It may be used in air-gapped and public cloud environments designed for large-scale deployments. Anchore Enterprise uses Anchore Engine, a free program that allows users to examine image contents deeply for potential vulnerabilities.
Pros:
- Automates vulnerability discovery and remediation
- Offers a CLI and GUI version
- Offers a free version through Anchore Engine
- Supports various container environments
Cons:
- Can take time to fully explore all features and options
2. Aqua Security
Aqua Security protects container-based software. It provides security support for orchestrators like Kubernetes, including vulnerability scanning and management. To start, it is a security system that contains all of the containers’ programs. It keeps those apps secure and safe.
Some important features of Aqua security are as follows:
- Check images for security flaws and issues such as secrets, viruses, and configuration problems.
- Prevent unauthorized images from executing in your environment by configuring your firewall.
- Learning acceptable container behavior by machine learning, with consideration given to applications’ context.
- Network lateral movement is prevented via a container-level firewall that maps connections.
- Manages container access to secrets across several environments in a secure manner.
A series of tools and libraries exist to help developers when they are working to create a picture. They can scan photos to verify that they are clean, ensuring no known vulnerabilities, passwords, or secrets. The scanned images will also ensure that no security threats can render the image vulnerable. When aqua security identifies vulnerabilities, they disclose the flaws to the developers and offer fixes. Once it goes into production, Aqua Security’s containers will keep attackers out, ensuring that their content is safe.
Pros:
- Flexible cloud-native platform
- Supports vulnerability detection as well as present threats
- Supports complete automated deployment
Cons:
- Better suited for larger businesses
3. Cilium
Cilium provides network security amongst container programs that are transparent to the user. It is built on a new Linux kernel technology known as eBPF, which allows you to establish and enforce both network-layer and HTTP-layer security restrictions based on identifying the container or pod in which it is running.
Some key features of Cilium are:
- The support and community surrounding Cilium are exceptional, especially considering that it is an open-source project.
- A full set of instructions and documentation, as well as a dedicated Slack channel and even a weekly development meeting, are all available.
- Cilium is a network security filtering solution for Linux container frameworks such as Docker and Kubernetes that is API-aware.
- Cilium, which uses a new Linux kernel technology known as BPF, provides a simple and efficient approach to design and enforce both network-layer and application-layer security policies depending on the identity of the container or pod being protected.
It is driven by BPF (previously known as Berkeley packet filter), a technology found in the Linux kernel. The unique part of Cilium’s low-level implementation is that it allows you to apply and update security policies without having to change the application code or container configuration at any point.
Pros:
- Helps visualize container security through workflow visuals
- Can dynamically apply updates to applications
- Supports larger environments relying on microservices
Cons:
- Requires technical experience to use all features and options
Cilium was created in response to the dynamic life cycles of modern microservices development and the need for rapid container deployment.
4. Blackduck
Black Duck Hub is the leader in container inventory and picture inventory. They help their customers find vulnerabilities and discover what is inside images by indexing the contents of their digital assets. Black Duck OpsSight aids in the prevention of known open source issues from being put into production environments through the use of artificial intelligence. Using the assistant, you may quickly and simply identify the exact libraries, software packages, or binary files posing a security concern. The assistant will instantly provide you with a list of known remedies.
Some important functions of Blackduck are:
- OpsSight scans containers in your cluster and identifies known vulnerabilities, which is made possible with the extensive databases of known risks.
- OpsSight monitors your orchestration platform’s event streams for any changes that may occur in them.
- Scan findings are put into metadata in the container image, which means you can easily access it to scan for vulnerabilities in your container orchestration platform’s console.
- Identify and highlight any photos that include open source vulnerabilities that have been publicly publicised.
- Flag the images of containers that are a security concern since they’re violating open-source software policies.
- When newly identified vulnerabilities are uncovered that could affect container images inside your cluster, you will be notified.
Pros:
- Clean and easy-to-navigate interface
- Leverages AI to avoid publishing vulnerable applications
- Supplies known fixes and remediation options for issues found
Cons:
- Requires technical experience to use all features and options
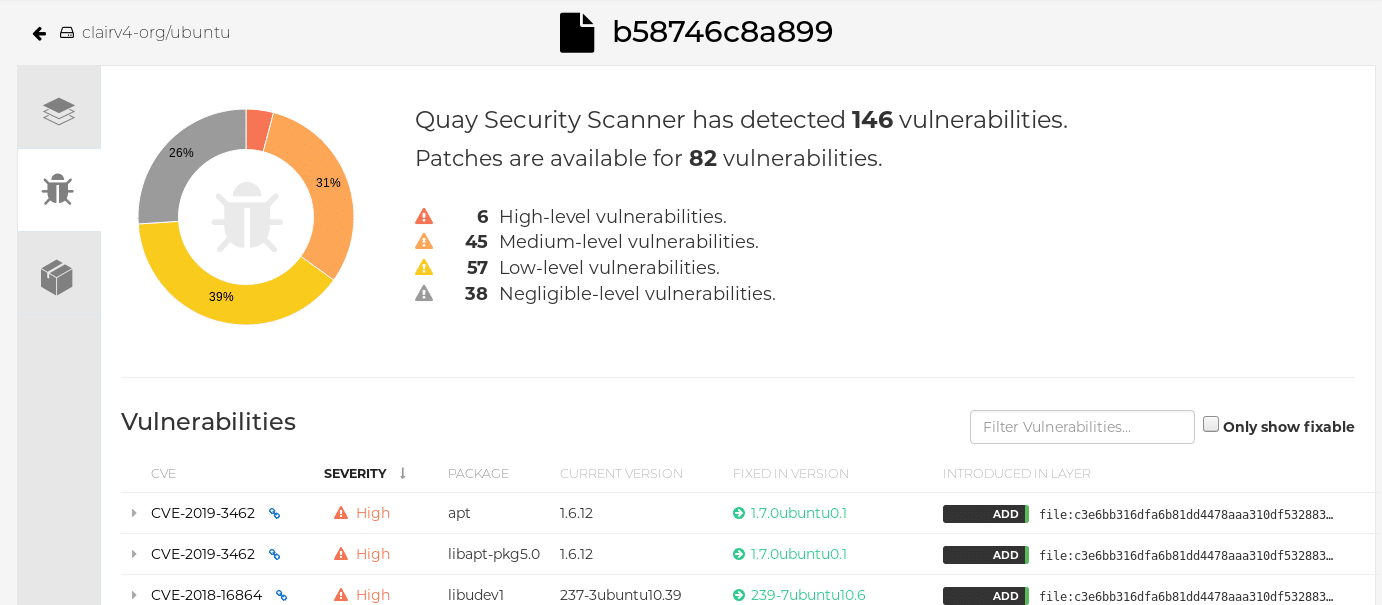
5. Clair
Clair is a free and open-source program that provides static security and vulnerability analysis for Docker and application (appc) containerized applications.
Clair features:
- Checks for current vulnerabilities and takes steps to prevent them from being exploited again in the future.
- This utility integrates with other tools using its REST API.
- Sends an alert when it detects a vulnerability in any of its systems.
- Gives an HTML report detailing the scan’s findings.
- Metadata is updated at regular intervals by this program.
In this case, it is an API-driven analysis engine that analyses for security issues in the containers at the application layer level. Through the use of Clair, you may create services that will continuously monitor your containers for potential container vulnerabilities. It alerts you to the presence of a potential threat within the container. It informs you of a potential threat in the container based on information from the Common Vulnerabilities and Exposures database (CVE) and other comparable databases, among other sources.
Pros:
- A completely free and open-source platform
- Offers a range of automated alert and remediation options
- Large community-backed project
- Simple monitoring through service creation
Cons:
- Not ideal for those looking to avoid open-source options
The National Vulnerability Database (NVD) will be consulted if any identified threat or issue has already been documented. The NVD will then obtain the relevant information and include it in the report.
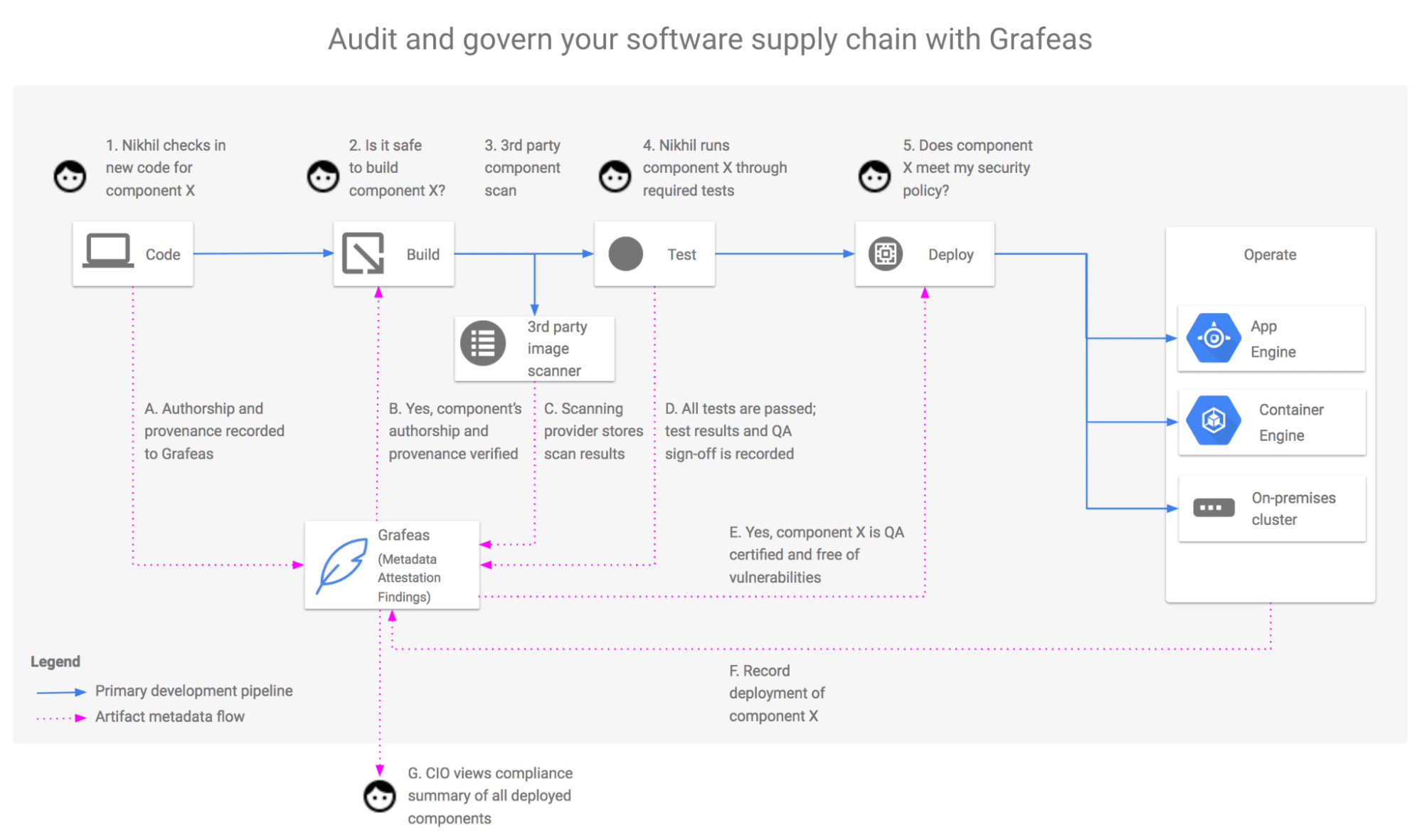
6. Grafeas
Grafeas is a container security scanning tool built by IBM and Google that uses container metadata API-based components. It enables the construction of projects by using the container metadata API to generate the necessary metadata about component relationships. Grafeas is a single-source repository allowing enterprises to manage and ensure compliance with all internal regulations by enforcing them across an ever-expanding number of development teams and pipelines. Grafeas categorizes metadata information into two categories: notes and occurrences. Notes are high-level summaries of specific sorts of metadata that have been collected. Occurrences are different from their instances, which convey information about how and when a particular note appears on the resource. Through this section, independent metadata providers can develop and maintain metadata on behalf of many consumers. In addition, it provides a comprehensive solution for fine-grained metadata access control.
Grafeas features:
- The Grafeas API may be used by software development, auditing, and compliance tools to store, query, and retrieve rich metadata about software components of all types.
- Using Grafaes metadata, Kubernetes clusters that employ Grafaes can have security policies enforced on them.
- Grafeas (which means “scribe” in Greek) is an open-source artefact metadata API that provides a standardised method for auditing and governing your software distribution chain.
- Grafeas establishes a metadata management API for containers, Virtual Machines, JAR files, and other software resources, such as script files.
- It is possible to specify and aggregate information on the components of your project using Grafeas software.
Pros:
- Offers a platform for full auditing, testing, and vulnerability discovery
- Great for larger companies looking to manage their compliance
- Offers a wide range of access control options
Cons:
- Can take time to full understand and explore the platform
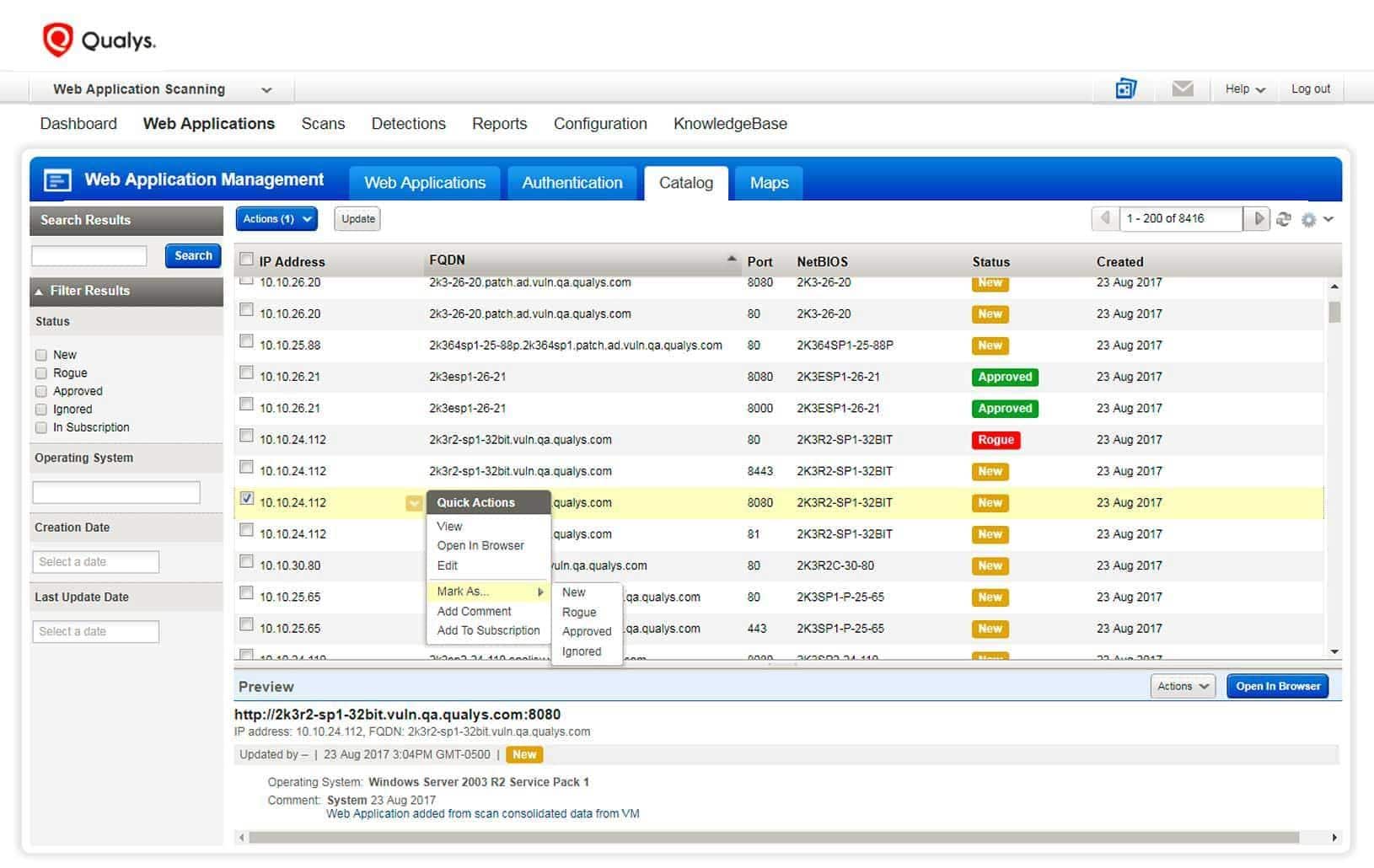
7. Qualys Container Security
Qualys Container Security provides security information on both the container host and the containers themselves. It also enables the user to identify and prevent security problems as they happen. Images, image repositories, and image-based containers are gathered by it. It is also valuable for learning whether photos are being saved on various hosts by installing plugins such as Jenkins or Bamboo or using REST APIsWeuncovering that containers have open network ports and determine whether these containers have elevated capabilities.
Qualys Key Differentiators:
- Secures containers regardless of whether they are on-premises or in the cloud
- Make policies that restrict images with known flaws and are more dangerous to use.
- By installing plugins such as Jenkins or Bamboo or using REST APIs.
- Identify and investigate images that contain high-severity vulnerabilities, unauthorized packages, and tags for earlier or test releases.
- Containers Runtime Security (CRS) provides information about what is going on inside running containers, as well as features to control the behavior of such containers.
- Finding and monitoring containers and photos in a central location
- Examine the metadata of containers and pictures that contain labels, tags, installed applications, and layers.
- Analyzing the wide variety of OSes, apps, and programming languages related to Linux’s contribution to container-centric OS design.
Pros:
- Great user interface
- Can track the usage and access of multiple images
- Supports native alerting and remediation
Cons:
- Ideal for SMBs
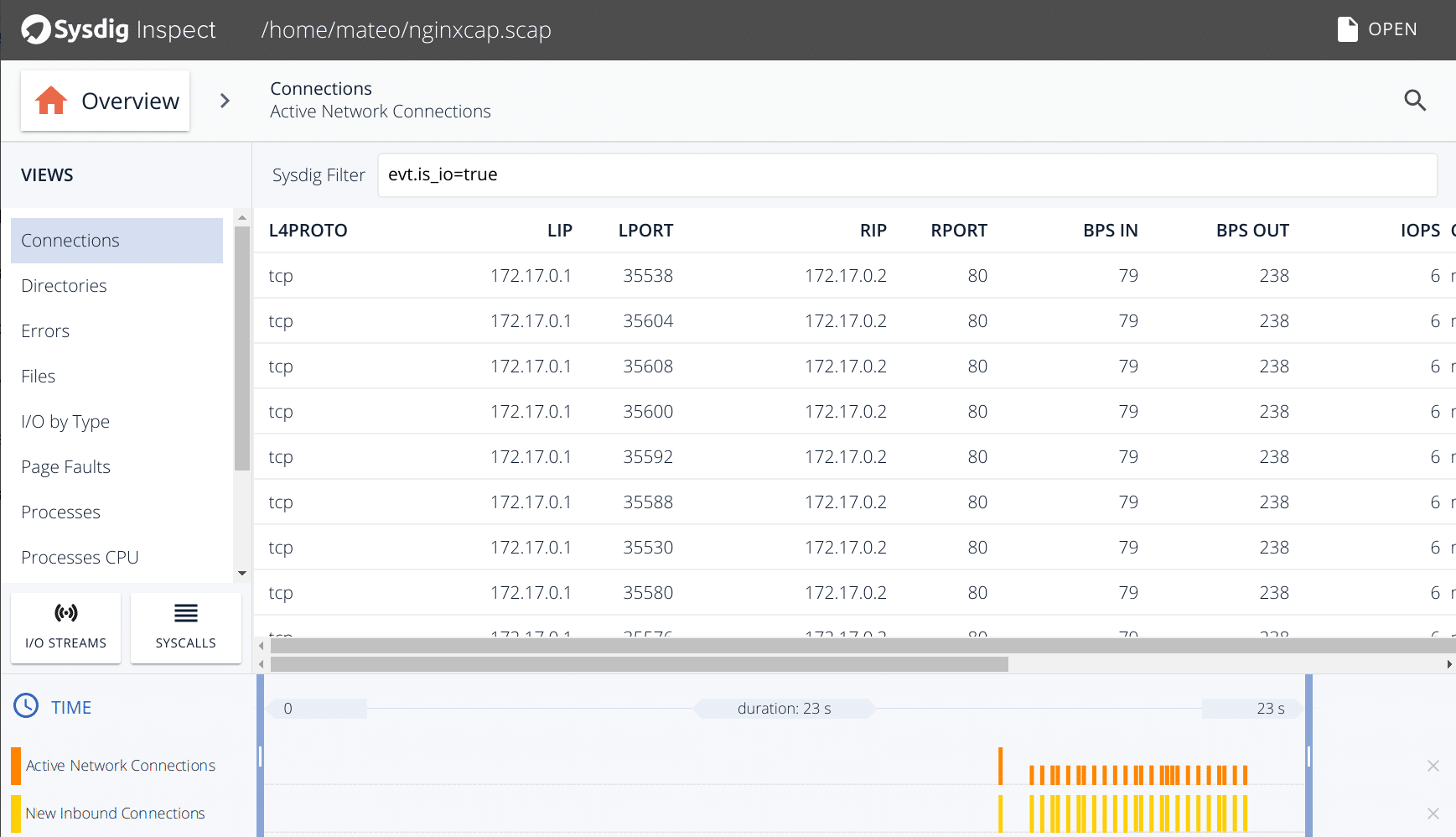
8. Sysdig Falco
Sysdig Falco is a container security monitor that is free and open-source, and it is designed to detect unusual activities in your applications. Falco allows you to continuously monitor and detect activities in your containers, applications, hosts, and networks. From a single location, using a single source of data, and using a single set of rules that may be customized.
Some functions of Sysdig Falco are:
- Sysdig’s Falco security auditing solution prioritises container, host, and network behavioral monitoring.
- Enable Falco to continually scan your infrastructure for issues, discover abnormalities, and inform you of any Linux system calls.
- The official guidelines direct people to run it through Docker.
- These are the commands that you will need to run to install it.
- Track the execution of containers’ shells, container mount points, and unplanned attempts to read sensitive files, go out on the network, or make other strange calls with Falco.
Pros:
- A completely free and open-source platform
- Consolidates all data in a single location
- Tracks container changes, access, and calls
Cons:
- Could use more data visualization features
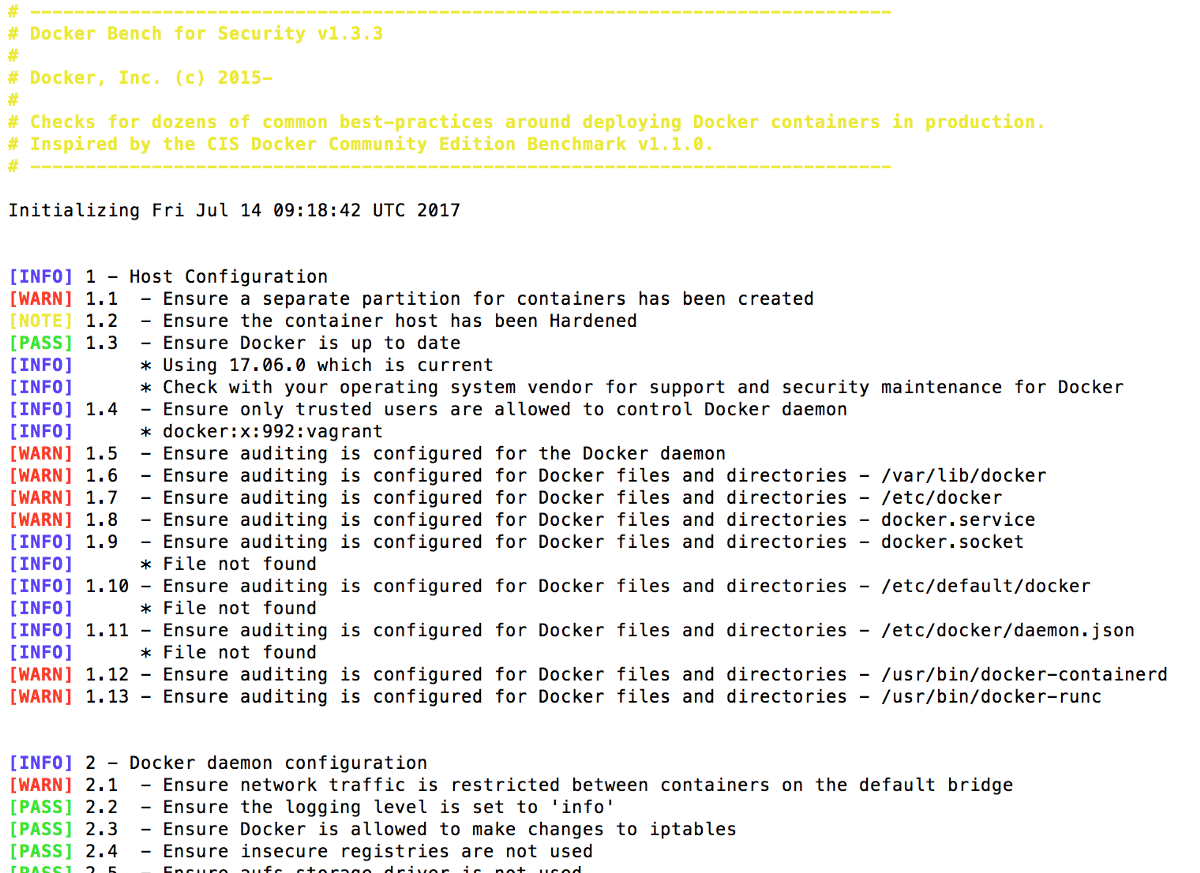
9. Docker Bench
Docker Bench for Security is an open-source script created by Docker to help developers perform audits of containers with Docker Community Edition to ensure the containers comply with standard security best practices. The tool is aimed at the developers who are running containers with Docker Community Edition. One disadvantage is that the output results are not machine-readable, which is a disadvantage. The Docker Bench package has been improved by a number of community packages, such as Docker Bench Test, drydock, and Actuary.
Features of Docker Bench include:
- Diogo Mónica, Docker’s security head, said it’s “a container that tests containers”.
- The findings are output in response logs to the current directory for each security setting benchmark.
- This tool is also available via Docker Compose or through running it directly on your host system.
- Docker Bench’s tests are based on the commonly used CIS benchmarks, which reduces the time used by the demanding manual procedure of vulnerability testing.
Pros:
- Open-source and transparent project
- Extremely lightweight
- Great for those looking for a CLI security tool
Cons:
- Lacks data visualization
Conclusion
No matter the tools you use, keep in mind to adhere to application security best practices throughout your development process to avoid making potentially costly mistakes afterwards. Containers have become standard practice for many organizations, and greater effort should be given to container security in light of that fact. The need for better container security becomes more important considering the many dangers that emerge as a container system evolves. When securing the container environment, organizations also defend themselves, their infrastructure, and their customers. Containers allow us to operate more quickly and efficiently, but it is still our responsibility to work with them securely. Now that you are aware that a container security scanner exists, there is no longer any justification. To learn how they can assist you in maintaining your containerized application safe and secure, feel free to investigate their services.
Container Security Tools FAQs
What are some common container security challenges?
Common container security challenges include securing container images and registries, managing access controls and authentication, monitoring container activity and performance, and integrating container security with other security and compliance tools.
What are some best practices for container security?
Best practices for container security include using trusted and verified container images, regularly patching and updating containers and underlying systems, implementing access controls and authentication measures, and regularly monitoring and reviewing container activity and performance.
What are some common types of container security tools?
Common types of container security tools include container image scanning tools, container runtime security tools, and container management and orchestration platforms.
How can container security be integrated with DevOps practices?
Container security can be integrated with DevOps practices by using tools and techniques such as infrastructure as code, continuous integration and delivery pipelines, and automated testing and deployment.
What are some popular container security tools?
Popular container security tools include Anchore, Aqua Security, Sysdig, and Twistlock.